(Damn Vulnerable Windows XP: Lesson 9)
{ How to setup the PCMan's FTP Server 2.0.7 Buffer Overflow }
| Section 0. Background Information |
- What is Damn Vulnerable Windows XP?
- This is a Windows XP Virtual Machine that provides a practice environment to conduct ethical penetration testing, vulnerability assessment, exploitation and forensics investigation.
- The Microsoft Software License Terms for the IE VMs are included in the release notes.
- By downloading and using this software, you agree to these license terms.
- What is PCMan
FTP Server?
- PCMan's FTP Server is a free software mainly designed for beginners not familiar with how to set up a basic FTP. Configuration is made very easy. Consequently, functionality and security are not major concerns. Accordingly, the following exploit (CVE-2013-4730) exists.
- What is
the PCMan FTP Server 2.0.7 Buffer Overflow Exploit?
- The CVE Vulnerability number is CVE-2013-4730.
- Buffer overflow in PCMan's FTP Server 2.0.7 allows remote attackers to execute arbitrary code via a long string in a USER command.
- Implementing the
CVE-2013-4730 with PCMan FTP Server 2.0.7
- The following lesson will show you how to down, install and run PCMan.
- The Post-Requisite Lesson will show you how to illustrate the exploit.
- Pre-Requisite
- Post-Requisite
-
Lab Notes
- In this lab we will do the following:
- Download PCMan FTP Server 2.0.7
- Install PCMan FTP Server 2.0.7
- In this lab we will do the following:
- Legal Disclaimer
- As a condition of your use of this Web site, you warrant to computersecuritystudent.com that you will not use this Web site for any purpose that is unlawful or that is prohibited by these terms, conditions, and notices.
- In accordance with UCC § 2-316, this product is provided with "no warranties, either express or implied." The information contained is provided "as-is", with "no guarantee of merchantability."
- In addition, this is a teaching website that does not condone malicious behavior of any kind.
- You are on notice, that continuing and/or using this lab outside your "own" test environment is considered malicious and is against the law.
- © 2016 No content replication of any kind is allowed without express written permission.
| Section 1: Log into Damn Vulnerable WXP-SP2 |
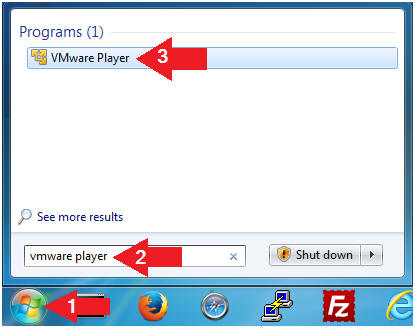
- Open VMware Player on your windows machine.
- Instructions:
- Click the Start Button
- Type "vmware player" in the search box
- Click on VMware Player
- Instructions:
- Edit Virtual Machine Settings
- Instructions:
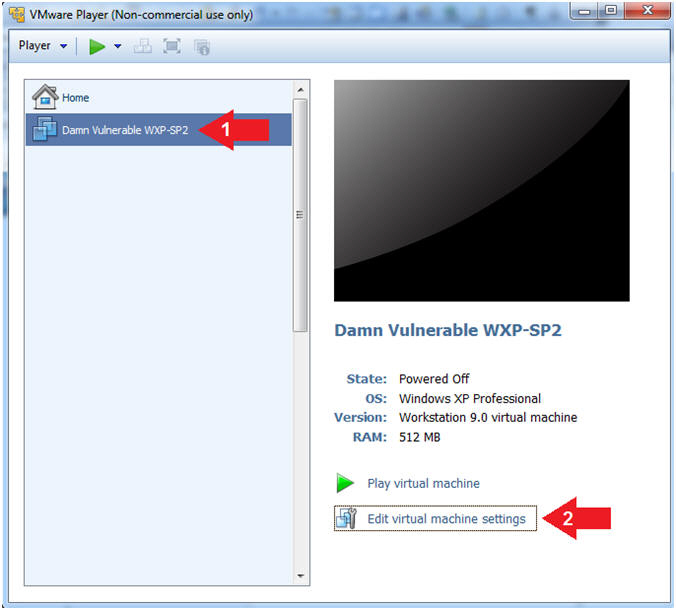
- Click on Damn Vulnerable WXP-SP2
- Edit Virtual Machine Settings
- Note:
- Before beginning a lesson it is necessary to check the following VM settings.
- Instructions:
- Set Network Adapter
- Instructions:
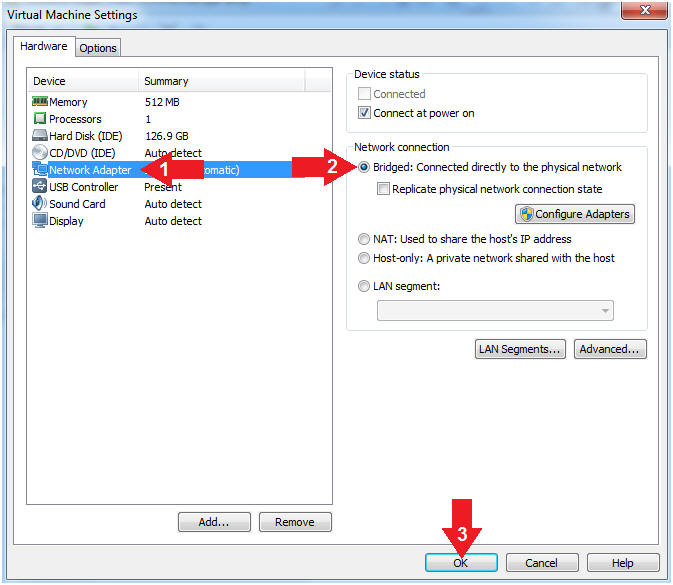
- Click on Network Adapter
- Click on the radio button "Bridged: Connected directly to the physical network".
- Click the OK Button
- Instructions:
- Start Up Damn Vulnerable WXP-SP2.
- Instructions:
- Start Up your VMware Player
- Play virtual machine
- Instructions:
- Logging into Damn Vulnerable WXP-SP2.
- Instructions:
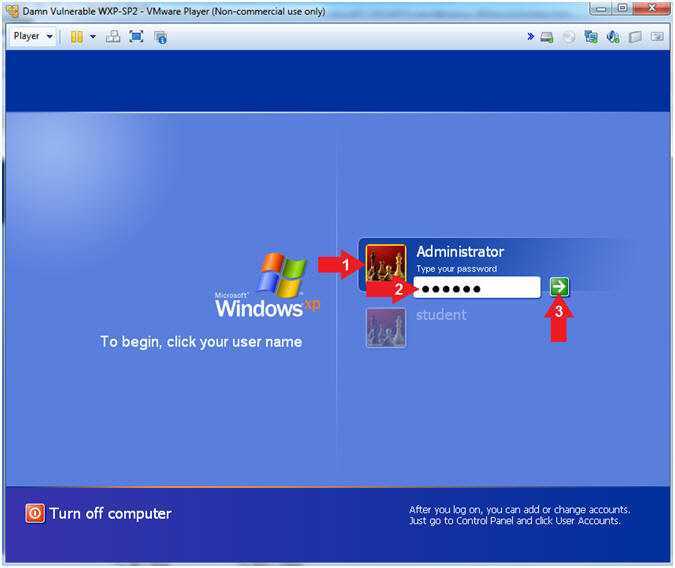
- Click on Administrator
- Password: Supply Password
- (See Note)
- Press <Enter> or Click the Arrow
- Note(FYI):
- Password was created in (Lab 1, Section 1, Step 8)
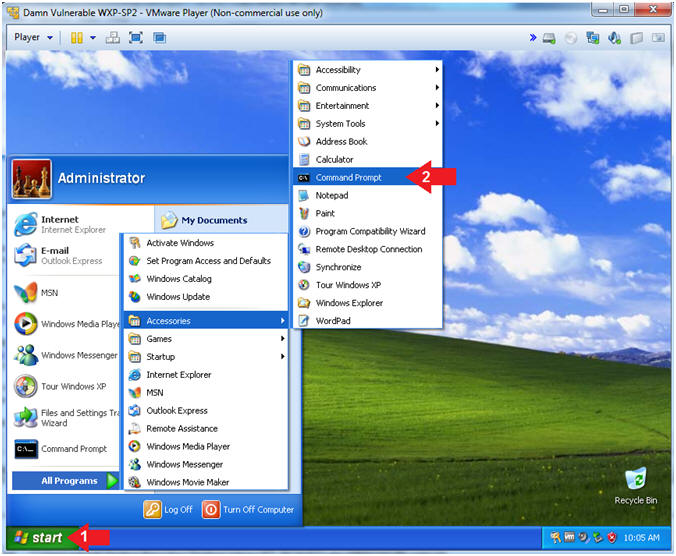
- Instructions:
- Open the Command Prompt
- Instructions:
- Click the Start Button
- All Programs --> Accessories --> Command Prompt
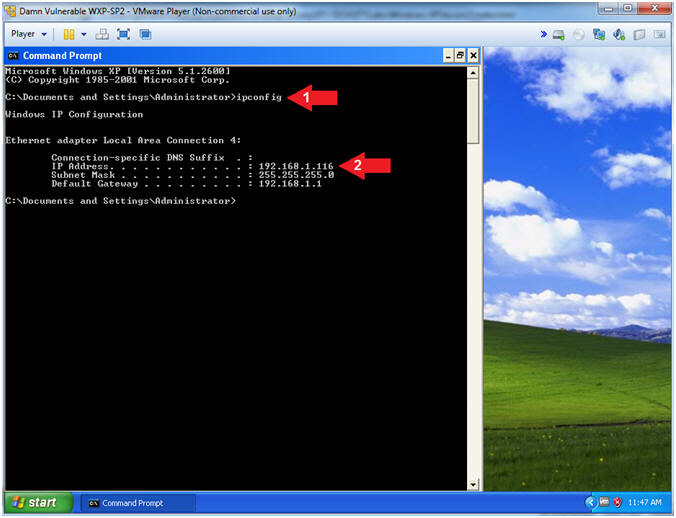
- Instructions:
- Obtain Damn Vulnerable WXP-SP2's IP Address
- Instructions:
- ipconfig
- Record Your IP Address
- Note(FYI):
- In my case, Damn Vulnerable WXP-SP2's IP Address 192.168.1.116.
- This is the IP Address of the Victim Machine.
- Instructions:
| Section 2: Install PCMan's FTP Server 2.0.7 |
- Open Firefox
- Instructions:
- Click the Start Button
- All Programs --> Mozilla Firefox
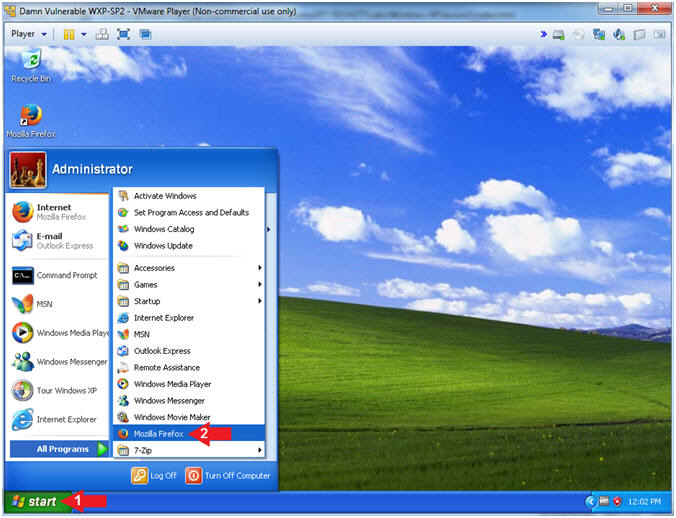
- Instructions:
- Download PCMan 2.0.7
- Instructions:
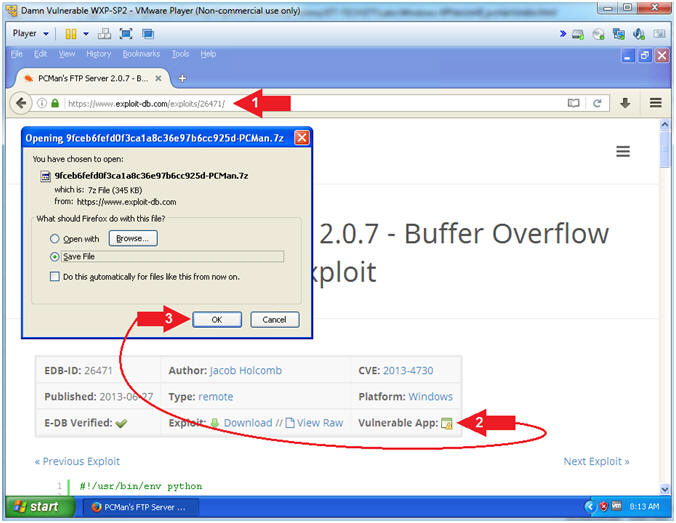
- Navigate to the following
URL
- https://www.exploit-db.com/exploits/26471/
- Click on the Vulnerable
App Icon (
 )
) - Click the OK Button
- Navigate to the following
URL
- Instructions:
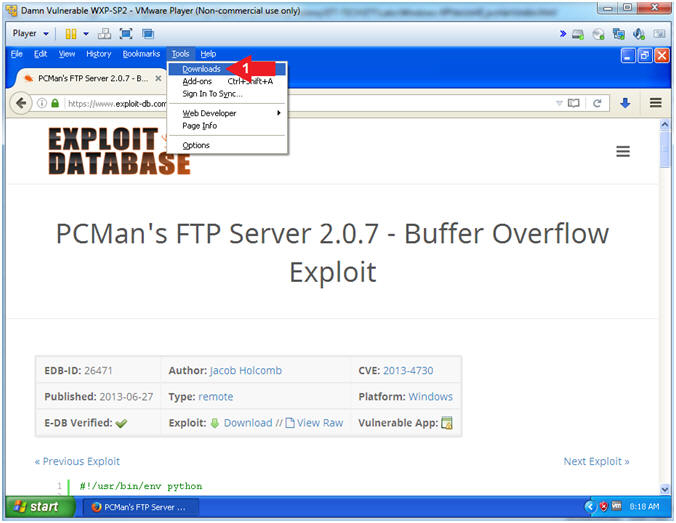
- Open Downloads Folder (Part 1)
- Instructions:
- Tools --> Downlaods
- Instructions:
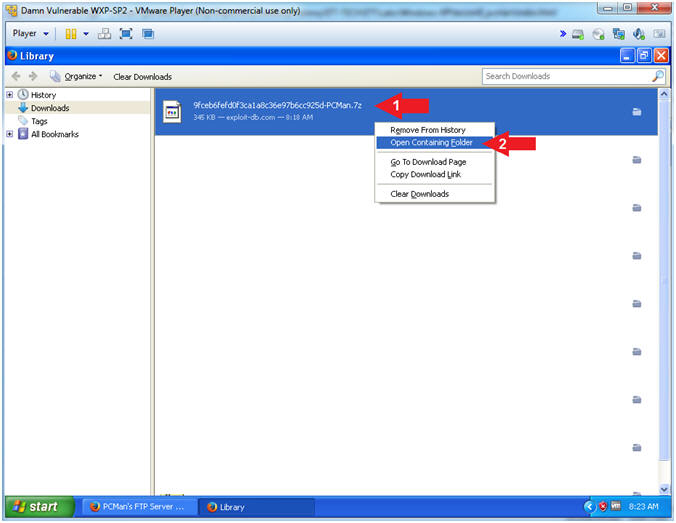
- Open Downloads Folder (Part 2)
- Instructions:
- Right Click on 9fceb6fefd0f3ca1a8c36e97b6cc925d-PCMan.7z
- Click on Open Containing Folder
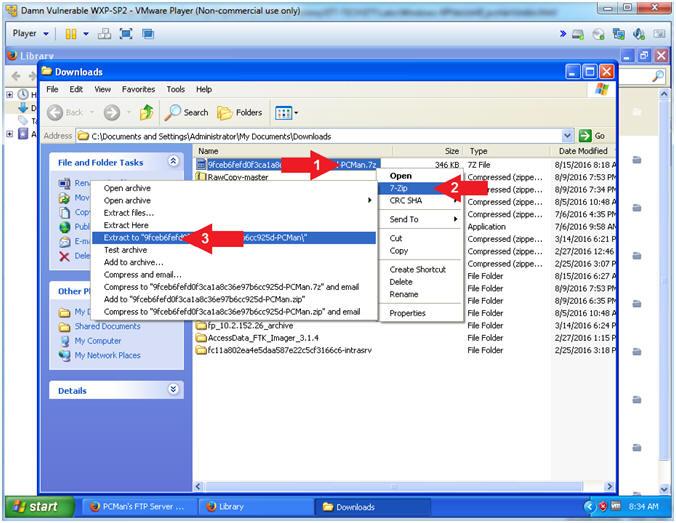
- Instructions:
- Extract the *PCMan.7z file
- Instructions:
- Right Click on *PCMan.7z
- Touch 7-Zip
- Click on Extract to *PCMan\
- Instructions:
- Open the *PCMan Folder
- Instructions:
- Right on *PCMan Folder
- Select Open
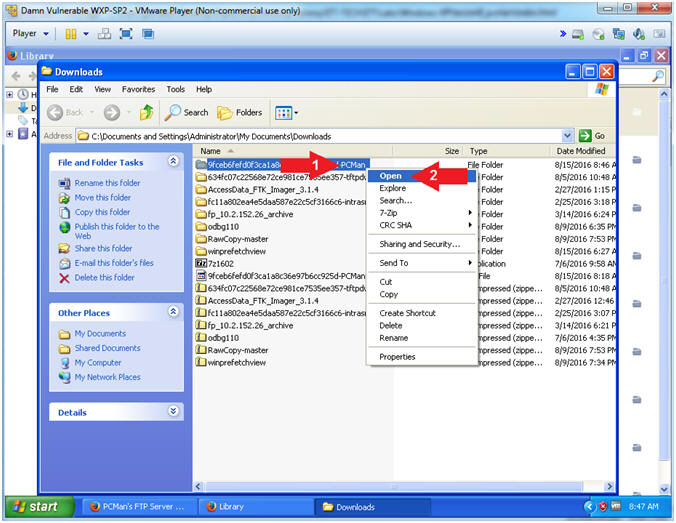
- Instructions:
- Create a PCMan Desktop Icon
- Instructions:
- Right on PCManFTPD2
- Touch Send To
- Select Desktop (create shortcut)
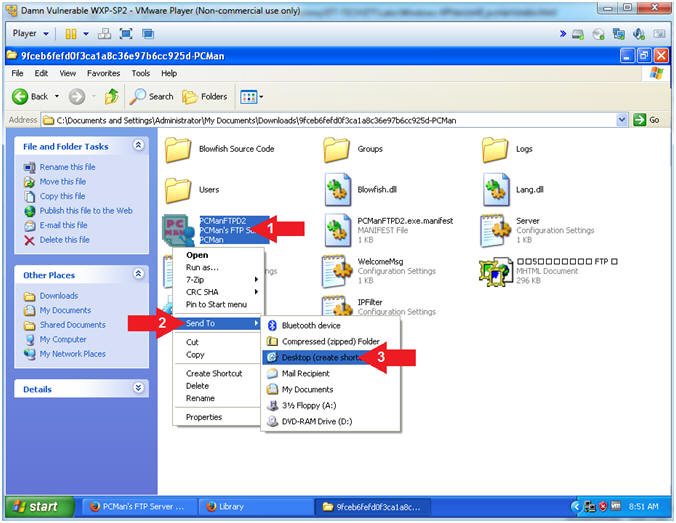
- Instructions:
- Show Desktop
- Instructions:
- Right Click on Blue Taskbar
- Select Show the Desktop
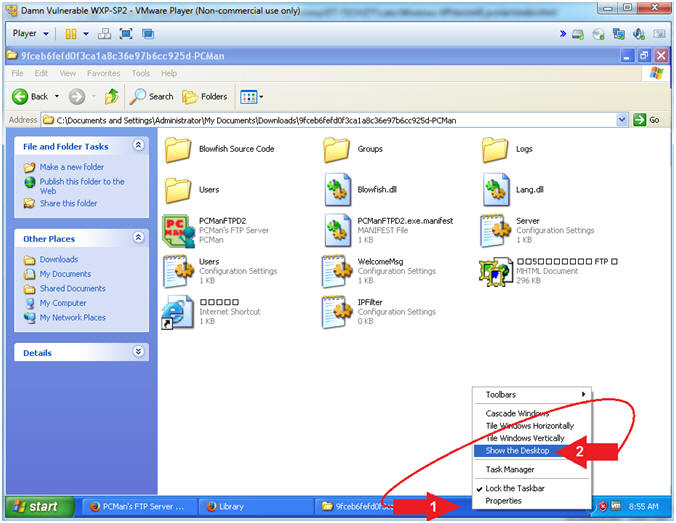
- Instructions:
- Run PCMan
- Instructions:
- Right Click on the PCMan Desktop Icon
- Select Open
- The PCMan FTP Server Application will appear
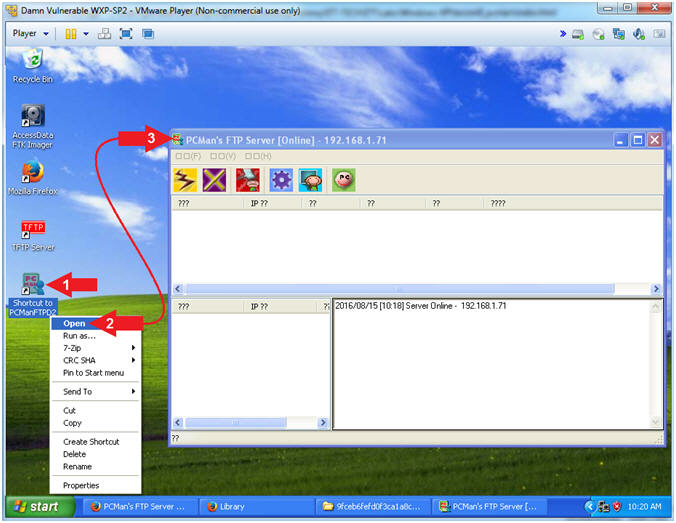
- Instructions:
| Section 3: Proof of Lab |
- Open the Command Prompt
- Instructions:
- Click the Start Button
- All Programs --> Accessories --> Command Prompt
- Instructions:
- Proof of Lab
- Instructions:
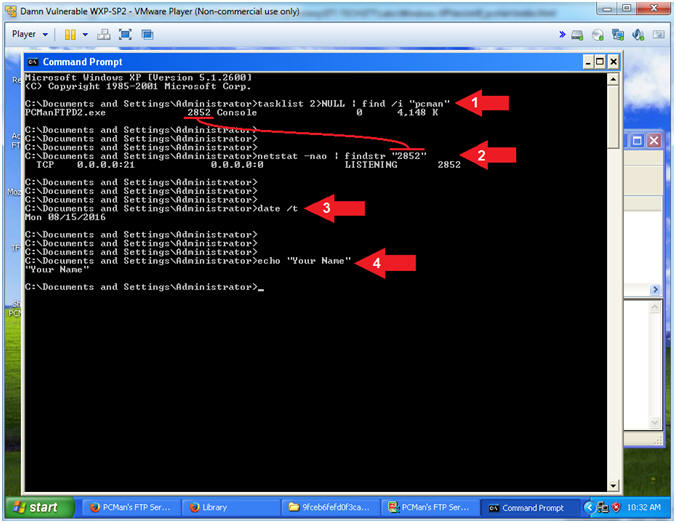
- tasklist 2>NULL| find /i "pcman"
- netstat -nao | findstr "2852"
- Replace the Process ID(2852) with your PCManFTPD2.exe Process ID.
- date /t
- echo "Your Name"
- Put in your actual name in place of "Your Name"
- e.g., echo "John Gray"
- Note(FYI):
- Command #1, Use (tasklist) to show all the running processes. Use (find) and ignore case (/i) to display only the processes that contain the string (pcman). Retrieve your Process ID associated with PCManFTPD2.exe. Mind is 2852.
- Command #2, Use (netstat -nao) to display all (a) network connections, their port numbers (n), and the owning process (o). Use (findstr) to display the Process ID(2852). Remember to replace my Process ID(2852) with your Process ID.
-
Proof of Lab
Instructions
- Press the <Ctrl> and <Alt> key at the same time.
- Press the <PrtScn> key.
- Paste into a word document
- Upload to Moodle
- Instructions: