(Windows 2008 Server: Lesson 6)
{ Creating Directories, ACLs, and using the icacls command}
| Section 0. Background Information |
- In this lab.
- In this lab we will directories, in which we allow and deny access to them.
- Also you will learn about the active directory command called icacls. (For more on icacls, please visit the below link).
- http://technet.microsoft.com/en-us/library/cc753525%28WS.10%29.aspx
| Section 1. Login to your W2K8 server. |
- Start your Windows 2008 Server
- Instructions:
- Click on W2K8 Server
- Click on Play virtual machine
- Instructions:
- CRTL + ALT + DELETE
- Instructions
- Virtual Machine
- Send Ctrl+Alt+Del
- Instructions
- Login as Administrator
- Click on the Administrator icon.
- Login
- Command: Provide the password for the Administrator account.
| Section 2. Creating the TOPSECRET directory and assign the ACL |
- Bring Up Computer (a.k.a., Windows Explorer)
- Instructions:
- Start --> Computer
-
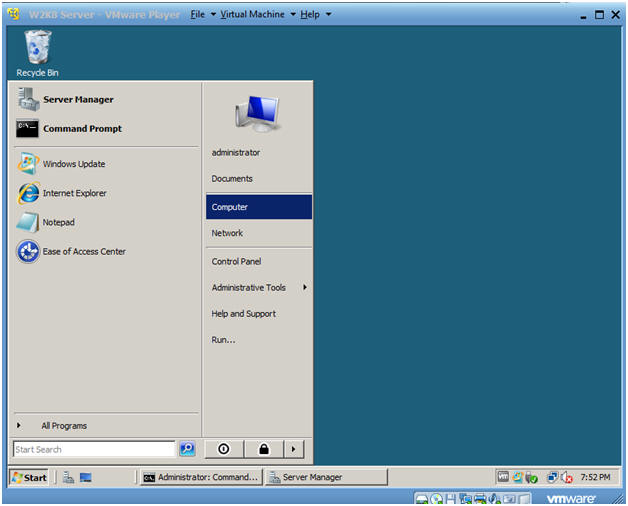
- Instructions:
- Select the C: Drive
- Instructions:
- Double Click on "Local Disk (C:)"
- Instructions:
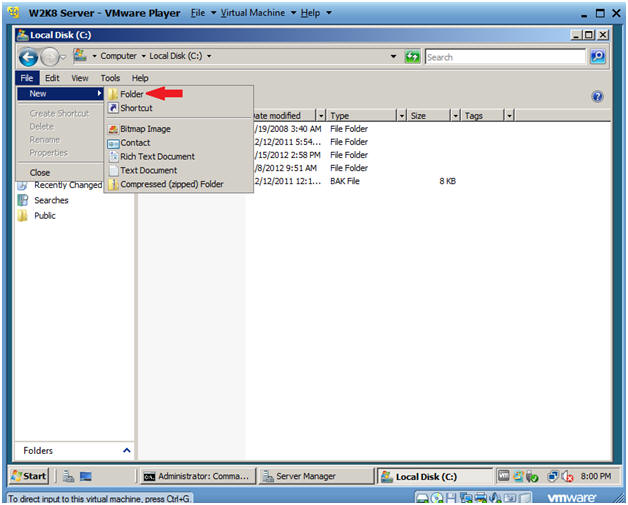
- Create a New Folder
- Instructions:
- File --> New --> Folder
- Instructions:
- Create a folder named "TOPSECRET"
- Instructions:
- Type TOPSECRET
- Instructions:
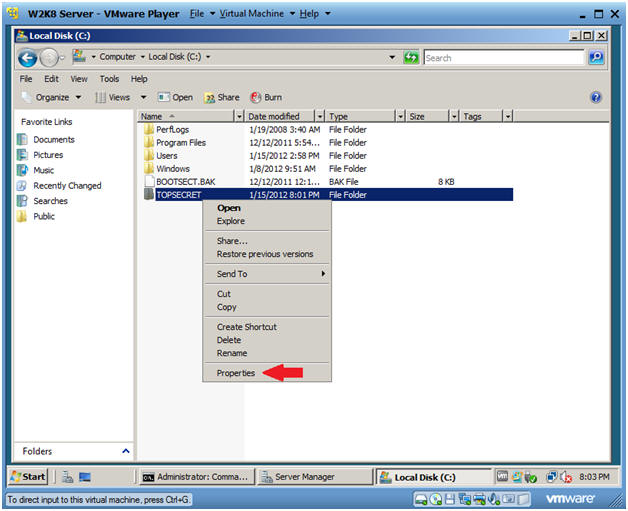
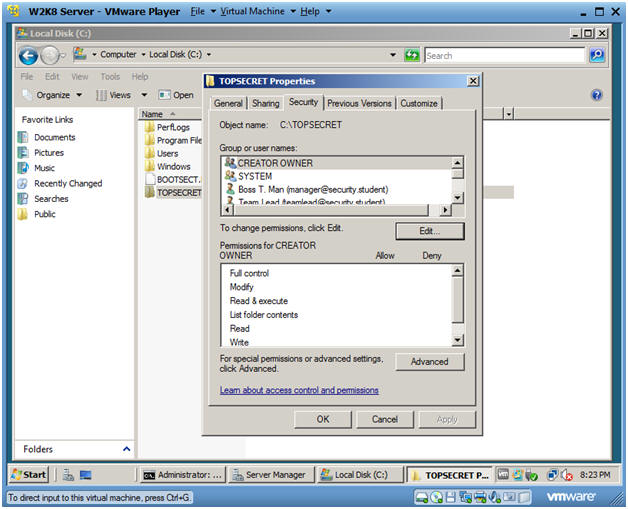
- Go to the properties of the "TOPSECRET" folder
- Instructions:
- Right Click on the TOPSECRET folder
- Select Properties
- Instructions:
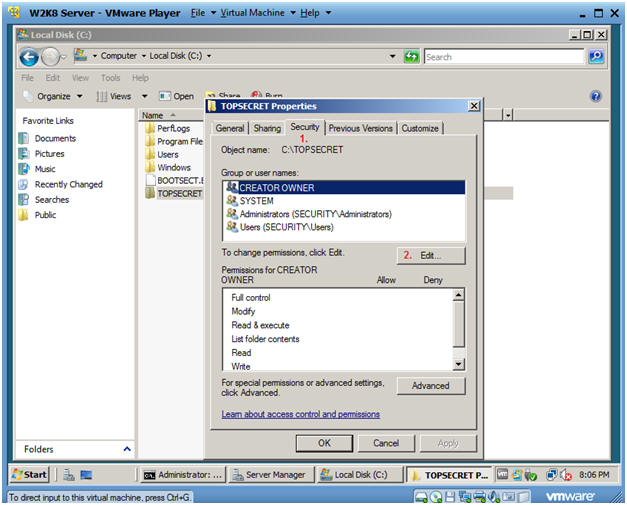
- Select the Security Tab.
- Instructions:
- Click on the Security Tab.
- Select the Edit... Button.
- Instructions:
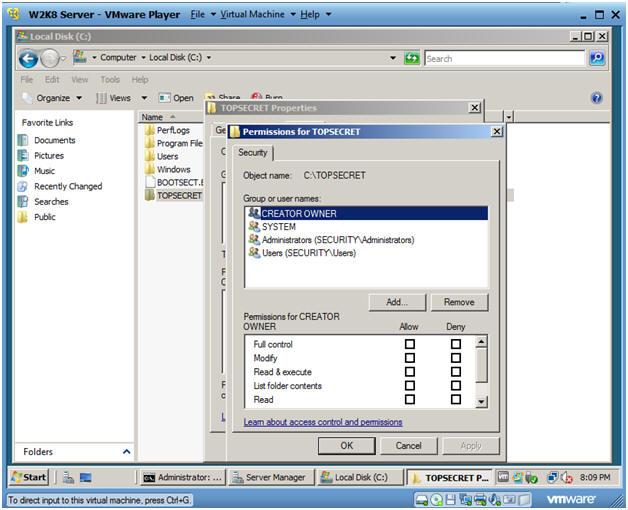
- Adding Users
- Instructions:
- Click the Add... Button
- Instructions:
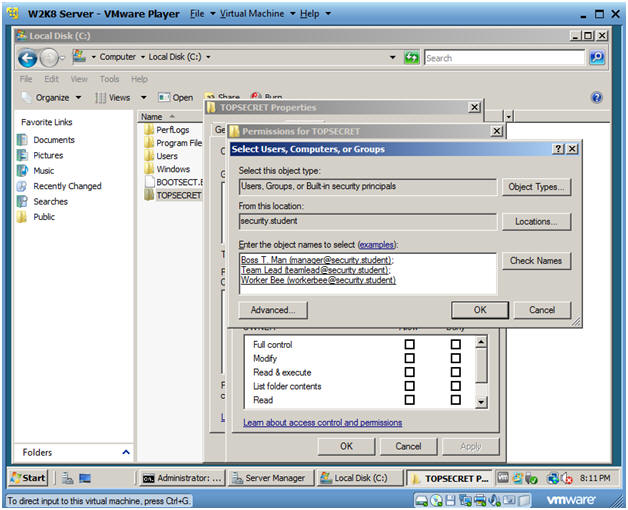
- Add Users Directory
- Instructions:
- In the Text Box type "Boss" and Click the Check Names Button.
- In the Text Box type "Team" and Click the Check Names Button.
- In the Text Box type "Worker" and Click the Check Names Button.
- Click OK
- Instructions:
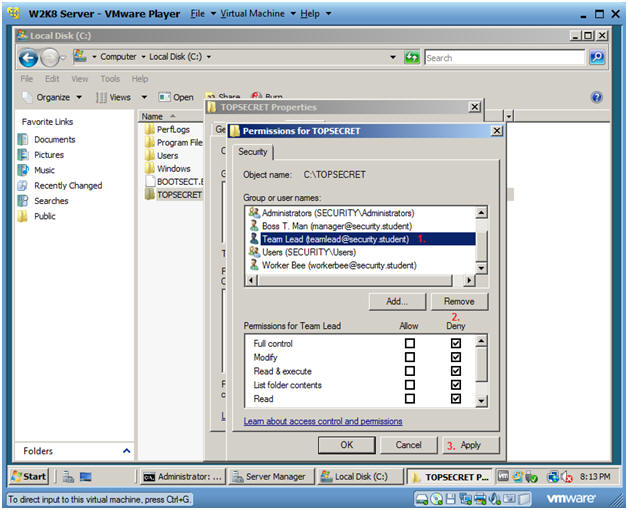
- Remove the Team Lead's permissions
- Instructions:
- Click on Team Leader (teamlead@security.student)
- Under the Deny Column, Click on Full Control
- Click Apply
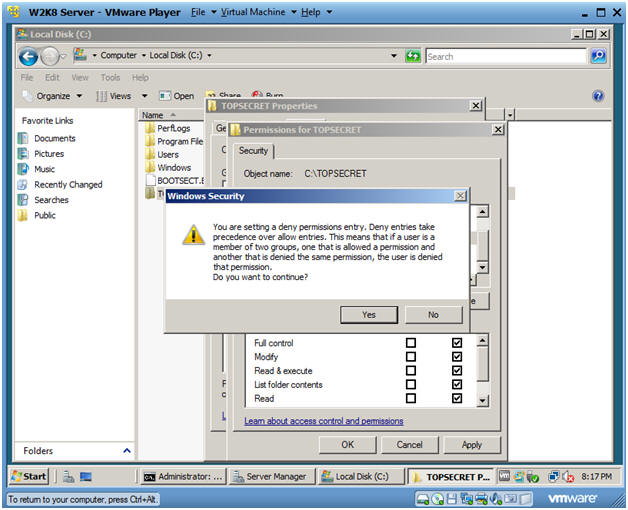
- Instructions:
- Confirm Windows Security Warning
- Instructions:
- Click Yes Button
- Instructions:
- Remove the Team Lead's permissions
- Instructions:
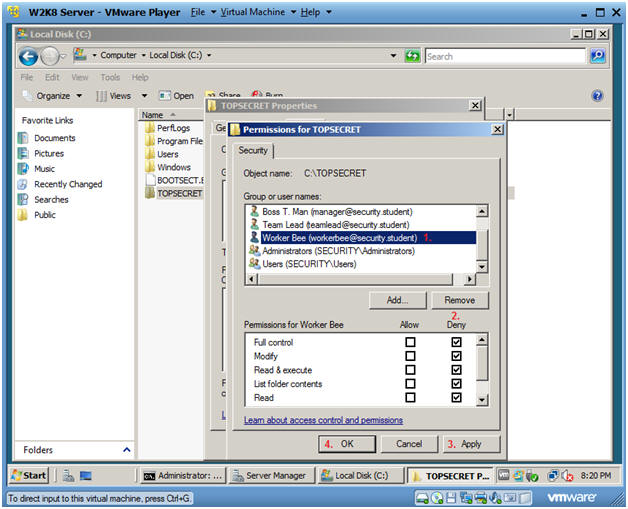
- Click on Worker Bee (workerbee@security.student)
- Under the Deny Column, Click on Full Control
- Click Apply
- Click OK
- Instructions:
- Remove the Team Lead's permissions
- Instructions:
- Click OK
- Instructions:
- Remove the Team Lead's permissions
- Instructions:
- Start --> Command Prompt
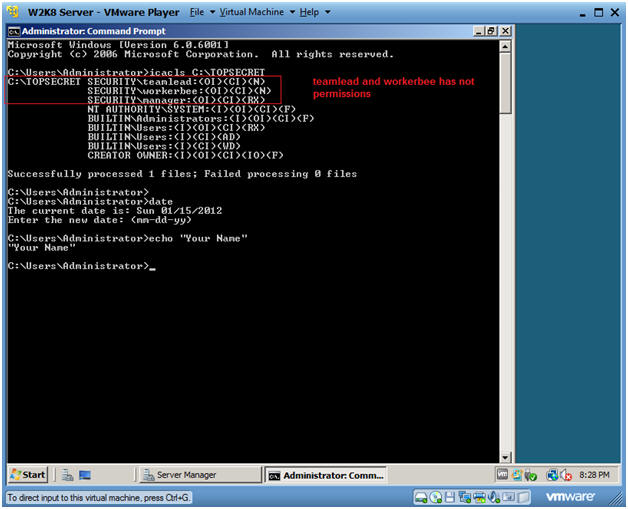
- icacls C:\TOPSECRET
- date
- echo "Your Name"
- Replace "Your Name" with your actual name.
- e.g., echo "John Gray"
-
Proof of Lab
Instructions:
- Do a PrtScn
- Paste into a word document
- Upload to Moodle.
- Note:
- Users teamlead and worker both have lines that end with (N), which mean no permissions.
- User manager's line end with "(RX)" which mean Read, Execute and list folder content Permissions.
- Instructions:
| Section 3. Testing out the ACL |
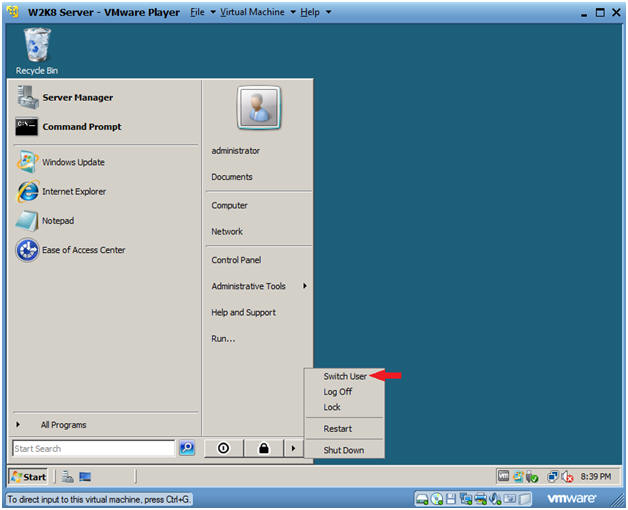
- Switch User
- Instructions:
- Start --> Switch User
- Instructions:
- Log On
- Instructions:
- Virtual Machine --> Send Ctrl+Alt+Del
- Instructions:
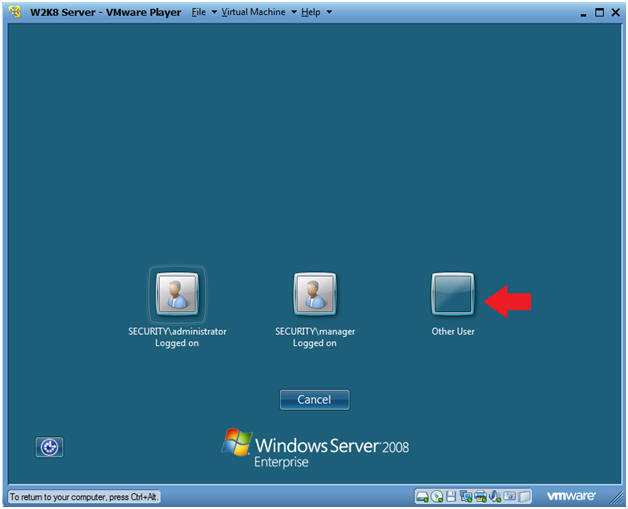
- Select Other User
- Instructions:
- Click on the Other User icon.
- Instructions:
- Select Other User
- Instructions:
- Login as teamlead
- The Password is the standard classroom password.
- Click the Blue Arrow next to the password box.
- Instructions:
- Bring up Computer (a.k.a., Windows Explorer)
- Instructions:
- Start --> Computer
- Instructions:
- Select the C: Drive
- Instructions:
- Double Click on "Local Disk (C:)"
- Instructions:
- Select the C: Drive
- Instructions:
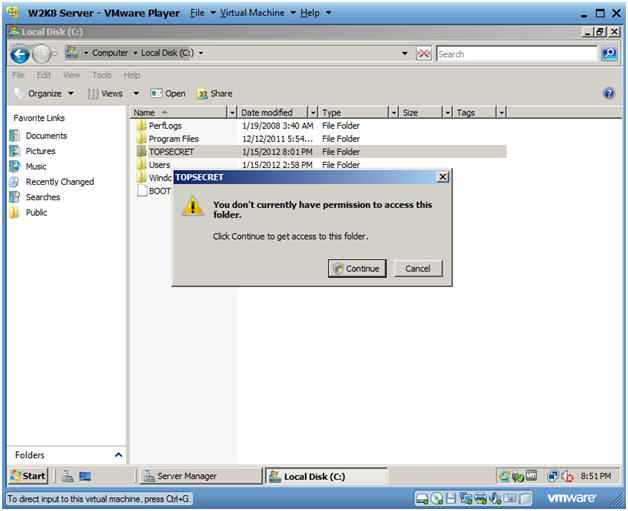
- Double Click on the TOPSECRET folder
- Note:
- You should see a message saying you do not have permission to access this folder.
- Instructions:
- Select the C: Drive
- Instructions:
- Start --> Command Prompt
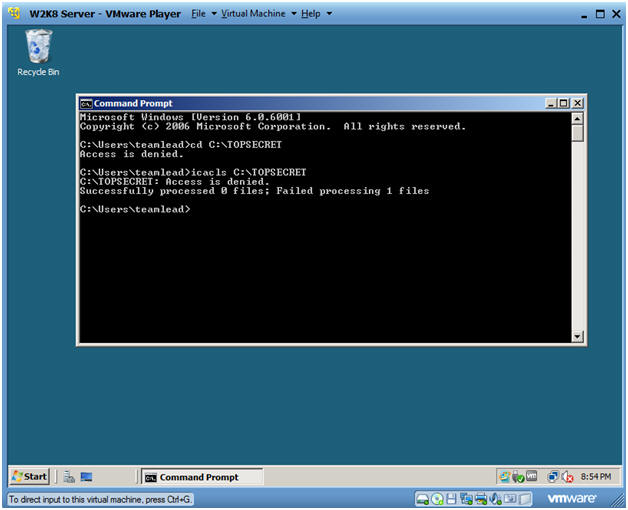
- cd C:\TOPSECRET
- icacls C:\TOPSECRET
- Note:
- This is the DOS view of access being denied to both the change directory and icacls commands.
- Instructions:
| Section 6. Proof of Lab |
- Complete Section 2, Step 13.Start Up the Command Prompt