(NESSUS: Lesson 3)
{ Scan with Nessus on BackTrack 5R1 }
| Section 0. Background Information |
- What is the purpose of this lesson?
- In the previous lessons you use NMAP to determine which services were running, using a methodology known as port scanning. This lesson will teach you how use Nessus to conduct a vulnerability assessment.
- What is NESSUS?
- Tenable Network Security provides enterprise-class solutions for continuous monitoring and visibility of vulnerabilities, configurations, user activity and system events that impact security and compliance.
- Nessus features high-speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture
- Pre-Requisite
-
Lab Notes
- In this lab we will do the following:
- Scan Damn Vulnerable WXP-SP2 with Nessus
- Product Nessus Report
- Save Nessus Report
- In this lab we will do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- You are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2013 No content replication of any kind is allowed without express written permission.
| Section 1: Login to BackTrack |
- Start Up VMWare Player
- Instructions:
- Click the Start Button
- Type Vmplayer in the search box
- Click on Vmplayer
- Instructions:
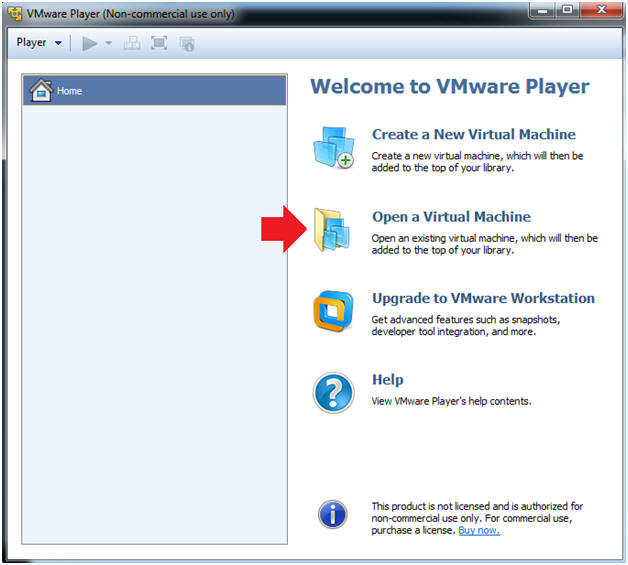
- Open a Virtual Machine
- Instructions:
- Click on Open a Virtual Machine
- Instructions:
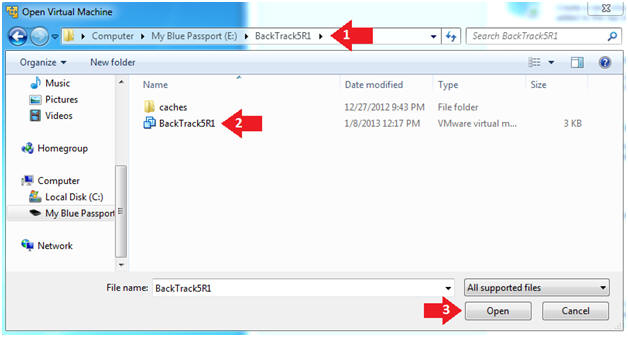
- Open the BackTrack5R1 VM
- Instructions:
- Navigate to where the BackTrack5R1 VM is located
- Click on on the BackTrack5R1 VM
- Click on the Open Button
- Instructions:
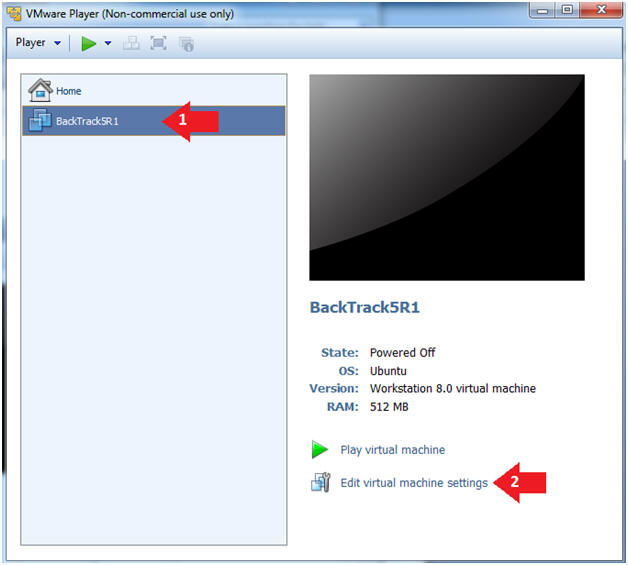
- Edit the BackTrack5R1 VM
- Instructions:
- Select BackTrack5R1 VM
- Click Edit virtual machine settings
- Instructions:
- Edit Virtual Machine Settings
- Instructions:
- Click on Network Adapter
- Click on the Bridged Radio button
- Click on the OK Button
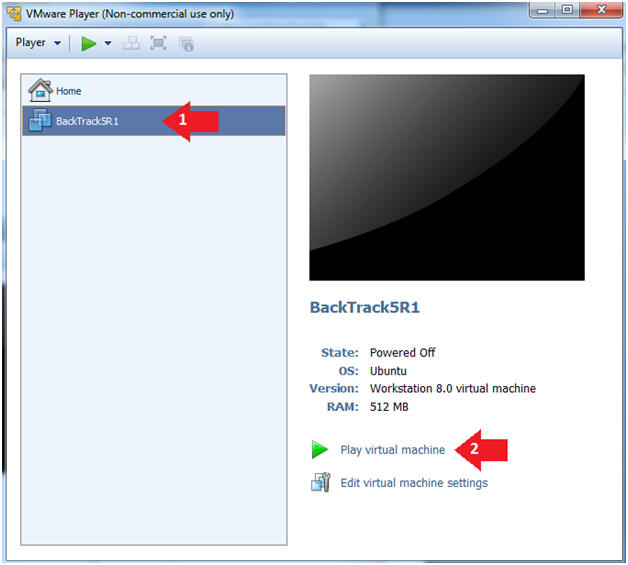
- Instructions:
- Play the BackTrack5R1 VM
- Instructions:
- Click on the BackTrack5R1 VM
- Click on Play virtual machine
- Instructions:
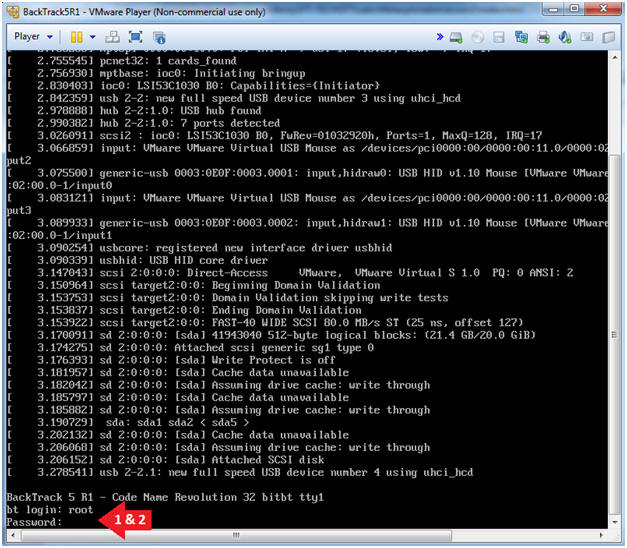
- Login to BackTrack
- Instructions:
- Login: root
- Password: toor or <whatever you changed it to>.
- Instructions:
- Bring up the GNOME
- Instructions:
- Type startx
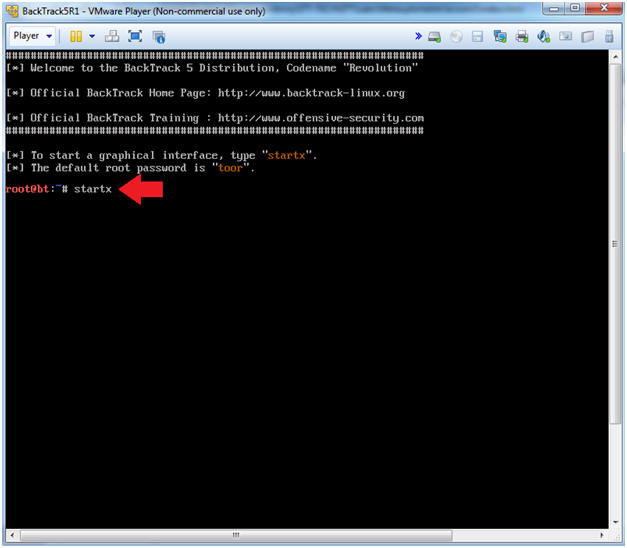
- Instructions:
| Section 2: Login to Damn Vulnerable WXP-SP2 (Victim Machine) |
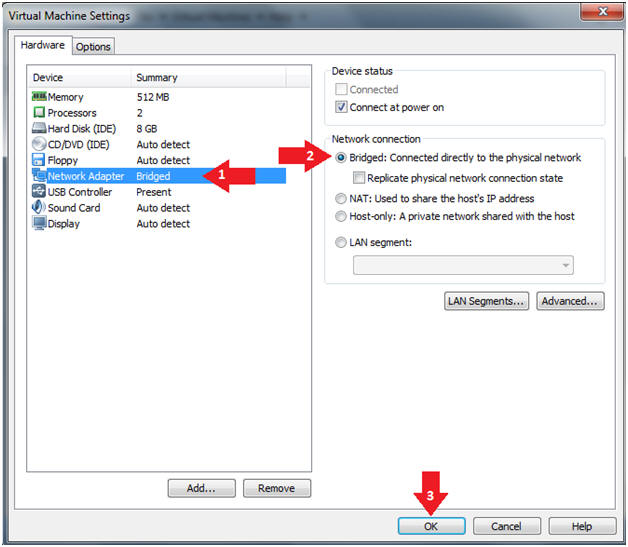
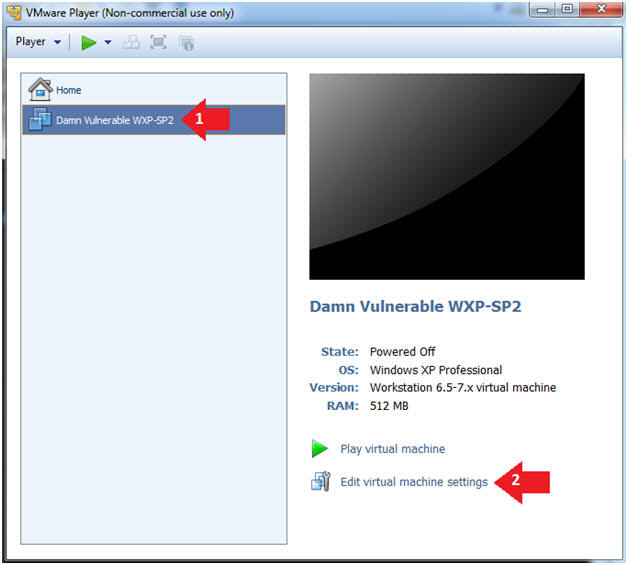
- Edit Virtual Machine Settings
- Instructions:
- Click on Damn Vulnerable WXP-SP2
- Edit Virtual Machine Settings
- Note:
- This VM is running Windows XP.
- This is the Victim Machine that we will be scanning with BackTrack5R1.
-
- Instructions:
- Set Network Adapter
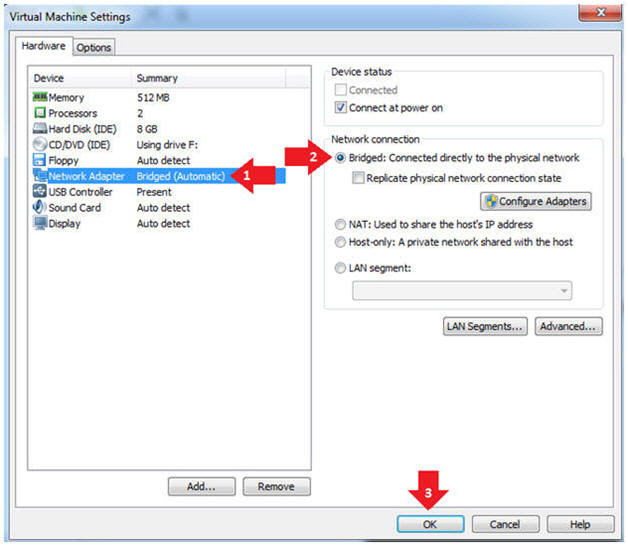
- Instructions:
- Click on Network Adapter
- Click on the radio button "Bridged: Connected directly to the physical network".
- Instructions:
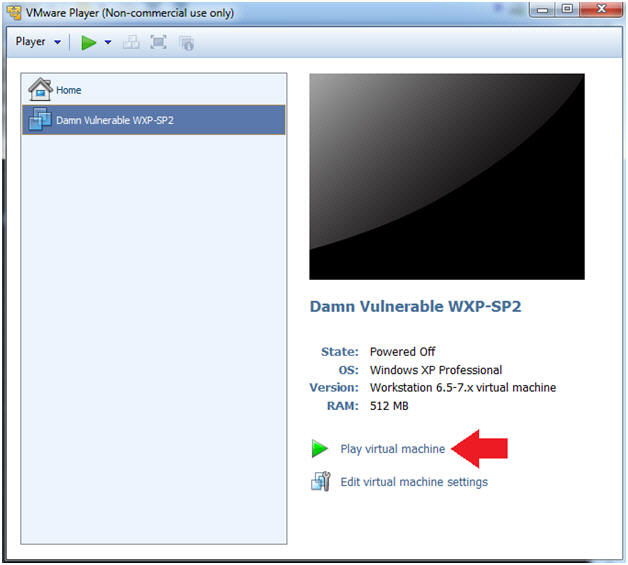
- Start Up Damn Vulnerable WXP-SP2.
- Instructions:
- Start Up your VMware Player
- Play virtual machine
- Instructions:
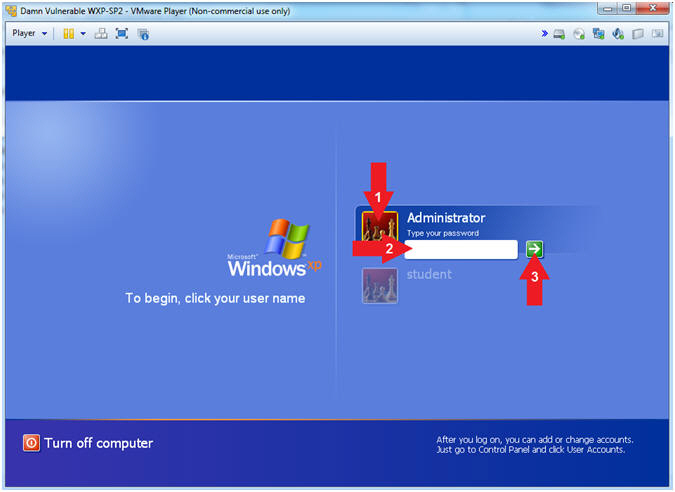
- Logging into Damn Vulnerable WXP-SP2.
- Instructions:
- Click Administrator
- Supply Your Password
- Click On

- Instructions:
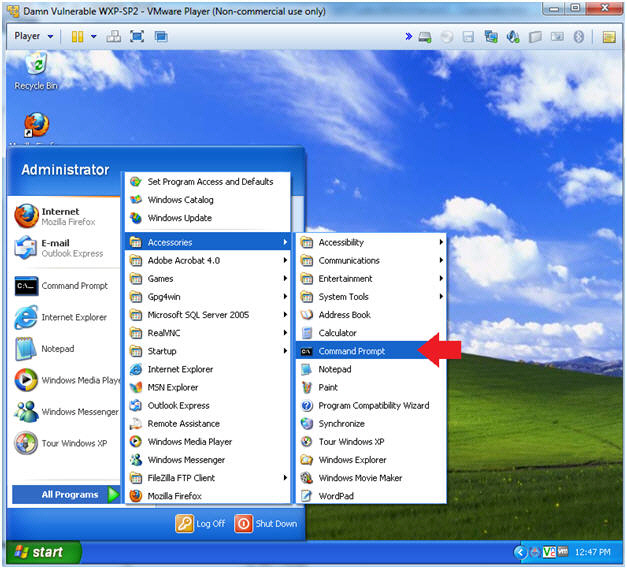
- Open a Command Prompt
- Instructions:
- Start --> All Programs --> Accessories --> Command Prompt
- Instructions:
- Obtain the IP Address
- Instructions:
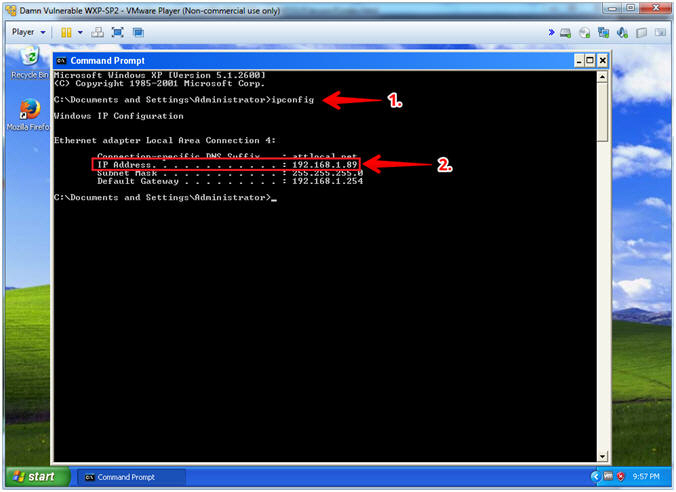
- ipconfig
- Record Your IP Address
- Note(FYI):
- #1, (ipconfig) displays all current TCP/IP network configuration values.
- #2, In my case, Damn Vulnerable WXP-SP2's IP Address 192.168.1.89.
-
- Instructions:
| Section 3: Bring up a console terminal |
- Start up a terminal window
- Instructions:
- Click on the Terminal Window
- Instructions:
- Obtain the IP Address
- Instructions:
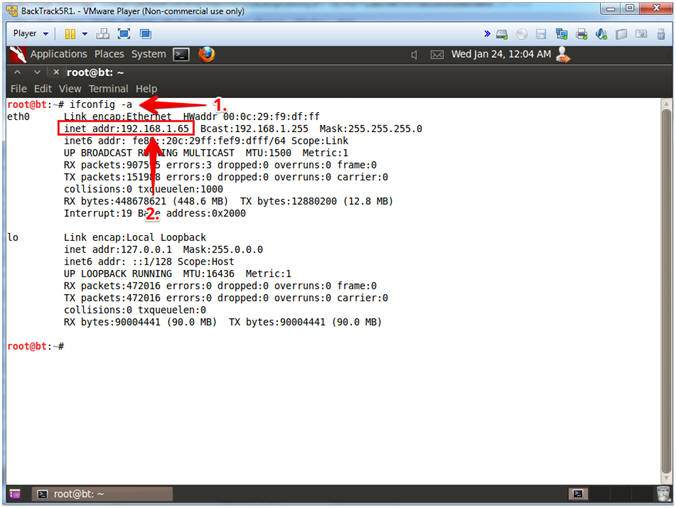
- ifconfig -a
- Record Your IP Address
- Note(FYI):
- #1, (ifconfig -a), display all interfaces which are currently available.
- #2, In my case, my IP address 192.168.1.65.
- Instructions:
| Section 4: Start the Nessus Service |
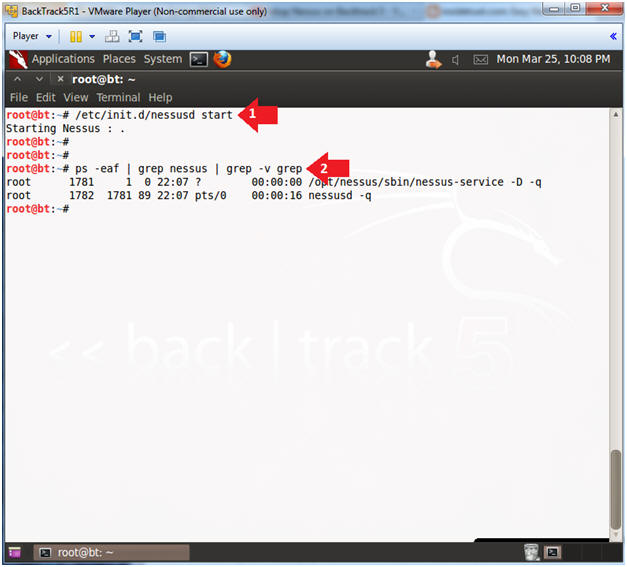
- Start Nessus Service
- Instructions:
- /etc/init.d/nessusd start
- ps -eaf | grep nessus | grep -v grep
- Note(FYI):
- /etc/init.d/nessusd, is the start up script for nessus.
- ps -eaf: Show me all processes
- | grep nessus: Only show me nessus processes.
- | grep -v grep: Do not show me the actual grep process.
- Instructions:
| Section 5: Login To Nessus |
- Start Firefox Instance
- Instructions:
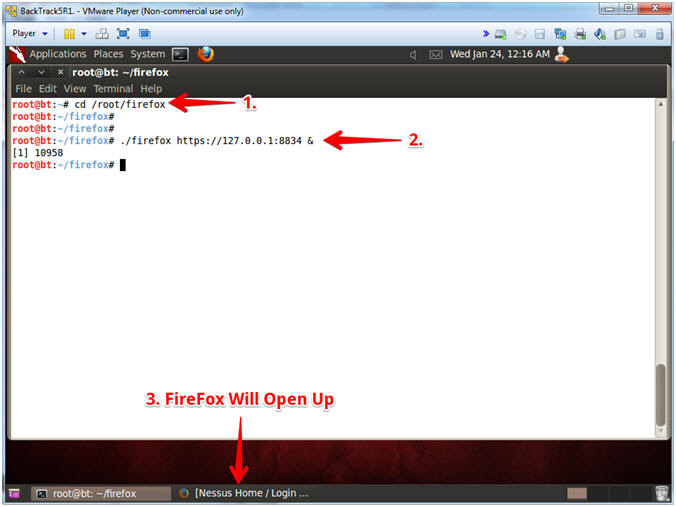
- cd /root/firefox/
- ./firefox https://127.0.0.1:8834 &
- Firefox will soon pop up.
- Note(FYI):
- We start Firefox this way, because this is our upgraded instance of Firefox that is compatible with the newest version of Nessus.
- Instructions:
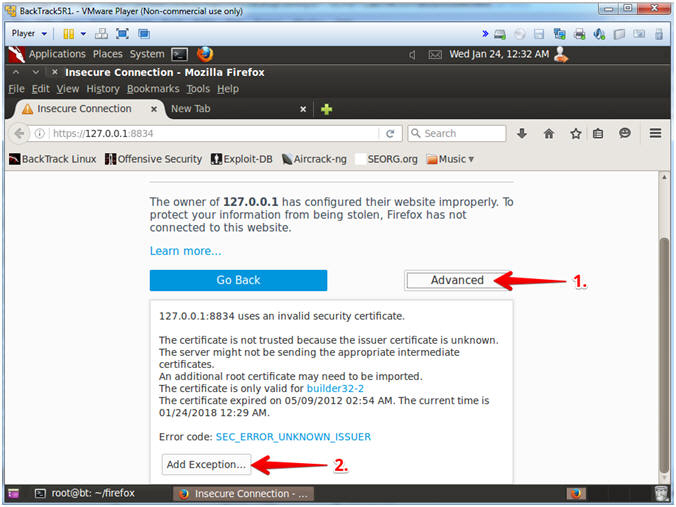
- Invalid Certificate Warning
- Instructions:
- Click the Advanced Button
- Click the Add Exception Button
- Note(FYI):
- You are receiving this message because Nessus uses a self-signed certificate that is required for the HTTPS protocol.
- In other circumstance, it is would be in your best interest to not proceed.
- Instructions:
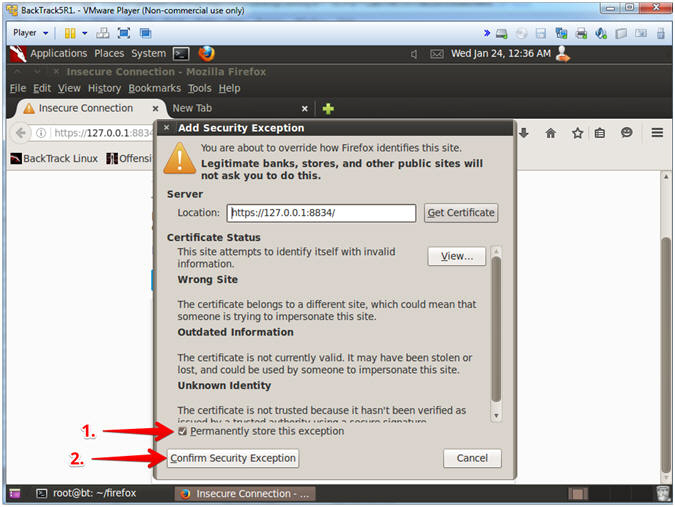
- Invalid Certificate Warning
- Instructions:
- Check the Permanently store this exception checkbox
- Click the Confirm Security Exception Button
- Instructions:
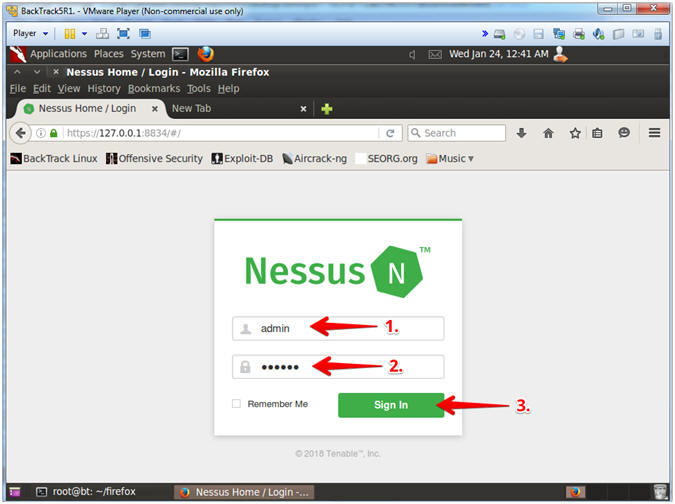
- Login To Nessus
- Instructions:
- Login: admin
- Password: Supply Password
- Click the Sign In Button
-
- Instructions:
| Section 6: Create Nessus Policy |
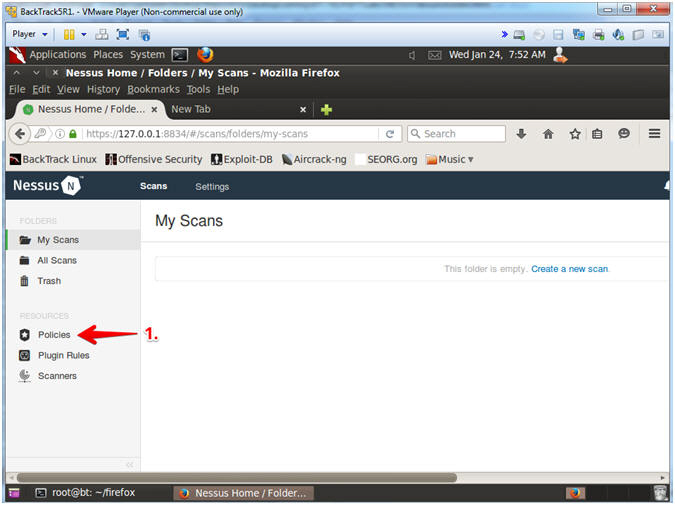
- Nessus Policies
- Instructions:
- Click on Policies
- Instructions:
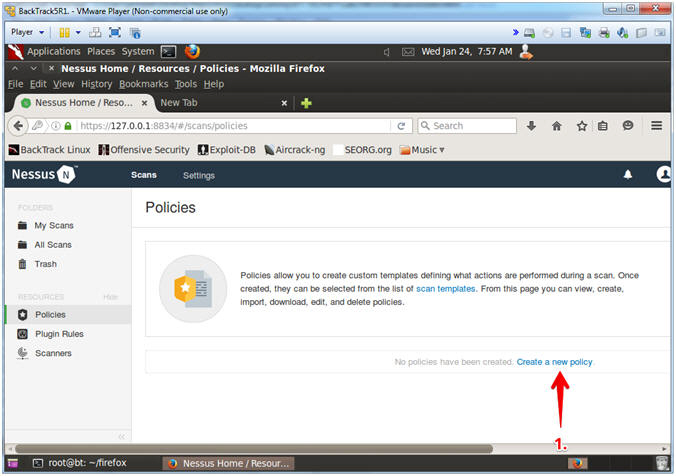
- Create Nessus Policies
- Instructions:
- Click on Create a new policy
- Instructions:
- Policy Wizards
- Instructions:
- Click on Basic Network Scan
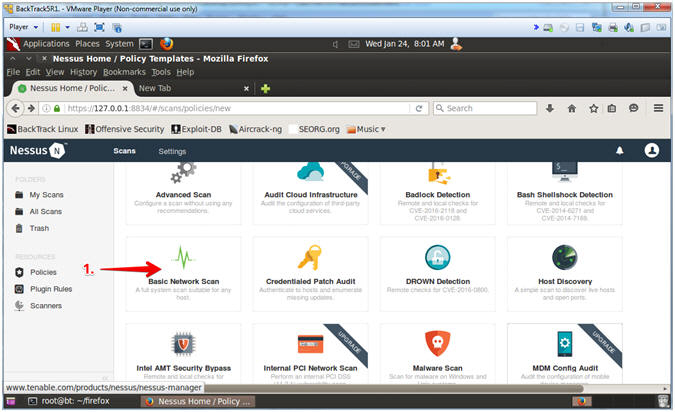
- Instructions:
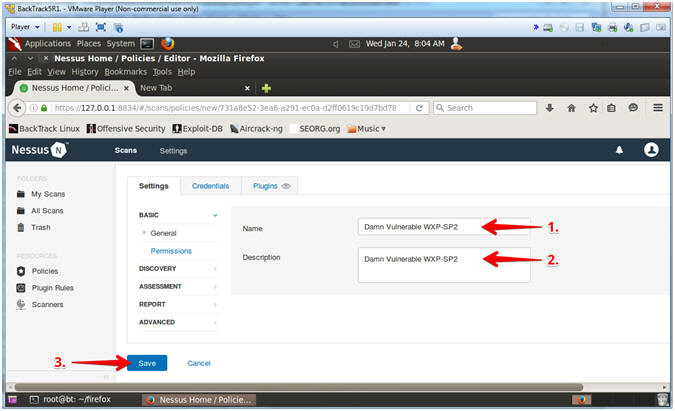
- New Basic Network Scan Policy
- Instructions:
- Policy Name: Damn Vulnerable WXP-SP2
- Description: Damn Vulnerable WXP-SP2
- Click the Save Button
- Instructions:
- View Saved Policy
- Note(FYI):
- After clicking the save button, you will see your newly saved policy.
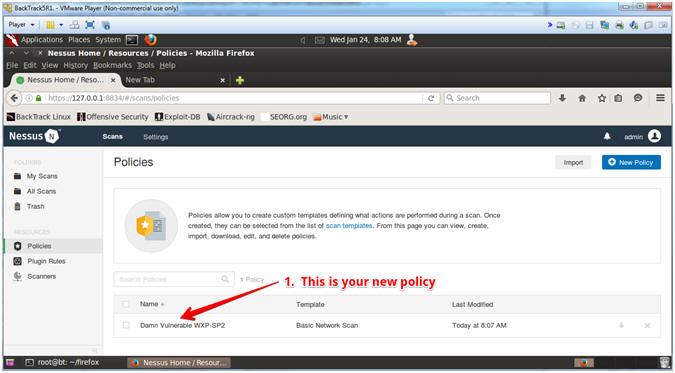
- Note(FYI):
| Section 7: Create Nessus Scan |
- Nessus Scans
- Instructions:
- Click on Scans
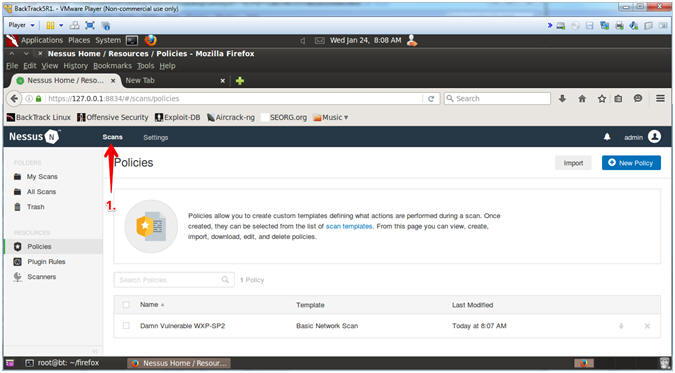
- Instructions:
- Create New Scan
- Instructions:
- Click on New Scan -or- Create a new scan
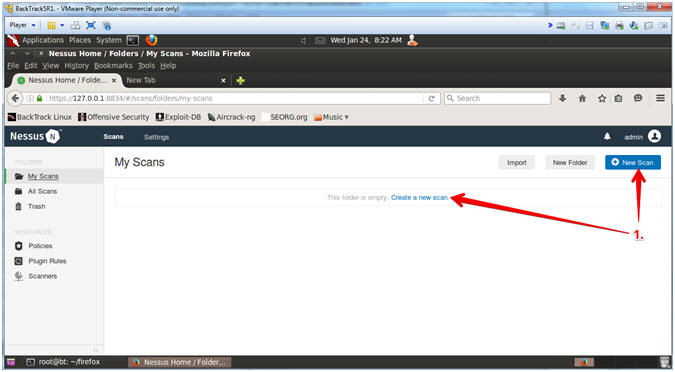
- Instructions:
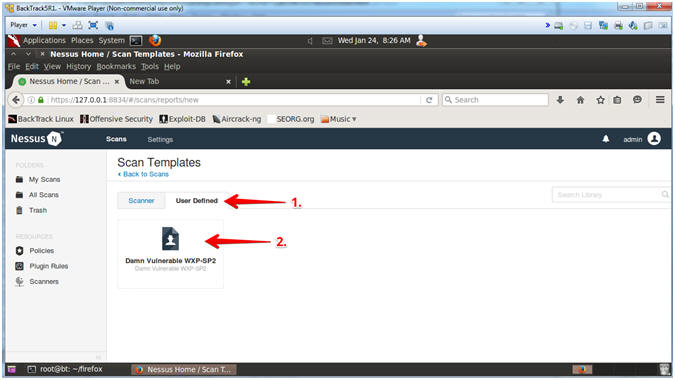
- User Defined Scan Templates
- Instructions:
- Click on the User Defined tab
- Click on the Damn Vulnerable WXP-SP2 Policy
- Instructions:
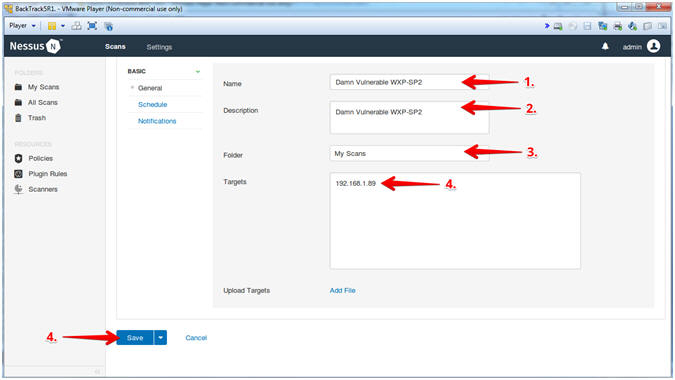
- Save Scan
- Note(FYI):
- Replace 192.168.1.89 with Damn Vulnerable WXP-SP2's IP Address obtained from (Section 2, Step 6).
- Instructions:
- Name: Damn Vulnerable WXP-SP2
- Description: Damn Vulnerable WXP-SP2
- Folder: My Scans
- Targets: 192.168.1.89
- Click the Save Button
- Note(FYI):
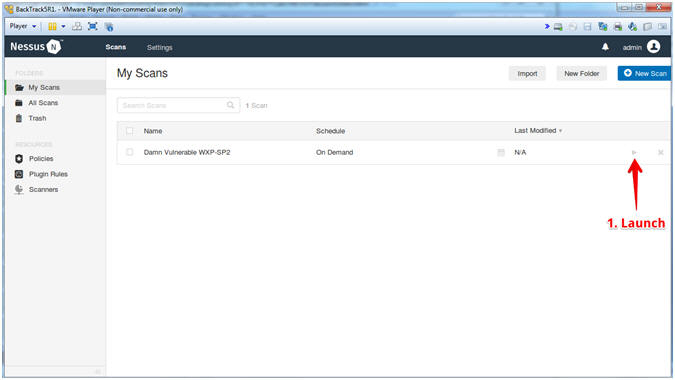
- Launch Scan
- Instructions:
- Click Launch Triangle
- Instructions:
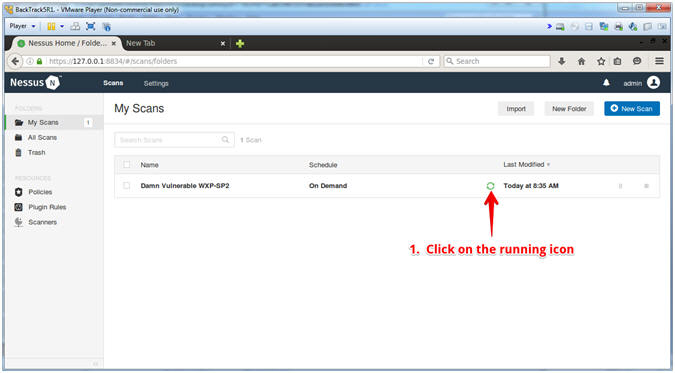
- View Running Scan
- Instructions:
-
Click the running icon
 to view the
active scan
to view the
active scan
-
Click the running icon
- Note(FYI):
- It
will take between 3 to 5 minutes for the running icon
 to turn into a
completed icon
to turn into a
completed icon  .
.
- It
will take between 3 to 5 minutes for the running icon
- Instructions:
- See Completed Scan
- Instructions:
-
Click on the grey check mark
 .
.
-
Click on the grey check mark
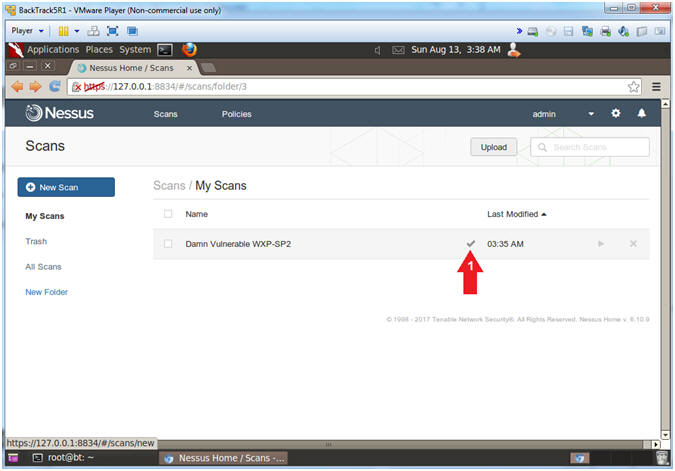
- Instructions:
| Section 8: View Nessus Results |
- View Vulnerabilities
- Instructions:
- Click on Vulnerabilities
- Notes(FYI):
- Red represents the highest vulnerabilities. Blue represents the lower vulnerabilities.
- You will see more vulnerabilities once you complete the following Hac-King-Do lessons: RealVNC, UltraVNC, and TFTPD32.
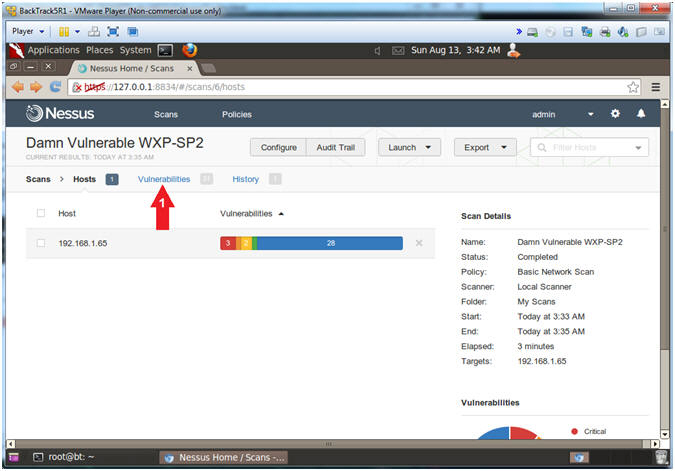
- Instructions:
- Viewing the Vulnerabilities
- Instructions:
- Click on the Vulnerabilities Tab
-
Notice the scan indicates how many vulnerabilities were found.
- In my case, there were 31.
- Notice the completed status.
- Click on MS08-067
- Note(FYI):
- A pen tester will have a big smile on their face, if MS08-067 shows up on the radar.
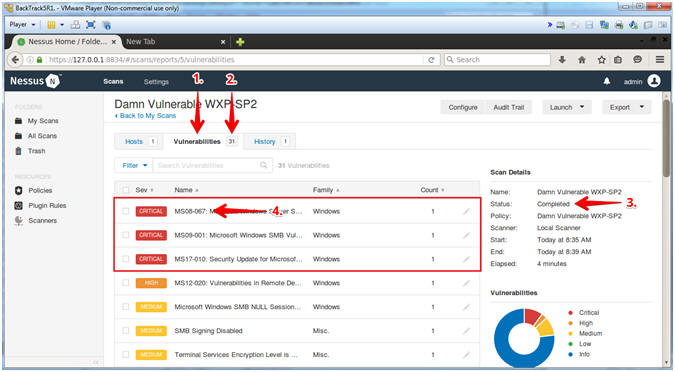
- Instructions:
- MS08-067 (Description, Solution)
- Instructions:
- Read the Description
- Read the Solution
- Scroll Down
- Note(FYI):
- #2, Notice this affects not only XP, but also W2K, W2K3, Vista and W2K8.
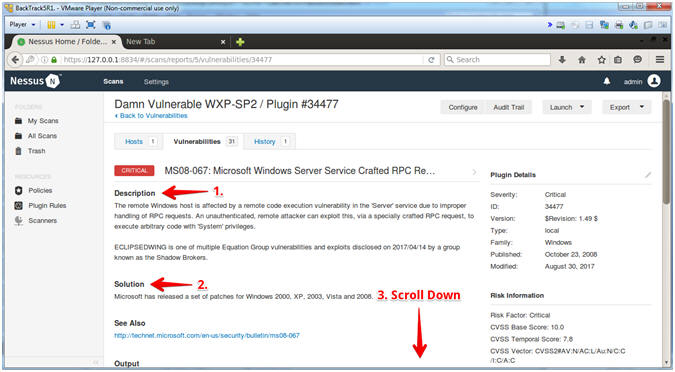
- Instructions:
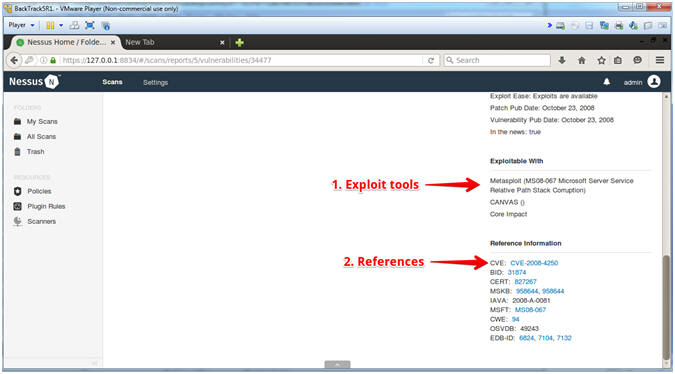
- MS08-067 (Exploit Tools and Reference Information)
- Instructions:
- Exploitable With: These are the tools that can exploit the vulnerability.
- Reference Information: Click on these links if you with to learn more able the exploit.
- Instructions:
| Section 9: Save Nessus Report |
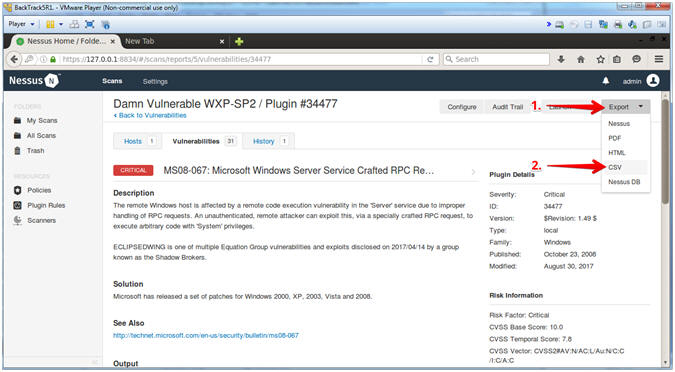
- Produce Report
- Instructions:
- Click on Export Drop Down Menu
- Click on CSV
- The Report will be downloaded and saved
- Instructions:
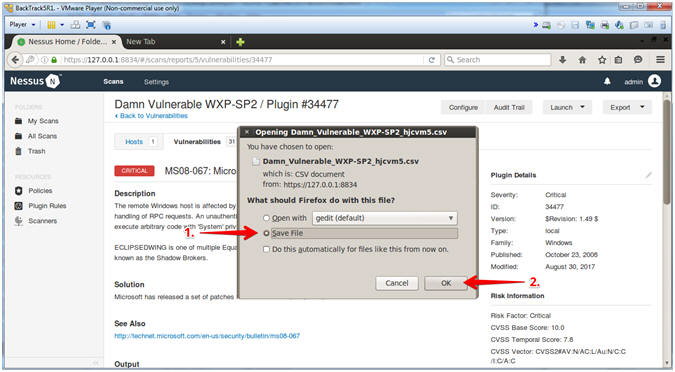
- Save Report
- Instructions:
- Select the Save File radio button
- Click on OK button
- Instructions:
| Section 10: Proof of Lab |
- Start up a terminal window
- Instructions:
- Click on the Terminal Window
- Instructions:
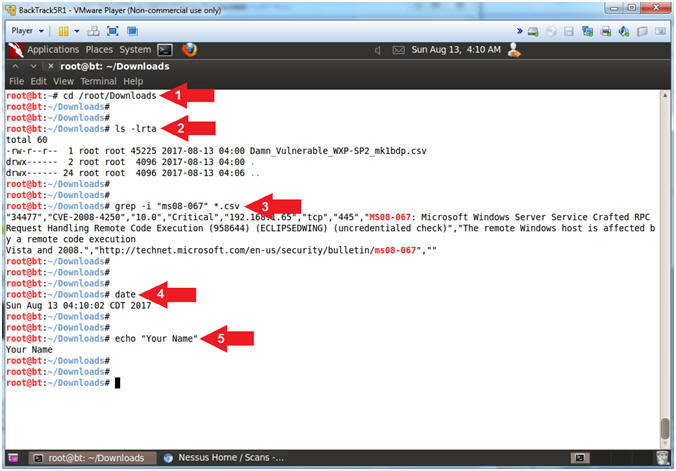
- Proof of Lab
- Instructions
- cd /root/Downloads
- ls -lrta
- grep -i "ms08-067" *.csv
- date
- echo "Your Name"
- Put in your actual name in place of "Your Name"
- e.g., echo "John Gray"
-
Proof Of Lab Instructions:
- Press the PrtScn key
- Paste into a word document
- Upload to Moodle
- Instructions