(Kali:
Lesson 3)
{ Install brutessh.py }
|
Section 0. Background
Information |
- Background information.
- The goal of the lesson is to show you how
to install brutessh.py and all of it's prerequisites.
- What is brutessh.py
- Brutessh is a program that uses the
paramiko ssh library, to launch bruteforce passwords attacks against the sshd
service. The tools is multithreaded and can use a dictionary password
lists.
- What is python-crypto
- This is a collection of both secure
hash functions (such as SHA256 and RIPEMD160), and various
encryption algorithms (AES, DES, RSA, ElGamal, etc.)
- What is python-paramiko
- Paramiko is a Python implementation of
the SSHv2 protocol, providing both client and server functionality.
Paramiko itself is a pure Python interface around SSH networking
concepts.
- Prerequisite
-
Lab Notes
- In this lab we will do the following:
- We will install python-crypto.
- We will install python-paramiko
- We will install python-paramiko
- We will use John the Ripper to create a
small password list
- Legal Disclaimer
- As a condition of your use of this Web
site, you warrant to computersecuritystudent.com that you will not use
this Web site for any purpose that is unlawful or
that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this
product is provided with "no warranties, either express or implied." The
information contained is provided "as-is", with "no guarantee of
merchantability."
- In addition, this is a teaching website
that does not condone malicious behavior of
any kind.
- You are on notice, that continuing
and/or using this lab outside your "own" test environment
is considered malicious and is against the law.
- © 2015 No content replication of any kind
is allowed without express written permission.
- Start VMware Player
- Instructions
- For Windows 7
- Start --> All Programs --> VMware
Player
- For Windows XP
- Starts --> Programs --> VMware
Player
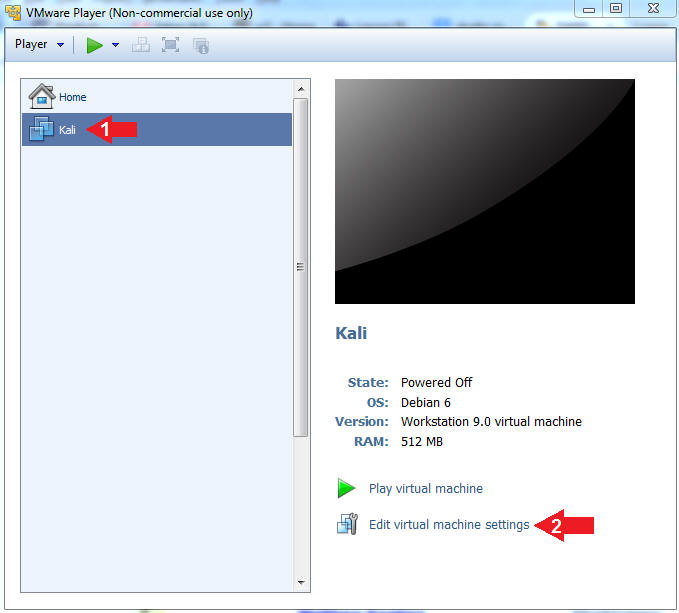
- Edit Virtual Machine Settings
- Instructions:
- Click on the Kali VM
- Click on Edit virtual machine settings
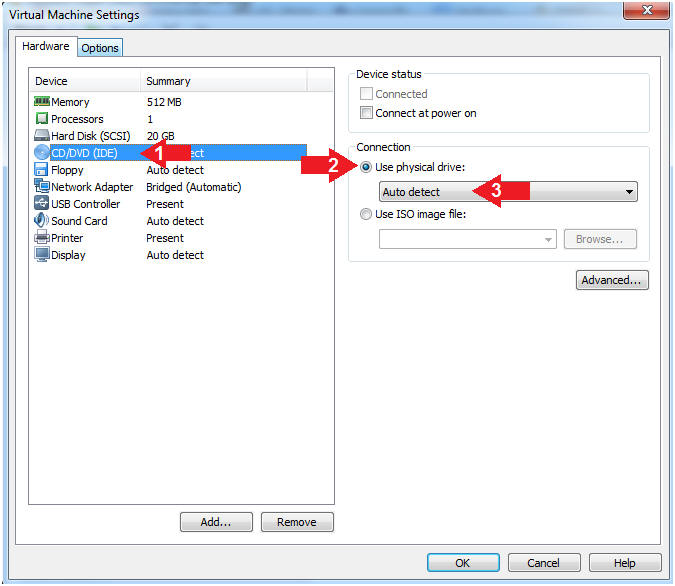
- Auto Detect Hard Drive
- Instructions:
- Click on CD/DVD(IDE)
- Click the Use physical drive: radio
button
- Make sure Auto detect is selected
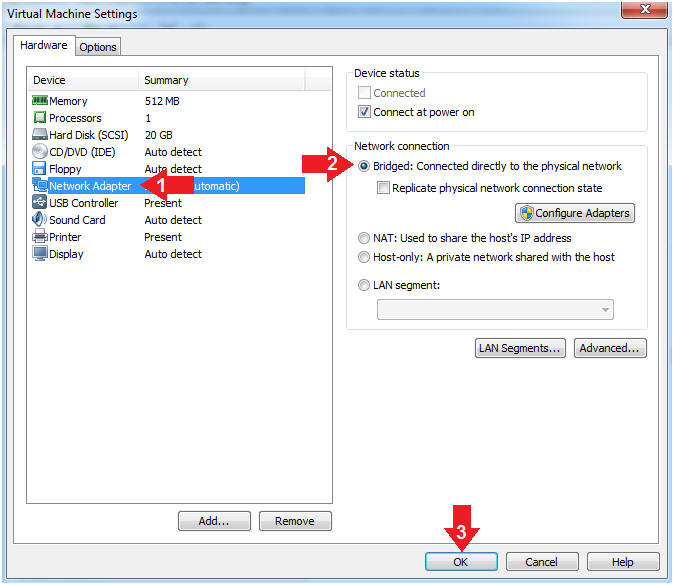
- Edit Network Adapter
- Instructions:
- Highlight Network Adapter
- Select Bridged
- Click the OK Button
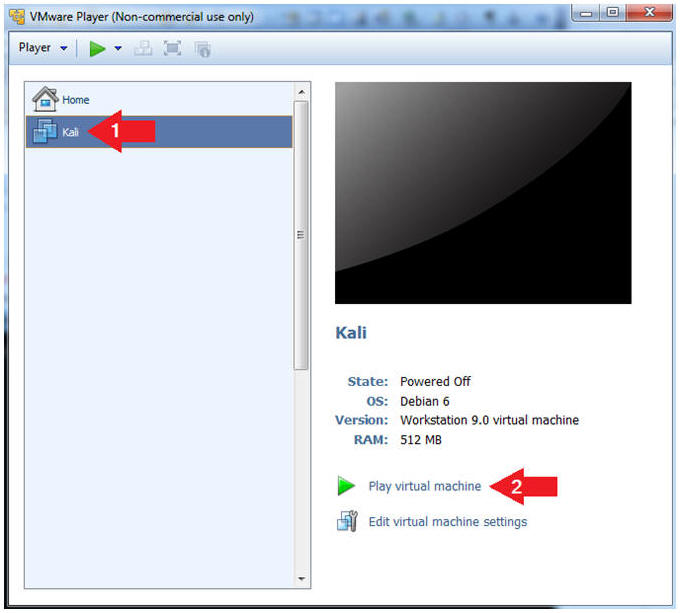
- Start the Kali VM
- Instructions:
- Click on the Kali VM
- Click on Play virtual machine
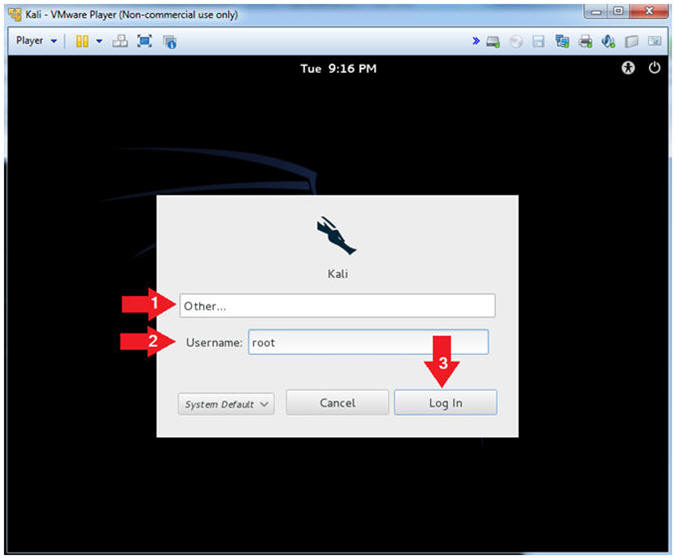
- Supply Username
- Instructions:
- Click Other
- Username: root
- Click the Login Button
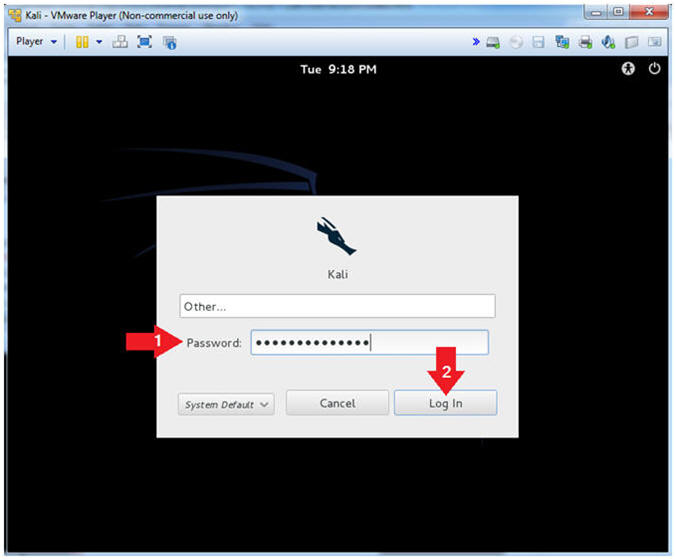
- Supply Password
- Instructions:
- Password: Provide the root password
- Click the Login Button
|
Section 3. Obtain IP Address Address |
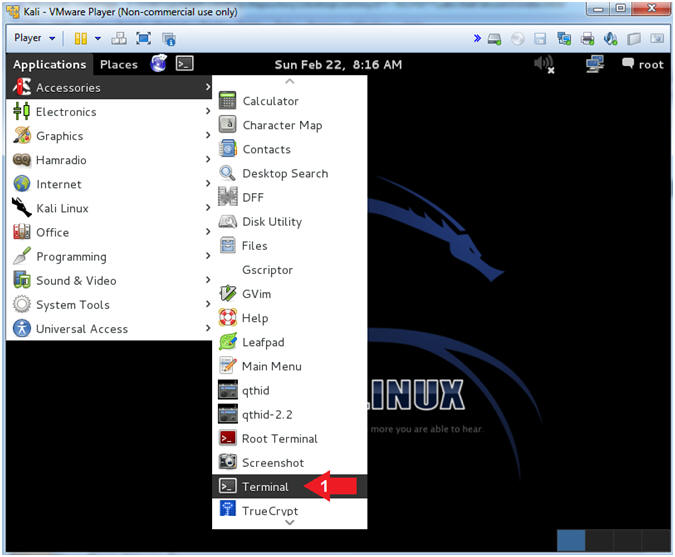
- Open a Terminal
- Instructions:
- Applications --> Accessories -->
Terminal
- Get IP Address
- Instructions:
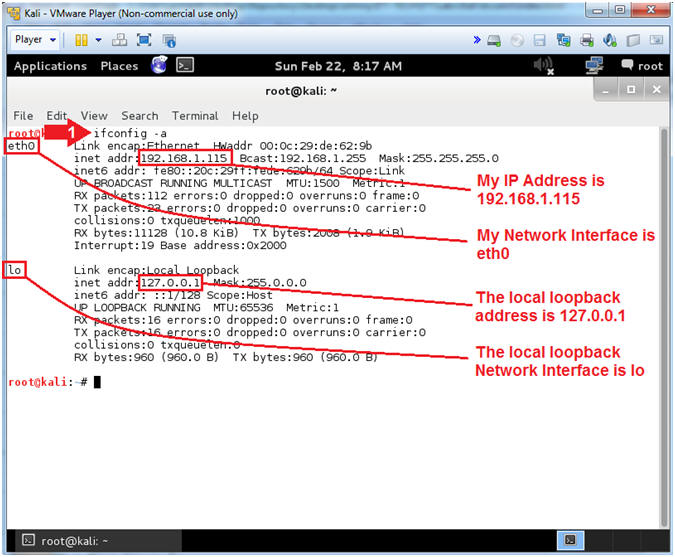
- ifconfig -a
- Notes (FYI):
- As indicated below, my IP address is
192.168.1.115 for Network Interface eth0.
- Please record your IP address
- The Local Loopback Address is 127.0.0.1
for Network Interface lo.
- The loopback device is a special,
virtual network interface that your computer uses to communicate
with itself. When the network or wifi is disconnected the
loopback exists so applications running on your computer can
always connect to servers on the same machine.
|
Section 4. Download
Brutessh |
- Install python-crypto
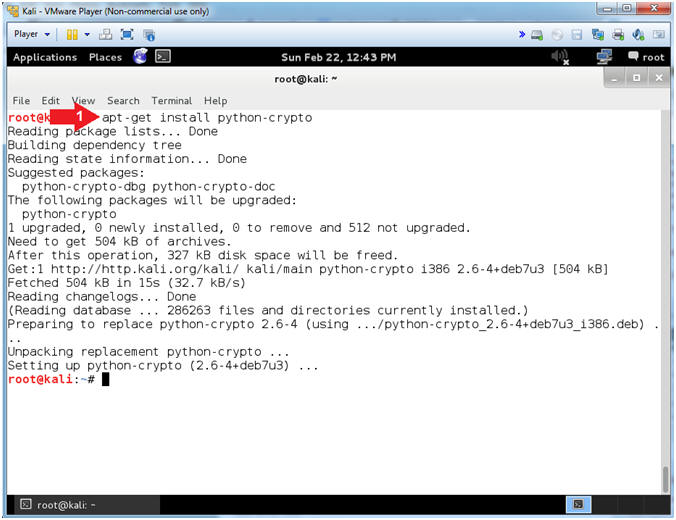
- Instructions:
- apt-get install python-crypto
- Note(FYI):
- This is a collection of both secure
hash functions (such as SHA256 and RIPEMD160), and various
encryption algorithms (AES, DES, RSA, ElGamal, etc.)
- Install python-paramiko
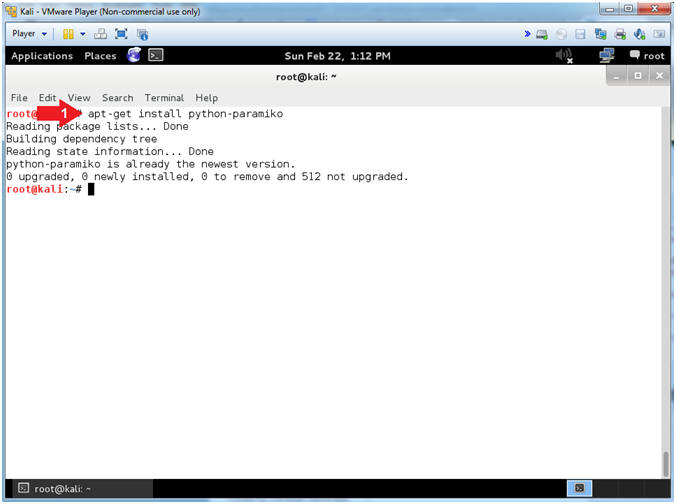
- Instructions:
- apt-get install python-paramiko
- Note(FYI):
- In my case, python-paramiko is at the
latest version.
- Paramiko is a Python implementation of
the SSHv2 protocol, providing both client and server functionality.
Paramiko itself is a pure Python interface around SSH networking
concepts.
- Download, Unzip and Untar brutessh.zip
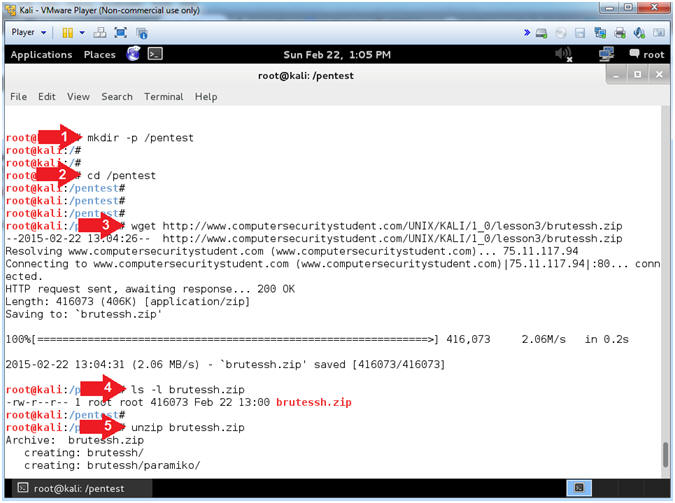
- Instructions:
- mkdir -p /pentest
- cd /pentest
- wget http://www.computersecuritystudent.com/UNIX/KALI/1_0/lesson3/brutessh.zip
- ls -l brutessh.zip
- unzip brutessh.zip
- Test brutessh.py
- Instructions:
- cd brutessh/
- python brutessh.py -help
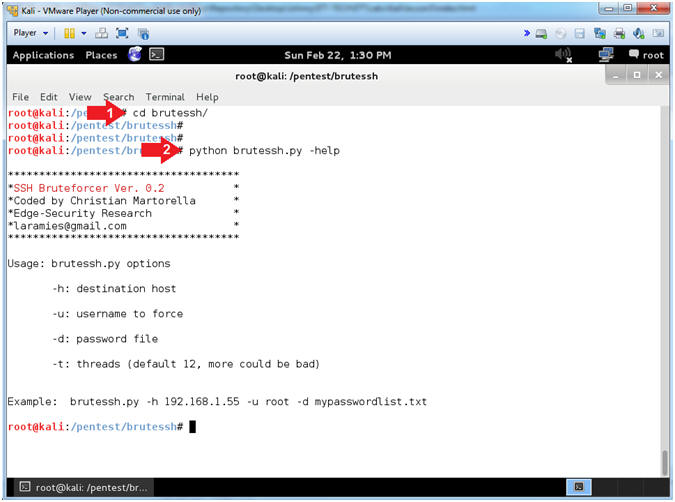
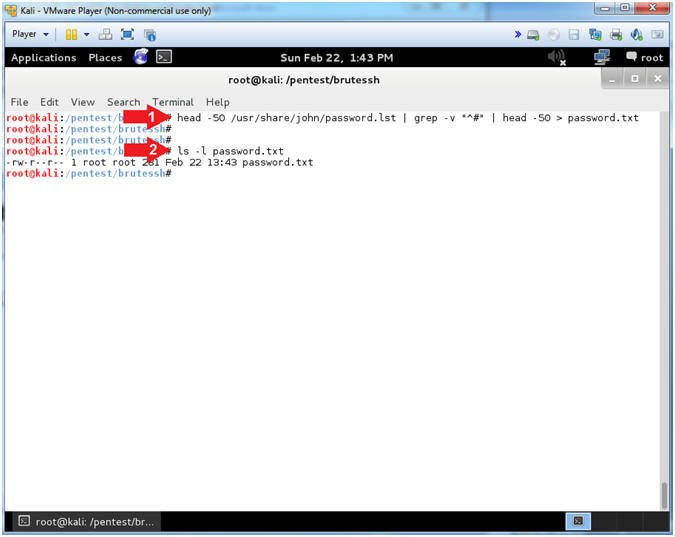
- Create BruteSSH Password List
- Instructions:
- head -50 /usr/share/john/password.lst
| grep -v "^#" | head -50 > password.txt
- I grabbed the first 50 passwords,
minus the comments(#), from John the Ripper to create enough
future brute force ssh traffic for denyhosts to block.
- ls -l password.txt
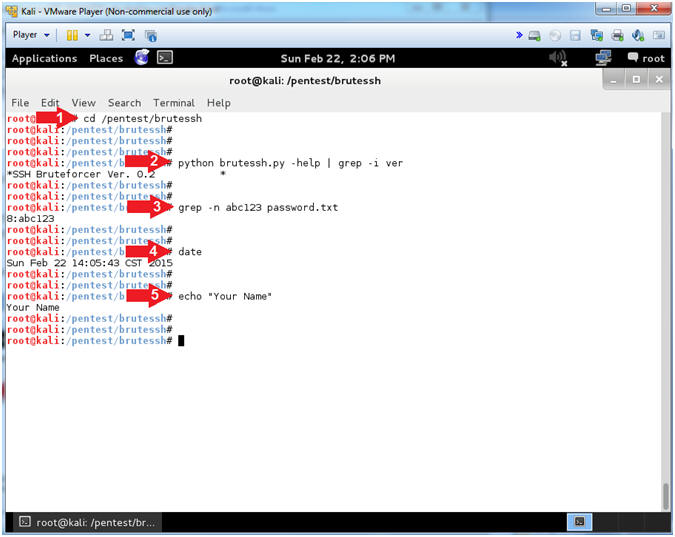
- Proof of Lab
- Instructions:
- cd /pentest/brutessh
- python brutessh.py -help | grep -i ver
- grep -n abc123 password.txt
- date
- echo "Your Name"
- Replace the string "Your Name" with
your actual name.
- e.g., echo "John Gray"
-
Proof of Lab
Instructions
- Do a <PrtScn>
- Paste into a word document
- Upload to Moodle
|
 
|