(Ubuntu: Lesson 8)
{ Installing and Securing openssh-server (a.k.a., sshd) }
| Section 0. Background Information |
- What is SSHD
- sshd (OpenSSH Daemon) is the daemon program for ssh(1). Together these programs replace rlogin(1) and rsh(1), and provide secure encrypted communications between two untrusted hosts over an insecure network.
- What is apt-get, dpkg and update-rc.d
- apt-get: APT is acronym for Advanced Package Tool. It supports installing packages over internet (ftp or http).
- dpkg: Debian packaging tool which can be use to install, query, uninstall packages.
- update-rc.d: The update-rc.d command is used to create startup, enable, kill, and remove scripts for services listed in the /etc/init.d
- Prerequisite
-
Lab Notes
- In this lab we will how to do the following:
- We will update the apt-get package list.
- We will use dpkg to search the package list for openssh-server.
- We will use apt-get to install openssh-server.
- We will secure SSHD using the /etc/ssh/sshd_conf file.
- We will use update-rc.d to create runlevel startup and kill scripts..
- In this lab we will how to do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- You are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2012 No content replication of any kind is allowed without express written permission.
| Section 1: Start Ubuntu 12.04 |
- Start Ubuntu 12.04
- Instructions
- For Windows 7
- Start --> All Programs --> VMware Player
- For Windows XP
- Starts --> Programs --> VMware Player
- For Windows 7
- Instructions
- Verify Virtual Machine Settings.
- Instructions
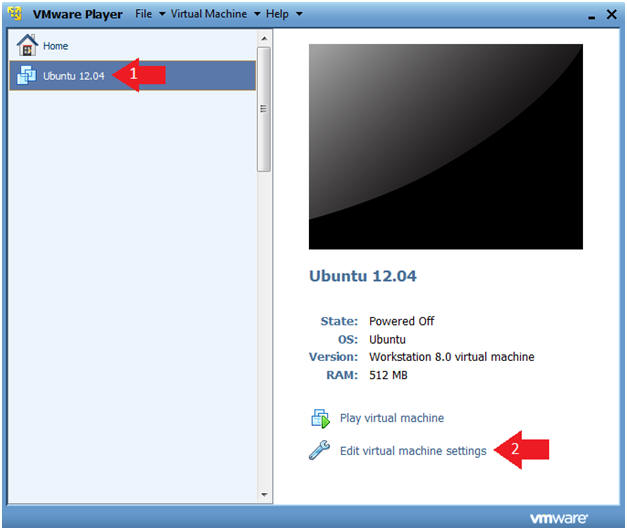
- Click on Ubuntu 12.04
- Click on Edit virtual machine settings
- Instructions
- Configure Network Adapter
- Instructions
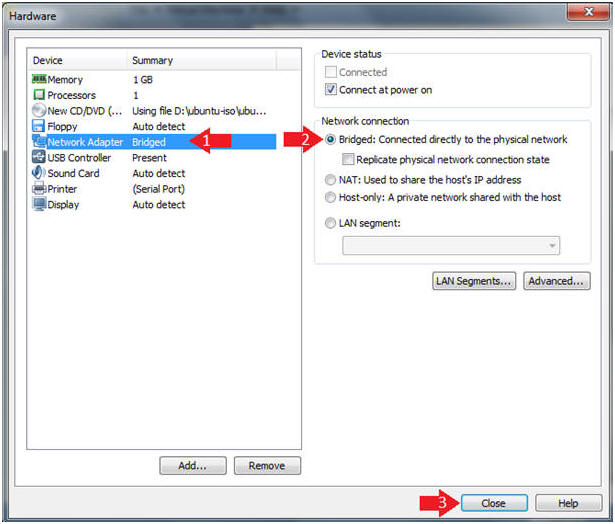
- Click on Network Adapter
- Click on the Bridged Radio Button
- Click on the Close Button
- Instructions
- Start the Ubuntu 12.04 VM
- Instructions
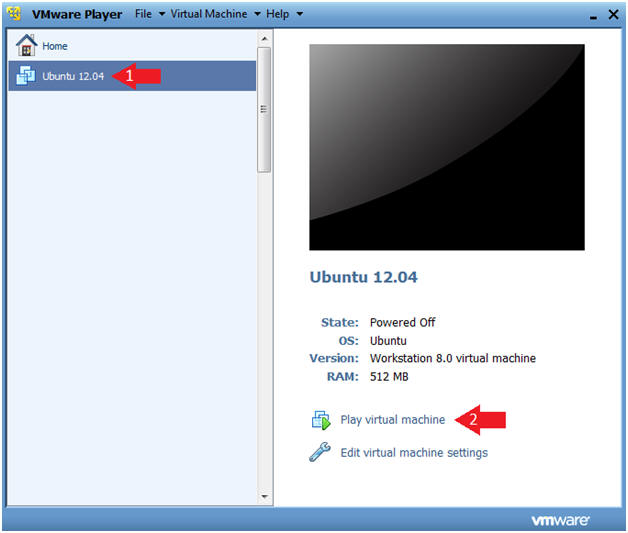
- Click on Ubuntu 12.04
- Click on Play virtual machine
- Instructions
| Section 2: Login to Ubuntu |
- Change to Gnome Classic
- Instructions:
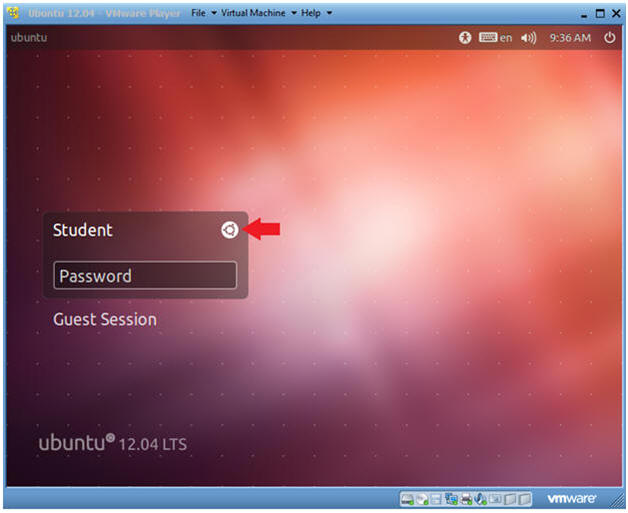
- Click on the Circle
- Instructions:
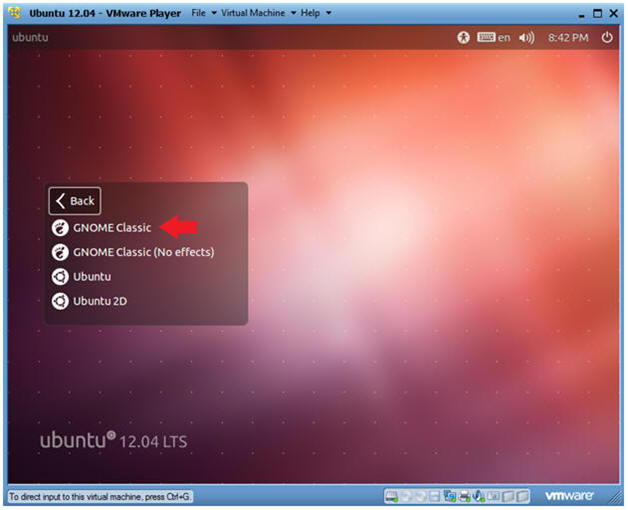
- Select Gnome Classic
- Instructions:
- Double Click on GNOME Classic
- Instructions:
- Login to Server
- Instructions
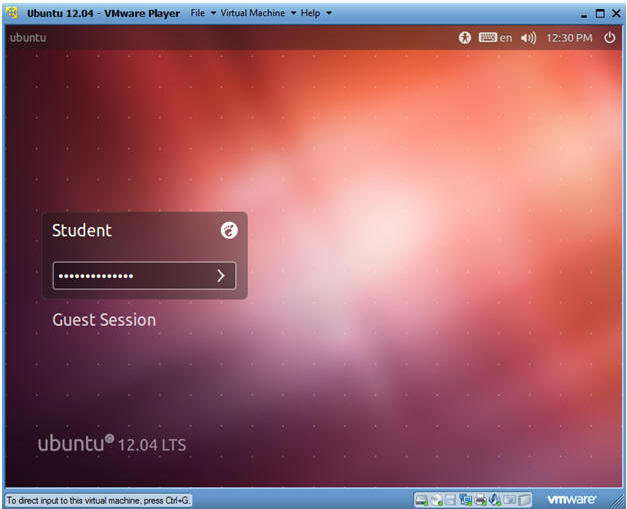
- User: Student
- Password: Please supply the student password.
- Instructions
| Section 3: Become Root and Verify Network Connection |
- Start up a Terminal
- Instructions
- Click on the Terminal
- Instructions
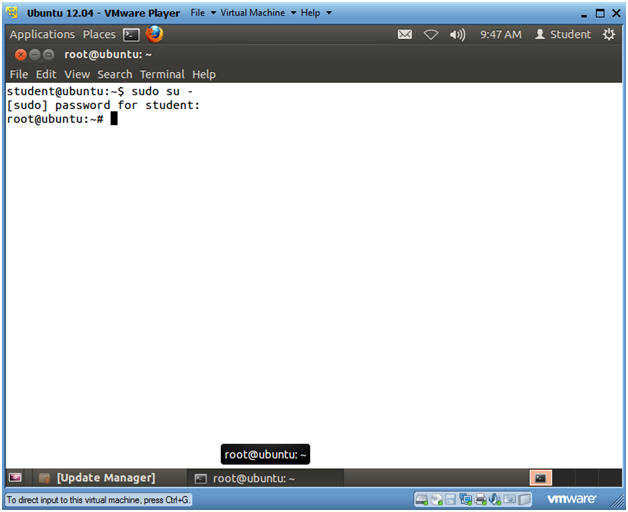
- Become Root
- Instructions
- sudo su -
- Supply the student password.
- Instructions
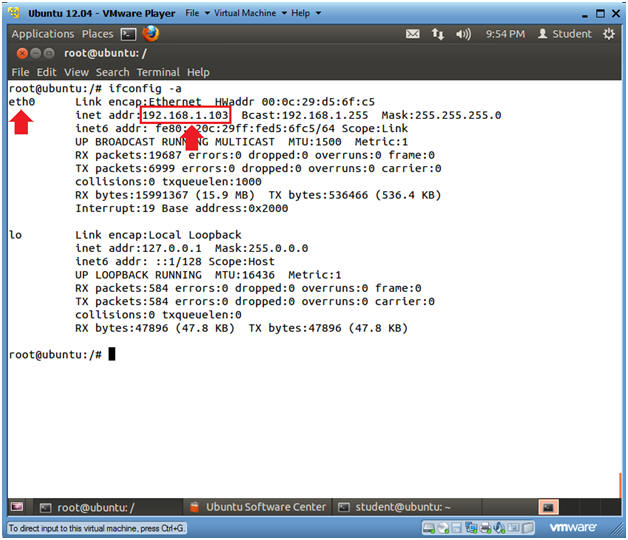
- Verify you have a network connection
- Instructions
- ifconfig -a
- eth0 is the name of my interface.
- 192.168.1.103 is my network IP address.
- ifconfig -a
- Notes(FYI)
- If you do not have an DHCP IP Address
try the following:
- dhclient
- OR
- /etc/init.d/networking restart
- dhclient
- If you do not have an DHCP IP Address
try the following:
- Instructions
| Section 3: Update apt-get's package index |
- Update apt-get's package index
- Instructions
- apt-get update
- Notes(FYI)
- update is used to resynchronize the package index files from their sources. I.e., The "update" flag updates apt-get's local database with debian server's pkglist files. The indexes of available packages are fetched from the location(s) specified in /etc/apt/sources.list.
- Instructions
| Section 4: Search for openssh-server |
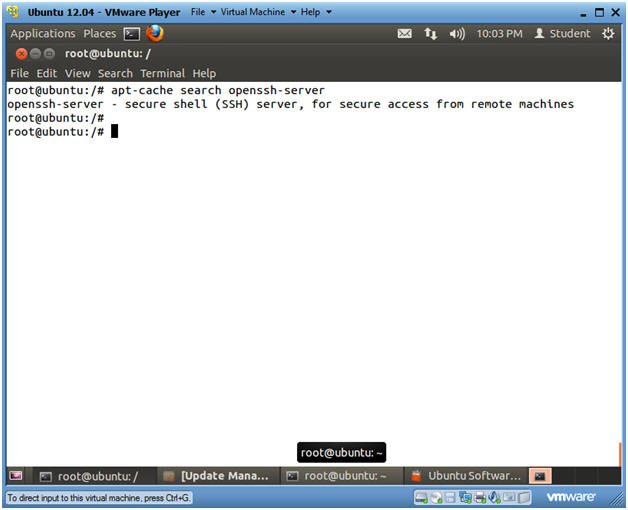
- Search for openssh-server
- Instructions
- apt-cache search openssh-server
- Notes(FYI)
- apt-cache is a command to manipulate and obtain information from the ubuntu packages.
- Instructions
| Section 5: Install openssh-server |
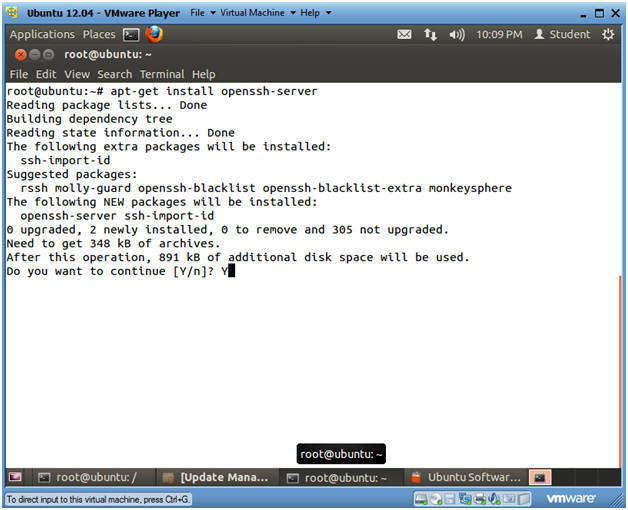
- Install openssh-server
- Instructions
- apt-get install openssh-server
- Do you want to continue? Y
- Instructions
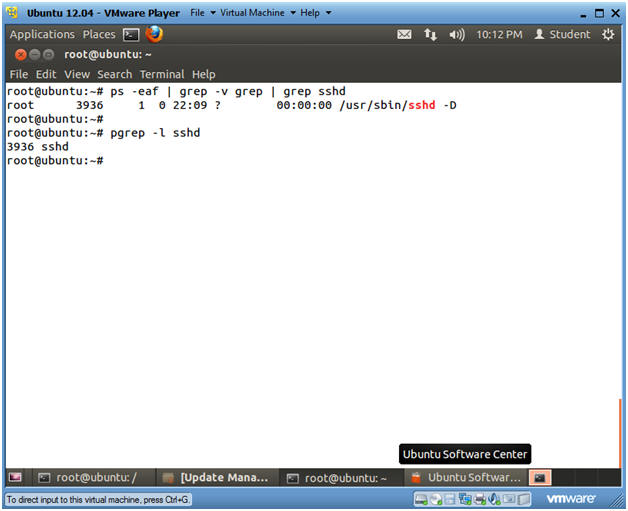
- Verify that openssh-server is installed and is
running
- Instructions
- ps -eaf | grep -v grep | grep sshd
- ps -eaf, show all processes.
- grep -v grep, filter out the grep process.
- grep sshd, show only the sshd process.
- pgrep -l sshd
- pgrep, is a command that combines both the "ps" and the "grep" commands.
- ps -eaf | grep -v grep | grep sshd
- Instructions
| Section 6: Startup Script for openssh-server |
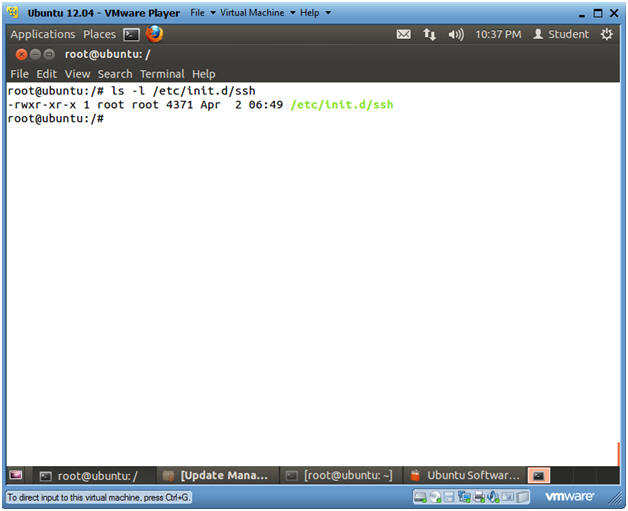
- Startup Script for openssh-server
- Instructions
- ls -l /etc/init.d/ssh
- Notes(FYI)
- As part of the openssh-server installation, the ssh startup script is placed in /etc/init.d/ssh.
- Instructions
- Stopping and Starting SSHD with /etc/init.d/ssh
- Instructions
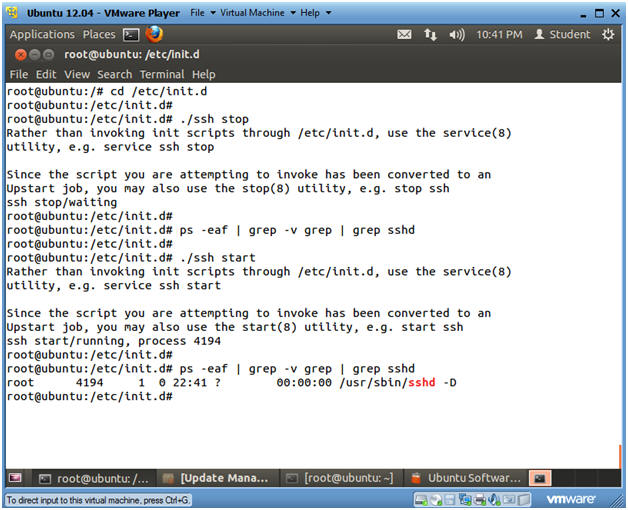
- cd /etc/init.d
- ./ssh stop
- ps -eaf | grep -v grep | grep sshd
- Notice, that no lines are returned, because sshd is not running.
- ./ssh start
- ps -eaf | grep -v grep | grep sshd
- Now one line is returned, because sshd is running.
- Instructions
- Stopping and Starting SSHD with the "service"
command
- Instructions
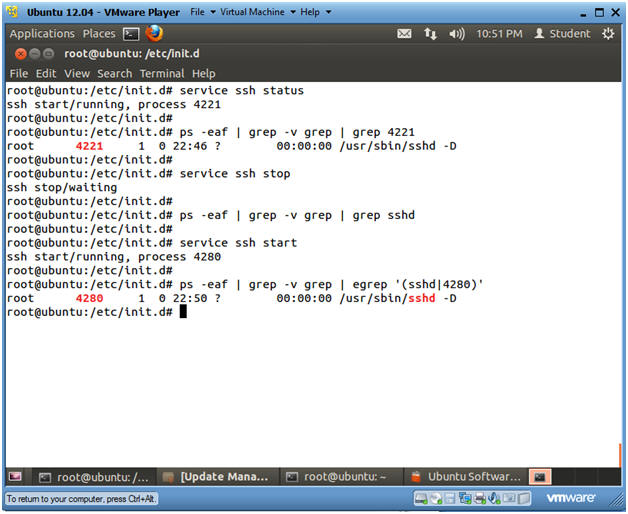
- service ssh status
- Notice, if ssh is running a process number is displayed call the PID (process ID).
- In my case, the PID is 4221.
- ps -eaf | grep -v grep | grep
4221
- Replace 4221, which your ssh PID.
- service ssh stop
- This command still stop the ssh daemon.
- ps -eaf | grep -v grep | grep sshd
- Notice, no processes are displayed for sshd, because we stopped sshd in the above command.
- service ssh start
- Since, we restart sshd, it has a new PID of 4280 in my case.
- ps -eaf | grep -v grep | egrep
'(sshd|4280)'
- ps -eaf, display all processes.
- grep -v grep, filter out the grep command.
- egrep '(sshd|4280)', search for any process containing the string sshd or 4280. Remember 4280 is my PID, and to replace 4280 with your PID.
- service ssh status
- Instructions
| Section 7: Securing openssh-server |
- Backup the /etc/ssh/sshd_config file
- Instructions
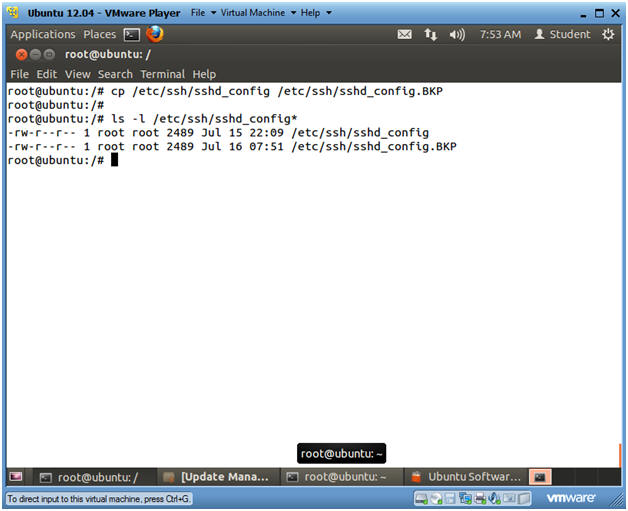
- cp /etc/ssh/sshd_config /etc/ssh/sshd_config.BKP
- ls -l /etc/ssh/sshd_config*
- Instructions
- Open the /etc/ssh/sshd_config file
- Instructions
- vi /etc/ssh/sshd_config
- Notes(FYI)
- The sshd_config file is the openssh-server configuration file.
- Instructions
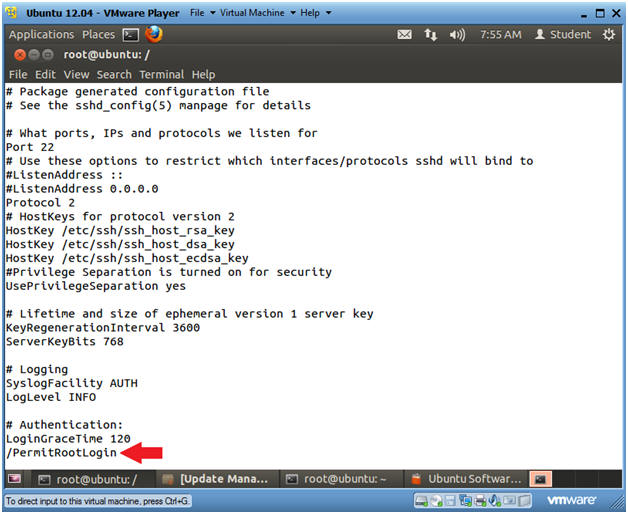
- Search for PermitRootLogin
- Instructions
- Press the "/"
key
- This will put the VI editor into search mode.
- Type "PermitRootLogin"
- Press the <Enter> key
- Press the "/"
key
- Instructions
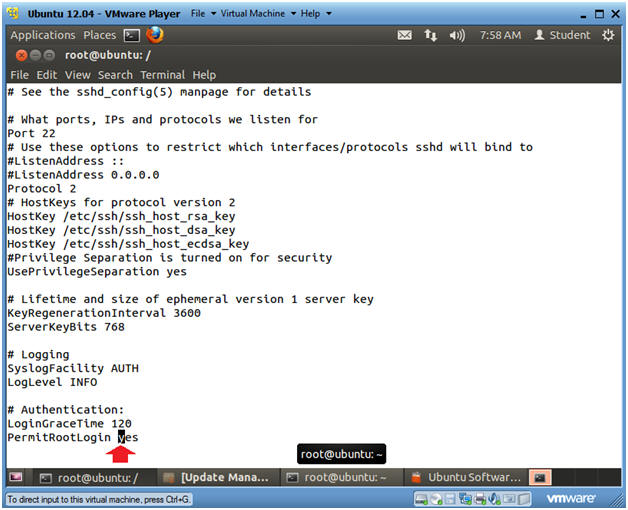
- Edit PermitRootLogin Directive
- Instructions
- Right arrow over until the cursor is on the "y" in yes.
- Type "cw"
- cw, means change word.
- Type "no"
- By replacing "yes" with "no", we are not allowing the root user to login via ssh directly as root.
- Press the <Esc> key
- Instructions
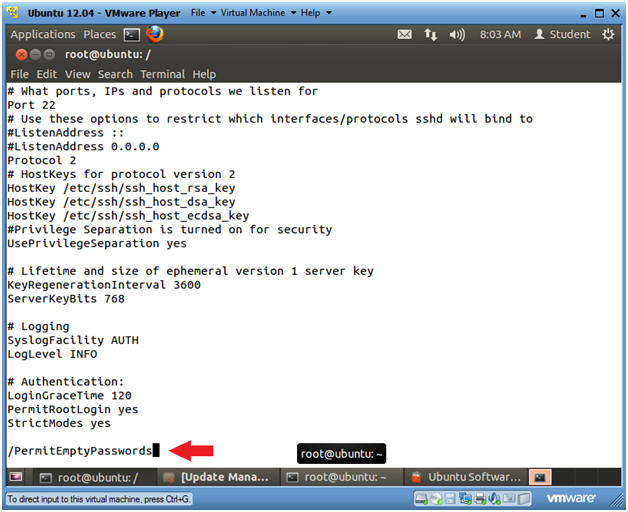
- Search for PermitEmptyPasswords
- Instructions
- Press the "/"
key
- This will put the VI editor into search mode.
- Type "PermitEmptyPasswords"
- Press the <Enter> key
- Press the "/"
key
- Instructions
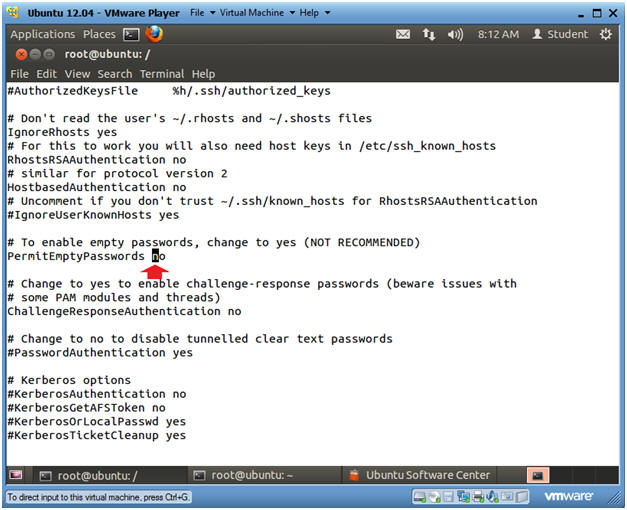
- Verify PermitEmptyPasswords is set to no
- Instructions
- By default PermitEmptyPasswords is set to "no".
- If PermitEmptyPasswords is set to "yes" for some unknown remarkable stupid reason, please set it to "no".
- Instructions
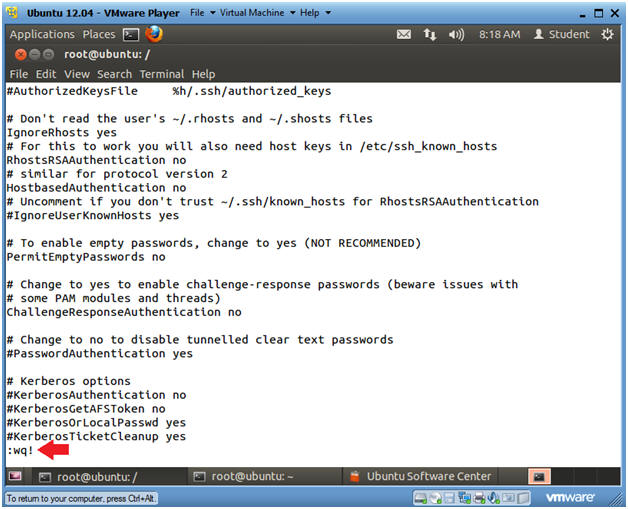
- Save the /etc/ssh/sshd_config file
- Instructions
- Press the <Esc> key
- Type ":wq!"
- Press <Enter>
- Instructions
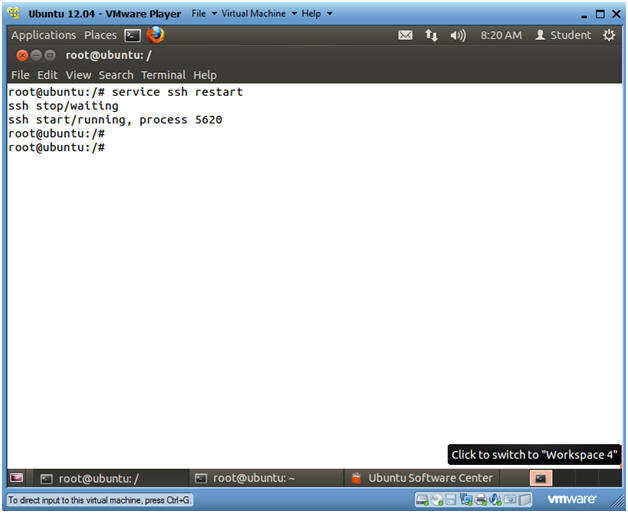
- Restart openssh-server
- Instructions
- service ssh restart
- Instructions
| Section 8: Create startup and kill scripts for openssh-server |
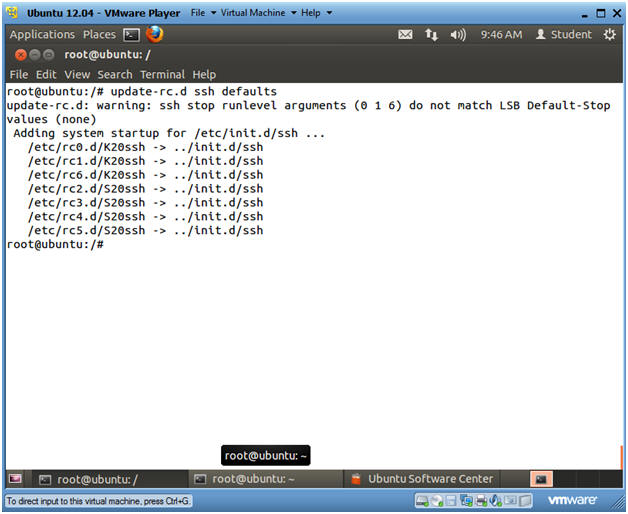
- Create startup and kill scripts for openssh-server
- Instructions
- update-rc.d ssh defaults
- Notes(FYI)
- The update-rc.d command is used to create startup, enable, kill, and remove scripts for services listed in the /etc/init.d.
- If defaults is used then update-rc.d will make links to start the service in runlevels 2345 and to stop the service in runlevels 016. By default all the links will have sequence number 20.
- Instructions
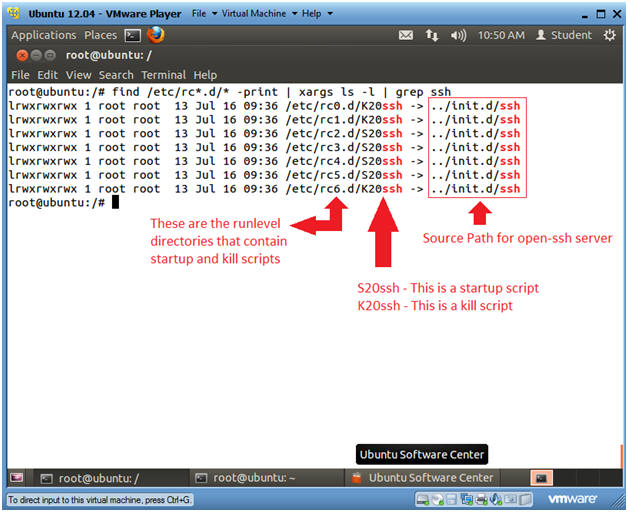
- Verify startup and kill script was created
- Instructions
- find /etc/rc*.d/* -print | xargs ls -l
| grep ssh
- find /etc/rc*.d/* -print, list all the file in /etc/rc*.d/*
- xargs ls -l, Use the xargs command to issue provide a long list of each file that find displays.
- grep ssh, only display files containing ssh.
- find /etc/rc*.d/* -print | xargs ls -l
| grep ssh
- Instructions
| Section 9: Proof of Lab |
- Proof of Lab
- Instructions
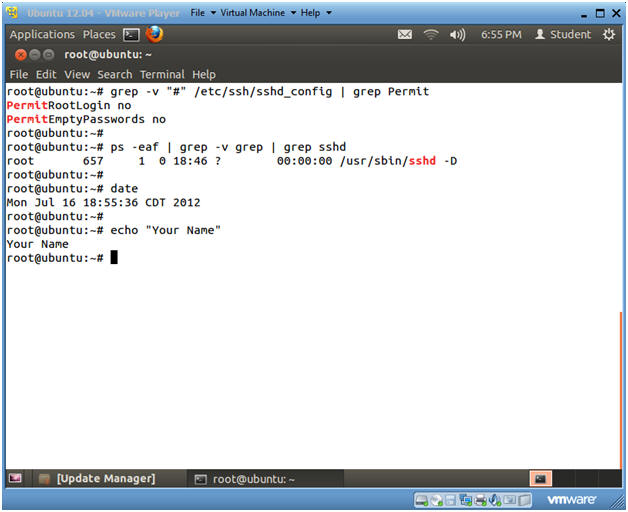
- grep -v "#" /etc/ssh/sshd_config | grep Permit
- ps -eaf | grep -v grep | grep sshd
- date
- echo "Your Name"
- Replace the string "Your Name" with your actual name.
- e.g., echo "John Gray"
-
Proof of Lab Instructions
- Press both the <Ctrl> and <Alt> keys at the same time.
- Do a <PrtScn>
- Paste into a word document
- Upload to Moodle
- Instructions