(Helix)
{ Dump Window's Physical Memory to Netcat }
| Section 0. Background Information |
- Helix3 is a Live CD built on top of Ubuntu. It focuses on incident response and computer forensics. According to Helix3 Support Forum, e-fense is no longer planning on updating the free version of Helix.
- See http://www.e-fense.com/products.php
- In this lab, you will learn how to make a copy the memory of a Window Server's over the network to another server running netcat.
| Section 1. Pre-requisites |
| Section 2. Logging Into TargetHelix01 |
- Booting up Helix
- Instructions:
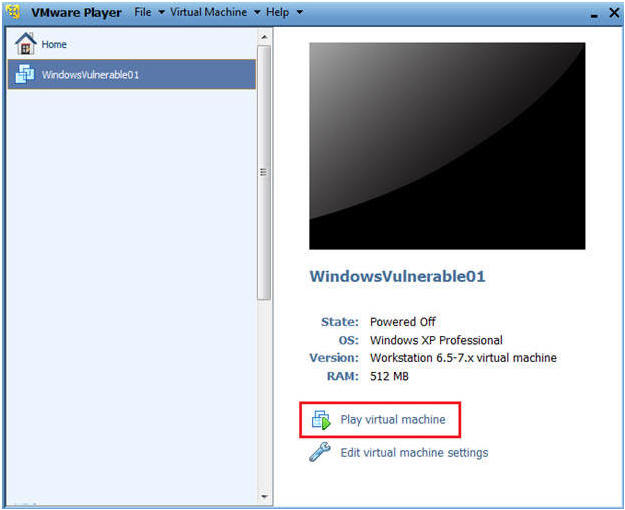
- Select TargetHelix01
- Play Virtual Machine
- Instructions:
- Logging into Helix
- Command:
- Login with your the username and password you created earlier.
- In my case, I create a username called "student".
- Command:
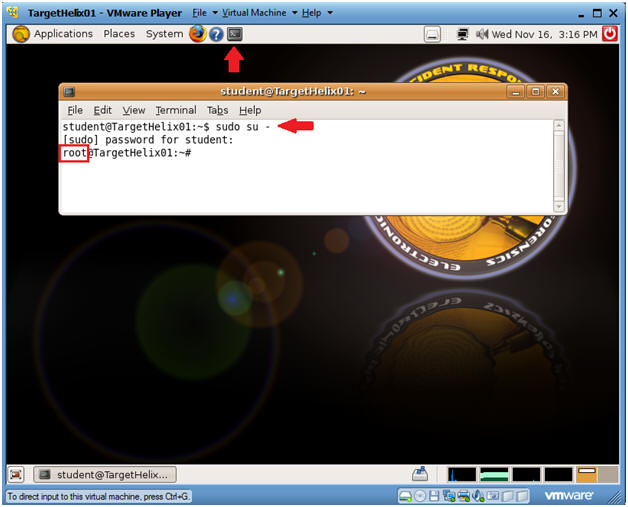
- How to become root
- Command:
- sudo su -
- Enter your current password for the account your logged in as.
- Command:
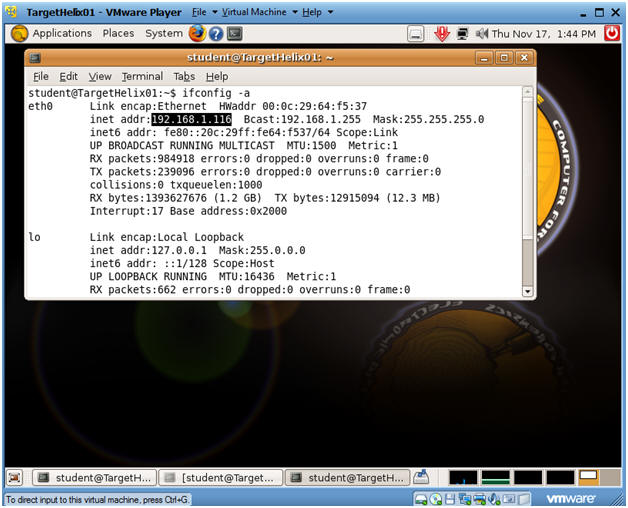
- Determine IP Address
- Command:
- ifconfig -a
- Note:
- In my case, my IP address is 192.168.1.116.
- You will use this IP address for your Netcat server.
- Command:
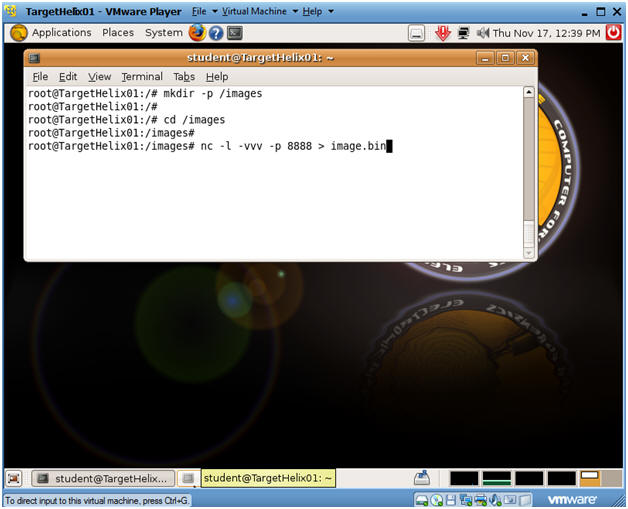
- Setting Up Netcat
- Command:
- mkdir -p /images
- cd /images
- nc -l -vvv -p 8888 > image.bin
- Command:
| Section 3. Logging Into TargetHelix01 |
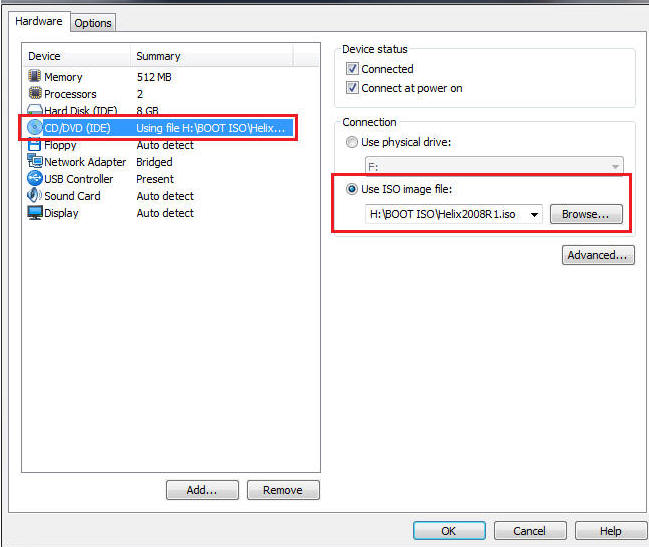
- Edit the WindowsVulnerable01 virtual machine.
(See Below)
- Note: For those of you that don't have access to class material, this can be Windows XP, 2000, 2003 and 7.
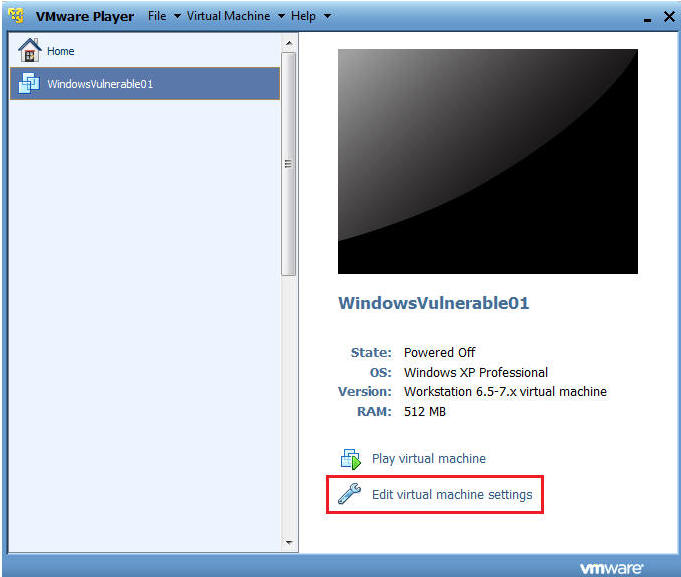
- Configure Windows to boot off of Helix
- Instructions:
- Select CD/DVD (IDE)
- Select the Use ISO image file
- Browse to where you saved the Helix iso.
- Note: In my case, I save it in the following location:
- H:\BOOT ISO\Helix2008R1.iso
- Instructions:
- Play the Virtual Machine
- Select Play Virtual Machine
- Booting from the ISO
- At the same time, Click the right mouse key and the press the ESC button, when the screen starts to change to the VMware screen below.
- Note: This might take you a few times so be patient!!!

- Boot Menu Selection
- Command:
- Select CD-ROW Drive
- Press Enter
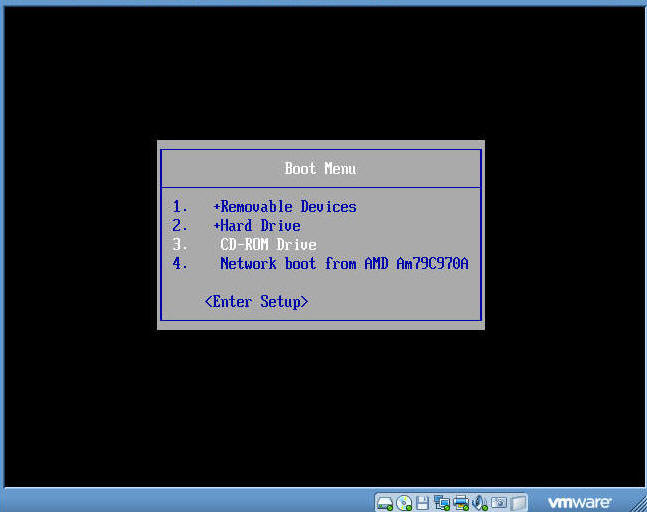
- Command:
- Booting from Helix Options
- Instructions:
- Boot into the Helix Live CD
- This will take you into a knoppix/linux operating systems.
- Unfortunately, VMware seems to not allow mouse clicks.
- In the future, I will experiment with VirtualBox to see if the same issue is present.
-
Boot from first hard disk
- Select this option.
- This will allow you to run the Helix CD from Windows.
- Boot into the Helix Live CD
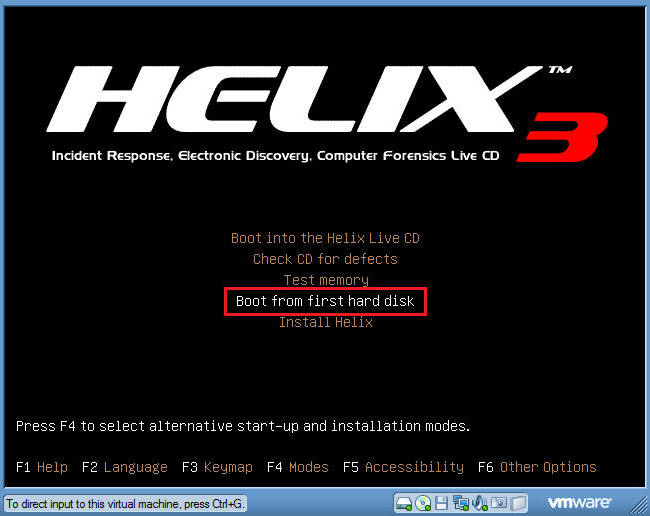
- Instructions:
- Log into your Windows Machine
- Instructions:
- Its probably a good idea to long in with an administrator account to ensure you can run the Helix CD.
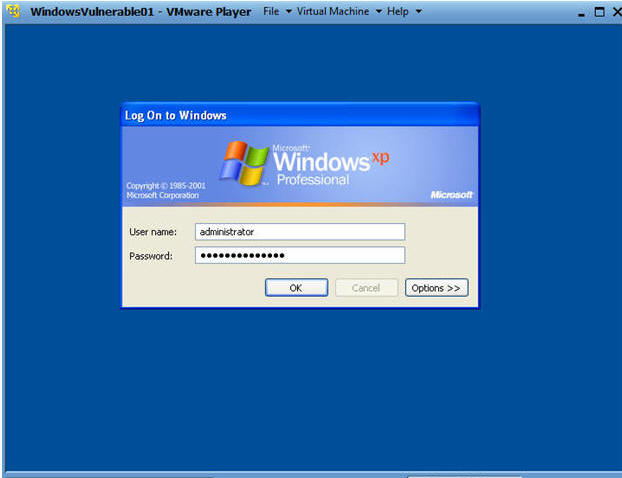
- Instructions:
| Section 4. Starting Helix and Acquire Image on WindowsVulnerable01 |
- Open Up My Computer
- Command: Start --> My Computer
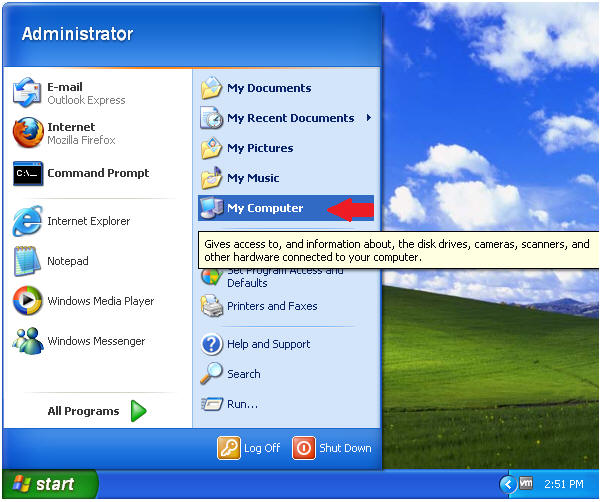
- Starting Up Helix
- Command:
- Right Click on Helix2008R1
- Click on AutoPlay
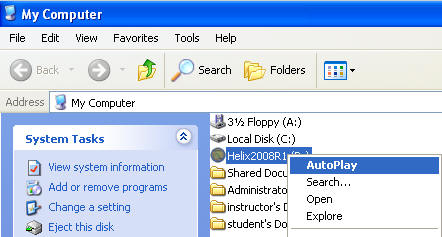
- Command:
- Select Language
- Command:
- Select English
- Click Accept
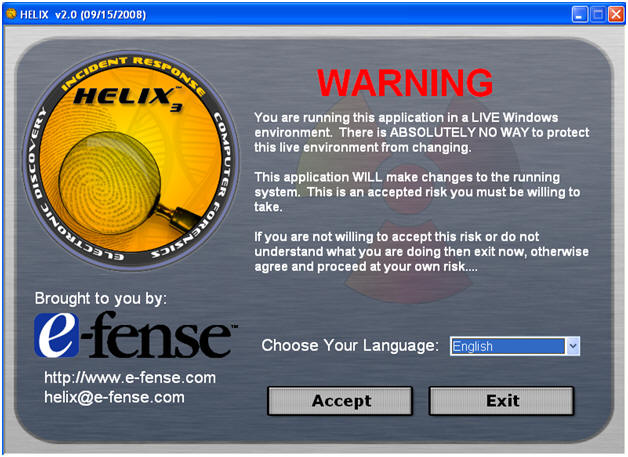
- Command:
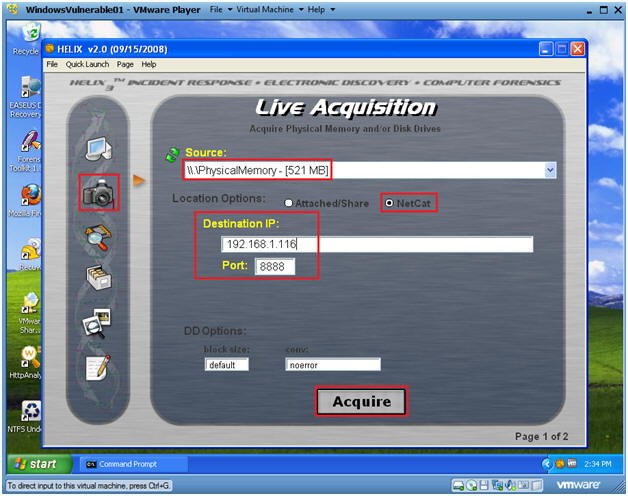
- Live Memory Acquisition
- Command:
- Click on the Camera
- Select \\Physical Memory
- You have the option of acquiring the entire disk as well.
- Location Options: Netcat
- Destination IP: 192.168.1.116
- Note: This is the IP Address of the Helix Server found in(Section 2, Step 4)
- Port: 8888
- Acquire
- Command:
- Notice
- Command: Yes
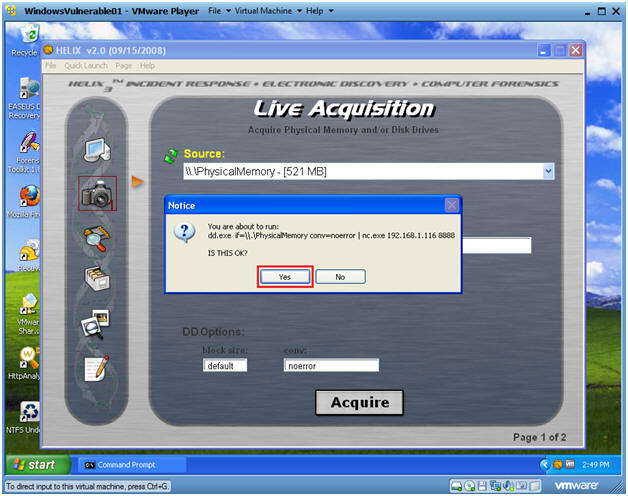
- So what is going on?
- Note:
- Your physical memory is now being copied to the Helix server.
- This will take between 5 to 10 minutes depending your system and network resources.
- Next Steps:
- Once the copy completes, the Black cmd.exe screen will close.
- Once the screen closes, then move on to the next section.
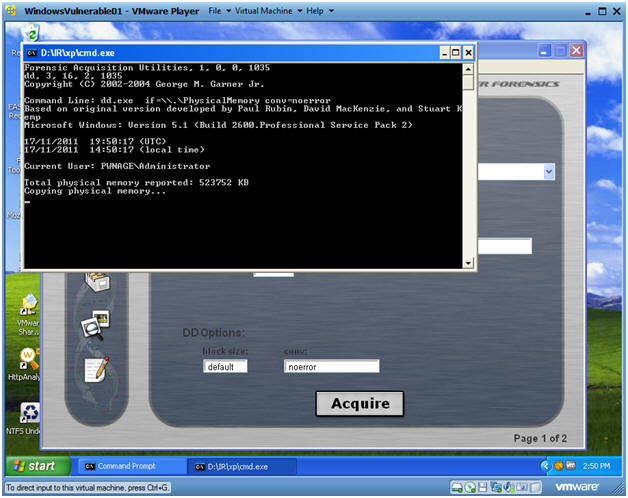
- Note:
| Section 5. Verifying Image Copy on the Helix Server |
- On your Helix Server
- Note: Once the copy completes on WindowsVulnerable01, you will see a similar received message "rcvd 536866816".
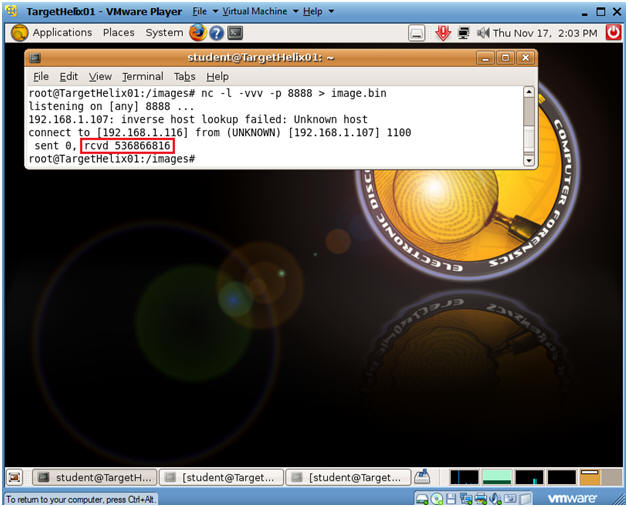
- Verifying your Image
- Proof of Lab
- Command:
- cd /images
- ls -lrta
- Do a Print Screen, Paste into a Word Document, Upload to Moodle.
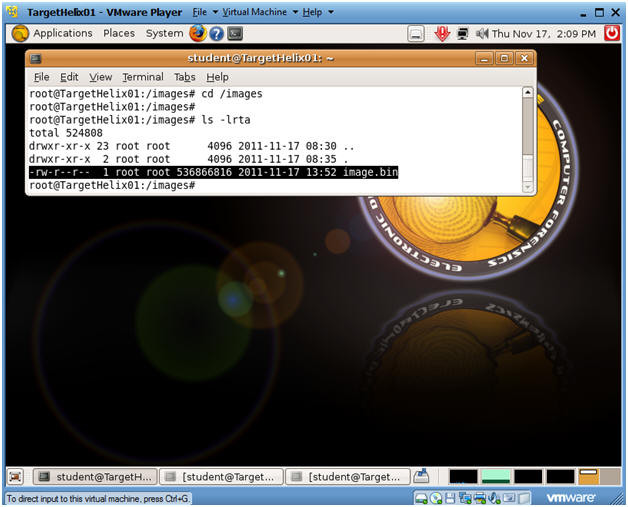
| Section: Proof of Lab |
- Cut and Paste a screen shot found in Section 5, Step 2 in a word and upload to Moodle.