(Damn Vulnerable Windows XP: Lesson 8)
{ How to install OllyDbg v1.10 x86 Debugger }
| Section 0. Background Information |
- What is Damn Vulnerable Windows XP?
- This is a Windows XP Virtual Machine that provides a practice environment to conduct ethical penetration testing, vulnerability assessment, exploitation and forensics investigation.
- The Microsoft Software License Terms for the IE VMs are included in the release notes.
- By downloading and using this software, you agree to these license terms.
- What is
OllyDbg v1.10 x86 Debugger?
- OllyDbg (named after its author, Oleh Yuschuk) is an x86 debugger that emphasizes binary code analysis, which is useful when source code is not available. It traces registers, recognizes procedures, API calls, switches, tables, constants and strings, as well as locates routines from object files and libraries.
- OllyDbg is often used for reverse engineering of programs. It is often used by crackers to crack software made by other developers. For cracking and reverse engineering, it is often the primary tool because of its ease of use and availability; any 32-bit executable can be used by the debugger and edited in bitcode/assembly in realtime. It is also useful for programmers to ensure that their program is running as intended, and for malware analysis purposes.
- OllyDbg v1.10
x86 Debugger
License Agreement
- By using the OllyDbg Software, you agree to all of the terms and conditions provided in the following URL. (http://www.ollydbg.de/download.htm)
- Pre-Requisite
- Lesson Purpose
- This is a Pre-Requisite Lesson that will be used to illustrate future buffer overflow analysis.
-
Lab Notes
- In this lab we will do the following:
- Download OllyDbg v1.10 x86 Debugger
- Install OllyDbg v1.10 x86 Debugger
- In this lab we will do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- You are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2016 No content replication of any kind is allowed without express written permission.
| Section 1: Log into Damn Vulnerable WXP-SP2 |
- Open VMware Player on your windows machine.
- Instructions:
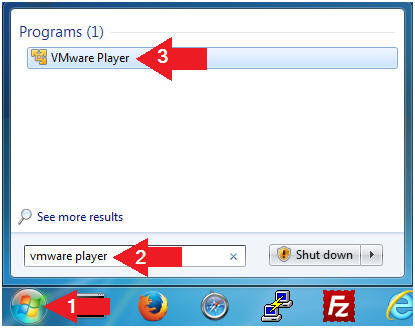
- Click the Start Button
- Type "vmware player" in the search box
- Click on VMware Player
- Instructions:
- Edit Virtual Machine Settings
- Instructions:
- Click on Damn Vulnerable WXP-SP2
- Edit Virtual Machine Settings
- Note:
- Before beginning a lesson it is necessary to check the following VM settings.
- Instructions:
- Set Network Adapter
- Instructions:
- Click on Network Adapter
- Click on the radio button "Bridged: Connected directly to the physical network".
- Click the OK Button
- Instructions:
- Start Up Damn Vulnerable WXP-SP2.
- Instructions:
- Start Up your VMware Player
- Play virtual machine
- Instructions:
- Logging into Damn Vulnerable WXP-SP2.
- Instructions:
- Click on Administrator
- Password: Supply Password
- (See Note)
- Press <Enter> or Click the Arrow
- Note(FYI):
- Password was created in (Lab 1, Section 1, Step 8)
- Instructions:
- Open the Command Prompt
- Instructions:
- Click the Start Button
- All Programs --> Accessories --> Command Prompt
- Instructions:
- Obtain Damn Vulnerable WXP-SP2's IP Address
- Instructions:
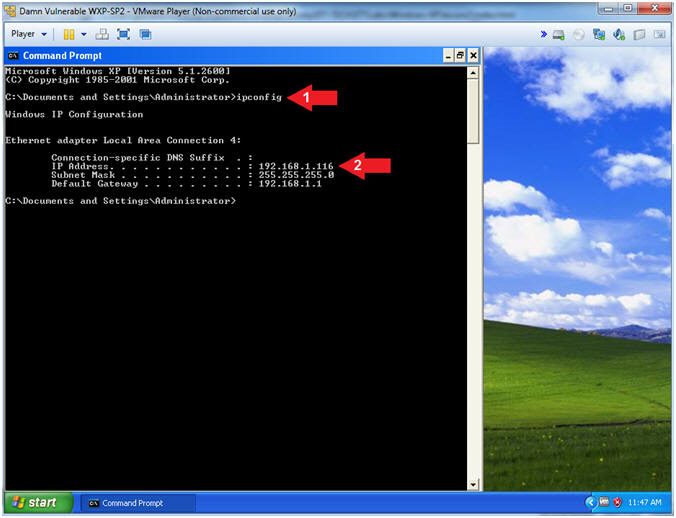
- ipconfig
- Record Your IP Address
- Note(FYI):
- In my case, Damn Vulnerable WXP-SP2's IP Address 192.168.1.116.
- This is the IP Address of the Victim Machine.
- Instructions:
| Section 2: Install OllyDbg v1.10 x86 |
- Open Firefox
- Instructions:
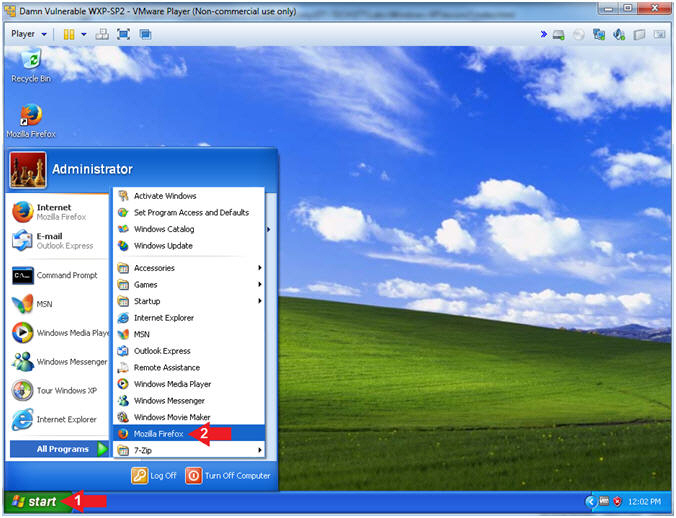
- Click the Start Button
- All Programs --> Mozilla Firefox
- Instructions:
- Download OllyDbg 1.10
- Instructions:
- Navigate to the following
URL
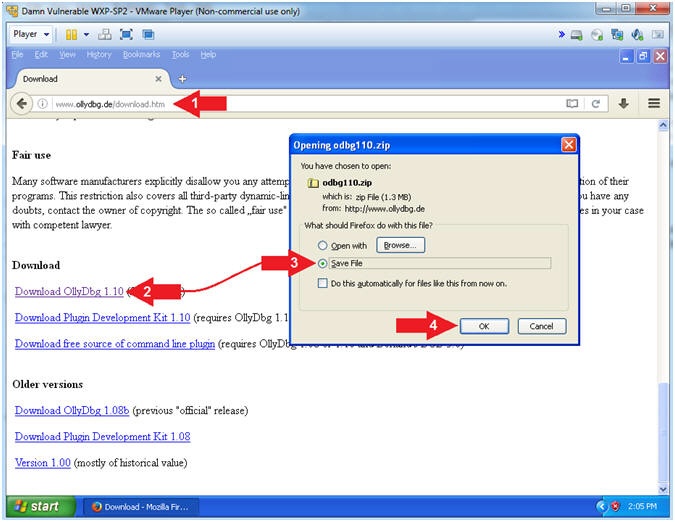
- http://www.ollydbg.de/download.htm
- Click on Download OllyDbg 1.10
- Click on Save File Radio Button
- Click the OK Button
- Navigate to the following
URL
- Instructions:
- Open Downloads Folder (Part 1)
- Instructions:
- Tools --> Downlaods
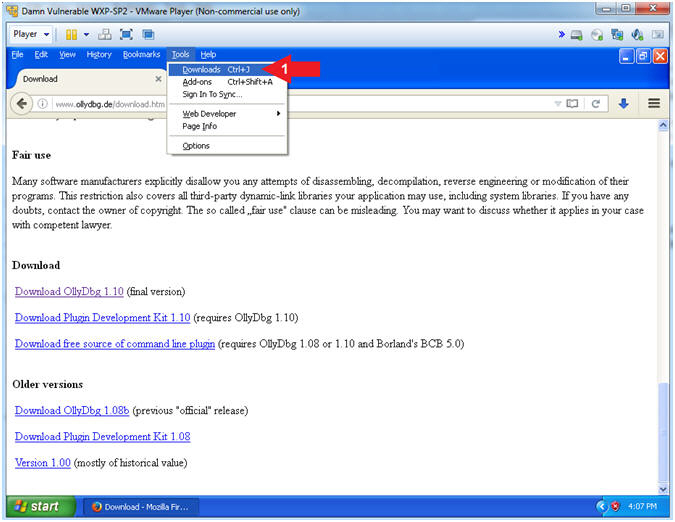
- Instructions:
- Open Downloads Folder (Part 2)
- Instructions:
- Right Click on odbg110.zip
- Click on Open Containing Folder
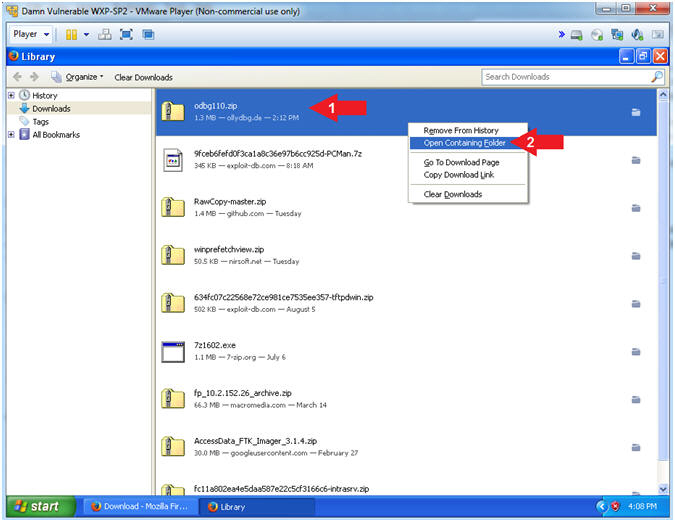
- Instructions:
- Extract the odbg110 file
- Instructions:
- Right Click on odbg110
- Touch 7-Zip
- Click on Extract to odbg110\
- Instructions:
- Open the oddbg110 folder
- Instructions:
- Right on the odbg110 folder
- Select Open
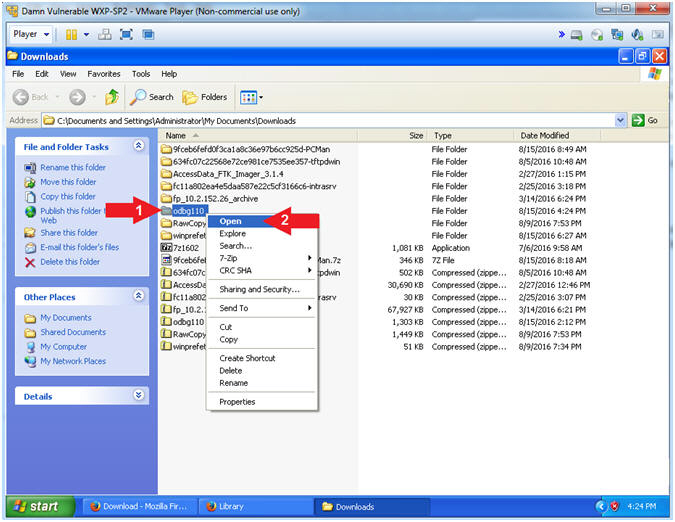
- Instructions:
- Create a OLLDBG Desktop Icon
- Instructions:
- Right on OLLDBG
- Touch Send To
- Select Desktop (create shortcut)
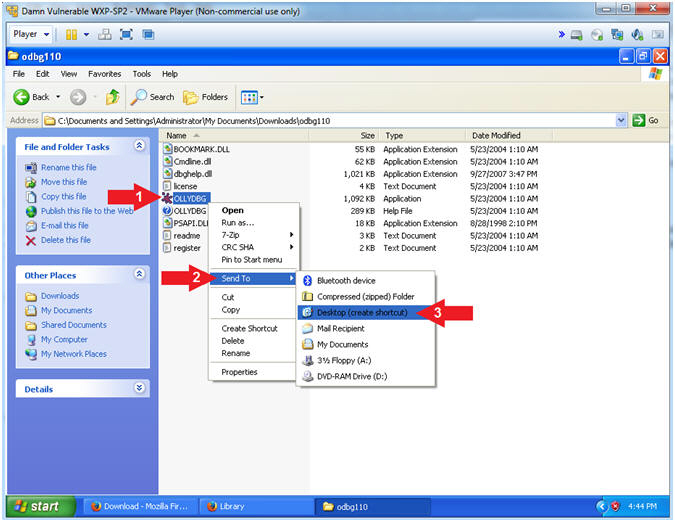
- Instructions:
- Show Desktop
- Instructions:
- Right Click on Blue Taskbar
- Select Show the Desktop
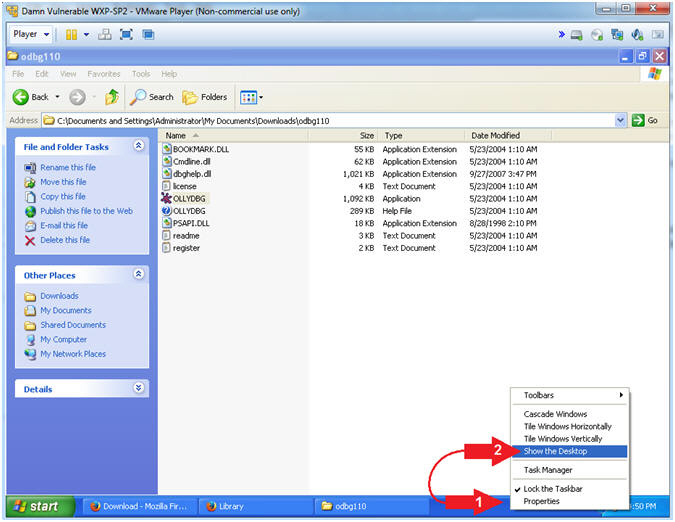
- Instructions:
- Run OLLYDBG
- Instructions:
- Right Click on the OLLYDBG Desktop Icon
- Select Open
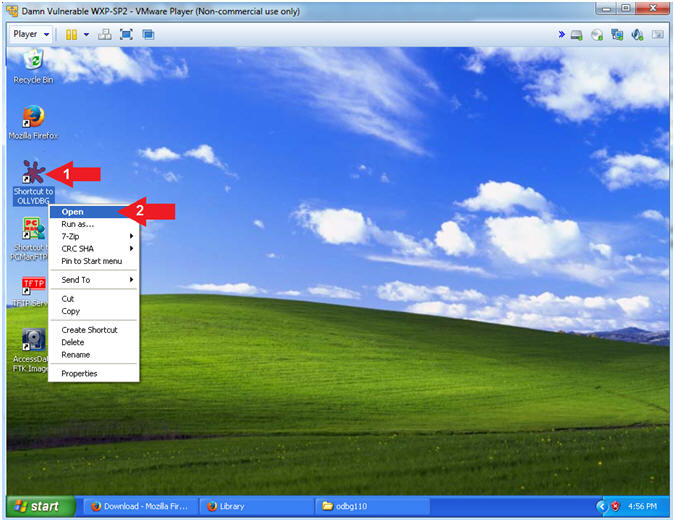
- Instructions:
- Old DLL
- Instructions:
- Select the No Button
- Note(FYI):
- You can select either Yes or No here. Selecting No did not appear to have any bearing on debugging analysis of the buffer overflow lessons.
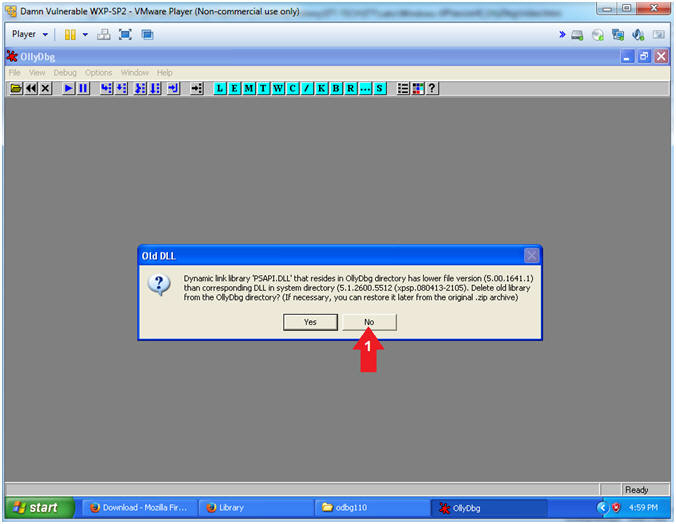
- Instructions:
| Section 4: Configure OllyDbg Font Appearance |
- Configuration Appearance (Part 1)
- Instructions:
- Options --> Appearance
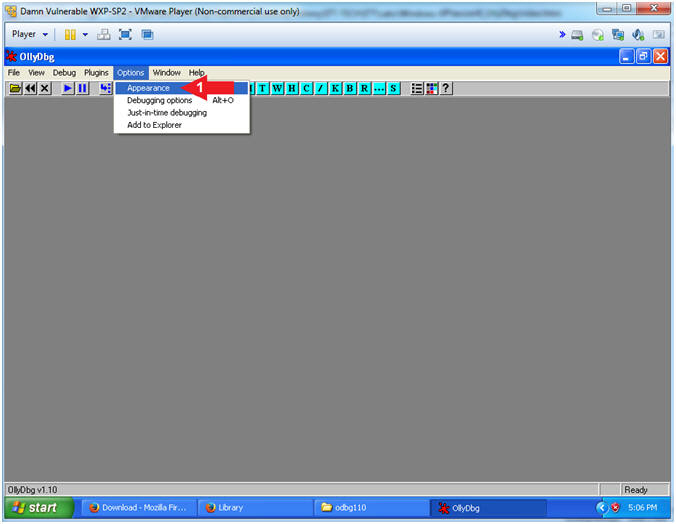
- Instructions:
- Configuration Appearance (Part 2)
- Instructions:
- Click the Change Button
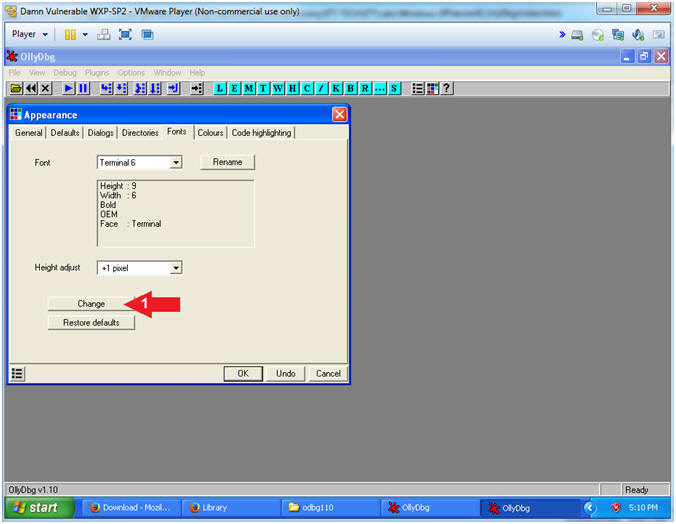
- Instructions:
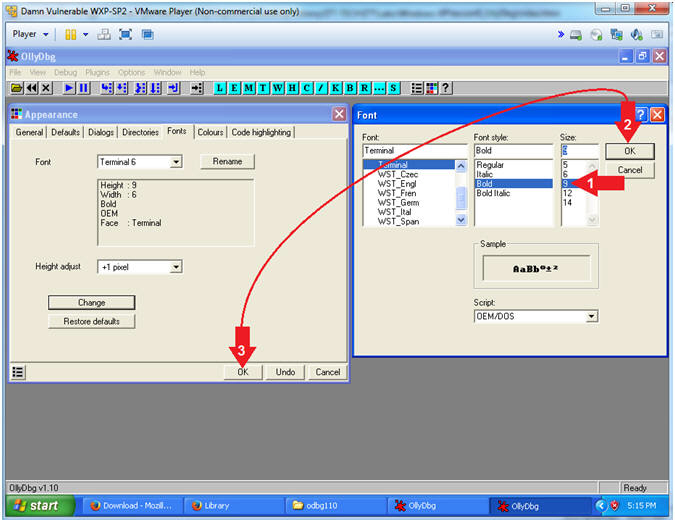
- Configuration Font
- Instructions:
- Select 9 Font Size
- Click the OK Button in the Font Window
- Click the OK Button in the Appearance Window
- Note(FYI):
- This is necessary unless you have really exceptional vision.
- Do not close OllyDbg
- Instructions:
| Section 5: Proof of Lab |
- Open the Command Prompt
- Instructions:
- Click the Start Button
- All Programs --> Accessories --> Command Prompt
- Instructions:
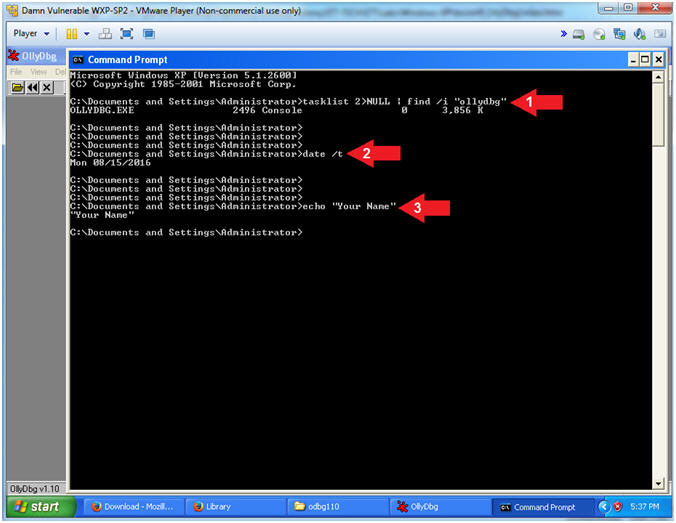
- Proof of Lab
- Instructions:
- tasklist 2>NULL| find /i "ollydbg"
- date /t
- echo "Your Name"
- Put in your actual name in place of "Your Name"
- e.g., echo "John Gray"
- Note(FYI):
- Command #1, Use (tasklist) to show all the running processes. Use (find) and ignore case (/i) to display only the processes that contain the string (ollydbg).
-
Proof of Lab
Instructions
- Press the <Ctrl> and <Alt> key at the same time.
- Press the <PrtScn> key.
- Paste into a word document
- Upload to Moodle
- Instructions:





